Locky virus is one more dangerous ransomware that locks personal files of computer users and asks them to pay a ransom if they want to retrieve their files. This ransomware changes the names of the encrypted files to a unique 16-character combination of letters and digits and adds the .locky file extension. According to the program, to unlock the files, you need the decryption code, which you can get if you pay the ransom. The program uses RSA-2048 (thus, it is sometimes named as RSA-2048 virus) and AES-1024 algorithms to encrypt files.
Locky Virus quicklinks
- The Many Versions of Locky
- Main Features of Locky Virus
- How To Restore Files Locked by Locky
- Locky Virus Updates
- How To Prevent Locky Virus
- Automatic Malware removal tools
- How to recover Locky virus encrypted files and remove the virus
- Step 1. Restore system into last known good state using system restore
- 1. Reboot your computer to Safe Mode with Command Prompt:
- 2.Restore System files and settings.
- Step 4. Use Data Recovery programs to recover Locky virus encrypted files

(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
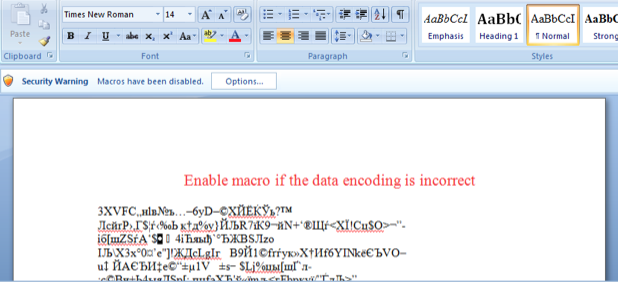
Even though there are several ways of distributing this infection, the most popular one is via infected e-mails. First of all, you will receive an e-mail to your inbox, attached a Word document. If you open the document, all you can see is just random gibberish and the advice to “Enable macro if the data encoding is incorrect”. Hackers want you to enable the macros so the code that is in the .doc document could run and infect your computer. It will automatically save the virus on your PC. Once this has been done, the saved file will serve as a downloader to get the needed pieces for the successful completion of the infection. Eventually, your files will be encrypted by the .locky extension ransomware.
Probably the worst feature of Locky is that it paved the way for other ransomware infections. Since it was almost unprecedentedly successful and dangerous, we have a lot of other ransomware viruses like GandCrab (3 versions of the virus), Cryptolocker or Petya. In fact, the threat isn’t going away any time soon and the largest-scale attacks have managed to cripple city services, health care facilities, newspapers, other businesses. Ransomware has become more aggressive than ever before.
The Many Versions of Locky
The success and relatively high infection rate of original locky virus inspired other cyber criminals to create ransomware viruses. They didn’t even bother to think of a new name that would be much different from locky or create some technological advancements, therefore a lot of them are very similar to each other. Also, most of them use the same .locky extension, thus same methods can be applied to decrypt locked files.
| Name | unique Features | Extension |
|---|---|---|
| Locky Imposter | Originates from Germany | .locky |
| ArmaLocky | Files destroyed after 72 hours | .armadilo1 |
| PowerLocky | Demands $500 in Bitcoins | .locky |
| StorageCrypter | Fixed price of 0.4 BTC | .locky |
| Jhash | Ransom note in Spanish, the ransom is only $10 | .locky |
| Asasin Ransomware | Fixed price of 0/25 BTC | .asasin |
| Lukitus Ransomware | Generates complicated extension with hexadecimal characters | .lukitus |
| syncCrypt Virus | Employs Military grande encryption, removes files after 48 hours | .kk |
| Diablo6 | Uses the same cryptgraphies as Locky | .diablo6 |
| ODIN ransomware | Fixed price of 0.5 BTC | .odin |
Main Features of Locky Virus
Locky can be easily called one of the most severe computer viruses of the past years, as a lot of hackers use various techniques to distribute it and infect more and more users. For instance, we have reported a situation where hackers sent 23 million emails with Locky virus or how they use MHT files to distribute Fareit Trojan and Locky ransomware.
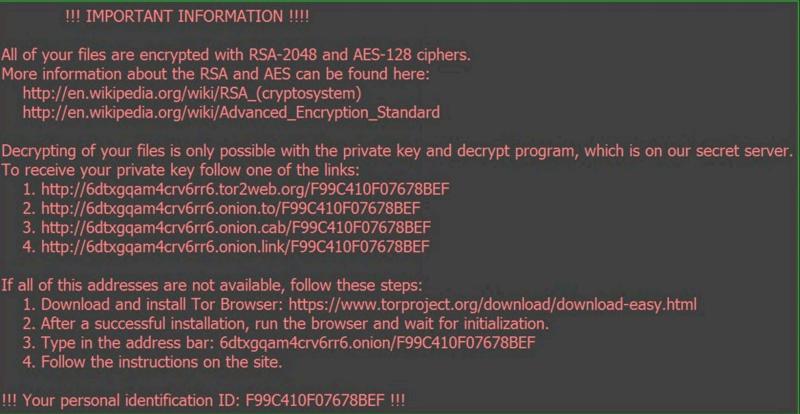
If your files have been locked by Locky Ransomware, your desktop wallpaper will be replaced with a message that says you must pay .5 BTC to get the decryption code. By the way, as stated by NakedSecurity, the price might go up to 1 BTC, which equals around $500. The program also creates a text file with the same message. Beware that this malware deletes the shadow volume copies of all the files, which makes it even more complicated to restore your files.
Original text from a Locky ransom note:
Locky ransomware
All of your files are encrypted with RSA-2048 and AES-128 ciphers. More information about the RSA and AES can be found here: https://en.wikipedia.org/wiki/RSA (crypto system) https://en.wikipedia.org/wiki/Advanced_Encryption_standard Decrypting of your files is only possible with the following steps How to buy decryption? 1. You can make a payment with BitCoins, there are many methods to get them. 2. You should register BitCoin wallet (simplest online wallet OR some other methods of creating wallet) 3. Purchasing BitCoins – Although it’s not yet easy to buy bitcoins, it’s getting simpler every day.
How To Restore Files Locked by Locky
If you have a backup of encrypted files, you have a solution to this problem. You can simply restore your files from this backup. If you do not, unfortunately, you may lose what Locky virus has locked. There are no guarantees that after making a payment you will get a code that works. If you pay, you may just give away some money to the cyber criminals.
Do not open attachments from unknown senders or you can get infected with Locky Ransomware. I recommend backing up important files using some cloud service. It is worth to mention that Locky virus employs difficult and aggressive distribution methods, as described in the blog entry by Symantec.
There are, in fact, 2 versions of the ransomware using .locky extension: the regular Locky virus and AutoLocky. The files encrypted by the latter ransomware can be decrypted using Emsisoft’s AutoLocky Decryptor. If your files have been encrypted by the regular Locky, your best choice is to recover the files from backups or to try to restore deleted files using Data Recovery software like Data Recovery PRO.
We also recommend getting the best antivirus protection and to install a professional anti-malware application, such as Spyhunter.
Locky Virus Updates
There is a copycat version of Locky Virus that is using a much simpler encryption scheme. Its corrupted files might be recovered by Emsisoft’s AutoLocky Decryptor. You can always give it a try if your files have .locky extension and other recovery methods have failed.
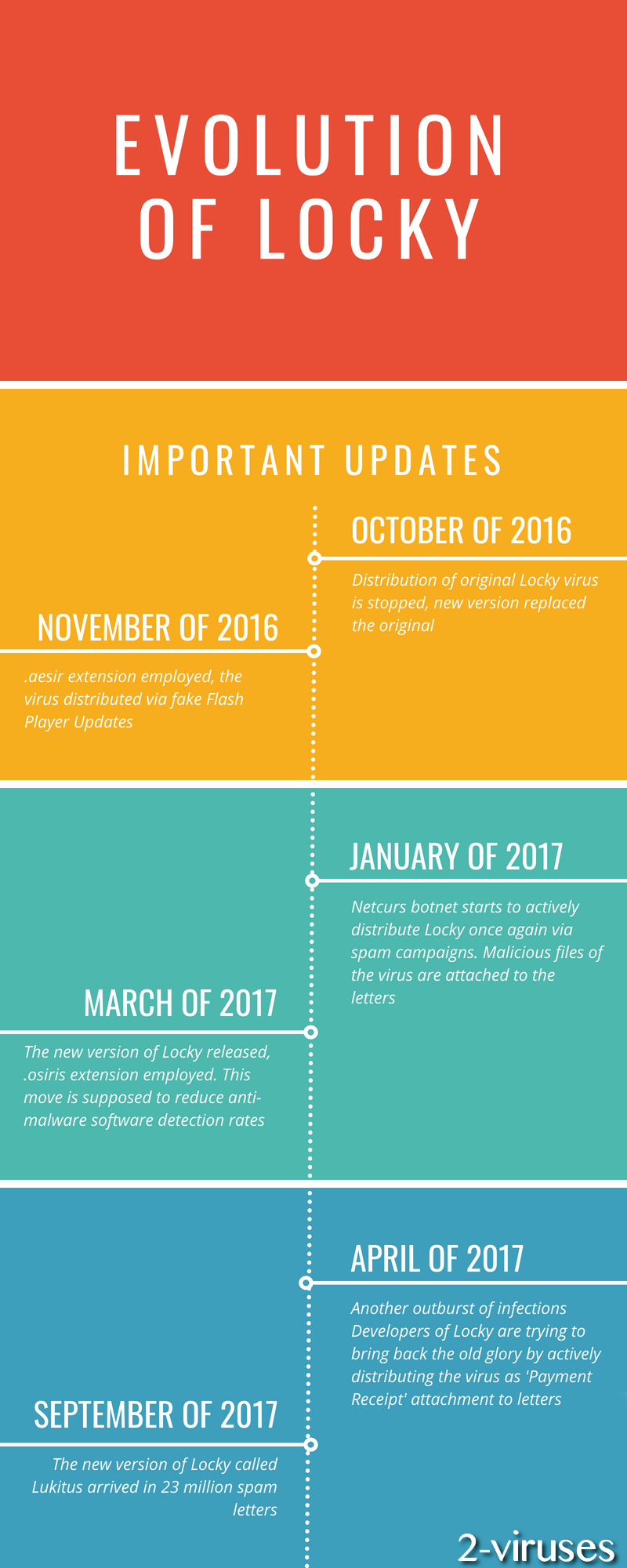
Update of October of 2016: Locky virus might have been a scary and widely-distributed infection, but now victims can get infected with it only accidentally as this variant is no longer actively spread. New ransomware released replace this older variant and are just as scary as this one.
Update of November the 17th, 2016: Locky ransomware has recently been distributed via fake Flash Player updates.
Update of the 21st of November, 2016: Locky crypto malware is now using .aesir extension to mark the encrypted files.
Update of the 5th of December, 2016. Now the files encrypted by Locky crypto-locker are appended with the .osiris extension. The extension is related with the spam e-mail attachments, which are Excel files and contain macro, which should be enabled. The files are named as Invoice_INV[random-numbers].xls. The ransom notes, left by this new variant are named as DesktopOSIRIS.bmp and DesktopOSIRIS.htm.
Update of the 20th of January, 2017. After being silent for some time, the virus returns to the playground. Its distributor, Netcurs botnet, has been noticed to initiate spam campaigns. They are not gigantic but are indeed active. Hackers elected .zip and .rar files to be appended to the malicious spam letters as attachments. Security researchers are guessing that this might be the beginning of a bigger spam campaign.
Update of the 23rd of January, 2017. Even though security researchers noticed some activity from Locky virus, the number of its attacks has significantly reduced.
Update of the 3rd of March, 2017. A new version of Locky virus has been detected and it is digitally signed for the sake of reducing the possibility of various anti-malware threats detecting the malware in a device. This sample also uses .osiris extension.
Update of the 27th of March, 2017. lucky does not seem to be doing very well. 2017 seems a little slow when it comes to the activity Locky. Currently, more persistent and obtrusive ransomware samples have been noticed, while Locky appears to be giving up its place of glory.
Update of the 24th of April, 2017. After almost being labeled as no longer active, Locky returns with a bang. It has adopted an old strategy for distribution. Hackers are spreading the payload of Locky in email letters. Their titles appear to be something like ‘Payment Receipt’. Usually, they will contain pdf files as attachments. Additionally, Recurs bonnet has been selected to distribute Locky as well.
Update of the 26th of June, 2017. Locky crypto-virus attempts to earn back its former glory but its attempt did not go as planned. Controllers of Locky ransomware decided to take down the Internet by storm and malicious payloads were being aggressively-delivered to random people. However, the authors forgot that newer versions of the Windows operating system have been designed to be more immune to such viruses. As a consequence, infection was limited to encoding files that are found in Windows XP or Vista devices.
Update of the 1st of September, 2017. The newest variant of Locky has been noticed to be delivered in a massive spam campaign. Lukitus crypto-virus arrived in 23 million deceptive email letters, sent on 28th of August.
Update of the 18th of September, 2017. A new extension of Locky ransomware was discovered today, called .ykcol. Some users infected with the virus of this extension might think that it is a Ykcol virus, due to the wrong information published by some websites. However, it is the same old Locky virus, only with a different extension.
How To Prevent Locky Virus
We have already mentioned that SpyHunter is a good tool that can effectively eliminate infections from Locky family. It has a real-time protection feature, so will be able to stop the virus on the go. Even if ransomware finds the way to enter your computer, this software won’t allow it to encrypt your files.
Automatic Malware removal tools
(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
How to recover Locky virus encrypted files and remove the virus
Step 1. Restore system into last known good state using system restore
1. Reboot your computer to Safe Mode with Command Prompt:
for Windows 7 / Vista/ XP
- Start → Shutdown → Restart → OK.
- Press F8 key repeatedly until Advanced Boot Options window appears.
- Choose Safe Mode with Command Prompt.

for Windows 8 / 10
- Press Power at Windows login screen. Then press and hold Shift key and click Restart.

- Choose Troubleshoot → Advanced Options → Startup Settings and click Restart.
- When it loads, select Enable Safe Mode with Command Prompt from the list of Startup Settings.

2.Restore System files and settings.
- When Command Prompt mode loads, enter cd restore and press Enter.
- Then enter rstrui.exe and press Enter again.

- Click “Next” in the windows that appeared.

- Select one of the Restore Points that are available before locky virus has infiltrated to your system and then click “Next”.

- To start System restore click “Yes”.

Step 2. Complete removal of Rsa-2048 virus
After restoring your system, it is recommended to scan your computer with an anti-malware program, like Spyhunter and remove all malicious files related to Locky Ransomware. You can check other tools here.Step 3. Restore .locky extension ransomware affected files using Shadow Volume Copies
If you do not use System Restore option on your operating system, there is a chance to use shadow copy snapshots. They store copies of your files that point of time when the system restore snapshot was created. Usually Locky malware tries to delete all possible Shadow Volume Copies, so this methods may not work on all computers. However, it may fail to do so. Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8. There are two ways to retrieve your files via Shadow Volume Copy. You can do it using native Windows Previous Versions or via Shadow Explorer. a) Native Windows Previous Versions Right-click on an encrypted file and select Properties → Previous versions tab. Now you will see all available copies of that particular file and the time when it was stored in a Shadow Volume Copy. Choose the version of the file you want to retrieve and click Copy if you want to save it to some directory of your own, or Restore if you want to replace existing, encrypted file. If you want to see the content of file first, just click Open.
b) Shadow Explorer It is a program that can be found online for free. You can download either a full or a portable version of Shadow Explorer. Open the program. On the left top corner select the drive where the file you are looking for is a stored. You will see all folders on that drive. To retrieve a whole folder, right-click on it and select “Export”. Then choose where you want it to be stored.

Step 4. Use Data Recovery programs to recover Locky virus encrypted files
There are several data recovery programs that might recover encrypted files as well. This does not work in all cases but you can try this:- We suggest using another PC and connect the infected hard drive as slave. It is still possible to do this on infected PC though.
- Download a data recovery program.
- Install and scan for recently deleted files.









Hello, how can I unlock encrypted files?
I’ve finally managed to recover my files. This is a crazy program!