Mr403Forbidden ransomware virus is a file-coder that encodes digital data by applying one of the cryptography techniques. The full name of the infection is EcryptRansombyMr403Forbidden and after analyzing one of the payloads, Inject.exe, we noticed that Alosia Team is indicated in the ‘comments’ section. Creators of this malware even indicate a ‘company name’ of Bandung BlackHat which is actually an existing group of hackers from Indonesia. The twitter account of these crooks has been silent since 2014; it might be possible that some other hackers are posing as members of Bandung BlackHat.
Good news – this sample is decryptable
Internet surfers should not fear this specific variant as file-encryption can be easily reversed. This infection was not an elaborate sample: therefore, security researchers did not take long to figure out that Stupid decrypter should be updated. This decryption-tool is applied to the files, encrypted by weaker crypto-viruses. Now, this application has been updated to overthrow the file-encryption Mr403Forbidden virus inflicted. Click here to download the tool.
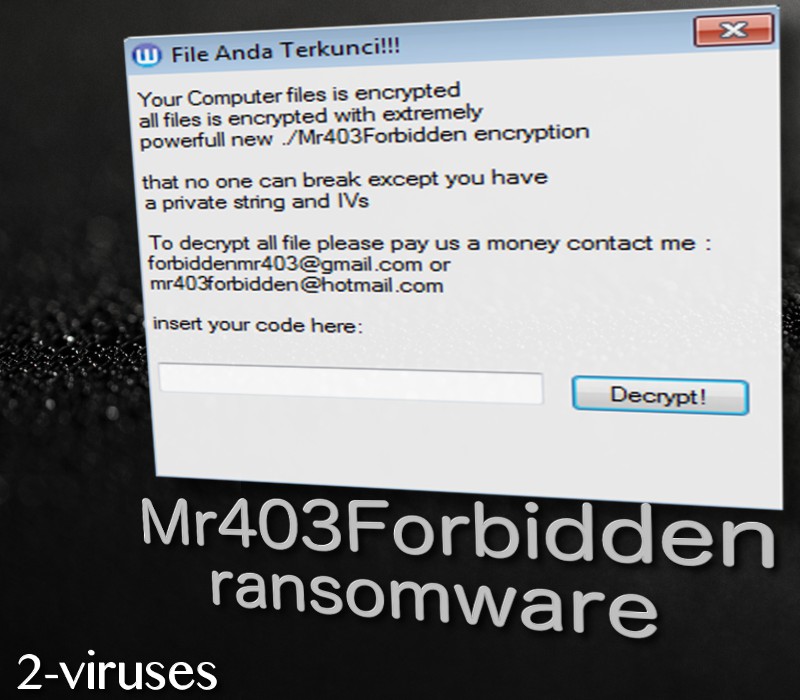
The window that gets loaded after files are encrypted features a title of “File anda terkunci” which is an Indonesian phrase for “Your file is locked”. However, the following text is written in the English language, making the crypto-virus more universal. .alosia extension is appended the encrypted executables. Victims are threatened that they can only recover their data after a specific amount of money will be paid. To find out more about the payment options, users are required to send email letters to [email protected] or [email protected].
However, if you have been having difficulties with malicious parasites, constantly affecting your operating system, you should protect your digital files from being harmed and made futile. This is when backup storages come in as the saviors of the day. Simply upload copies of your original files into the storage, or keep them in other locations that are more familiar, like USB flash drives. Nevertheless, we are to inform you about the keeping your USB plugged into the computer at all times is not a good idea. If a crypto-virus managed to get inside, newer versions will all presumably encode all data.
File Anda Terkunci!!!
Your Computer files is encrypted
all files with extremely
powerfull new ./Mr403Forbidden encryption
that no one can break except you have
a private string and IVs
To decrypt all file please pay us a money contact me :
[email protected] or
[email protected]
insert your code here:
[…]
[Decrypt!]
If there would not be a free file recovery option, we would discuss alternative methods. This includes restoration of Shadow Volume Copies or applying universal tools that have been generated for this purpose. Since there is a technique for file-recovery, we gladly encourage you to give it a go.
Remember: before you try to decrypt files with the Stupid Decrypter, you should eliminate the infection first. This should be done with an anti-malware tool you find the most fit. Spyhunter or Hitman are definitely some of the samples that will not dash hopes of a safer device.
We should also include possible techniques that crypto-viruses take advantage of. First of all, they might be, distributed in malicious spam campaigns. This refers to letters that have harmful attachments, like .doc files that contain damaging macros. In other cases, viruses can reach your device if you visit suspicious or vulnerable websites. Furthermore, flimsy remote desktop protocol is also one of the reasons for a ransomware infection to occur.
Lastly, whatever you do, do not contact the hackers via the email address they have included into the ransom window. This Mr403Forbidden virus is an Indonesian sample, but has been adjusted to target English speaking users just as well. The window, containing all of the information about this infection, has a button of “Decrypt”. If a code victims’ type in is incorrect, the infection will show “WRONG CODE NJING!!!” message.
Mr403forbidden Ransomware Virus quicklinks
- Good news – this sample is decryptable
- Automatic Malware removal tools
- How to recover Mr403Forbidden ransomware virus encrypted files and remove the virus
- Step 1. Restore system into last known good state using system restore
- 1. Reboot your computer to Safe Mode with Command Prompt:
- 2.Restore System files and settings.
- Step 4. Use Data Recovery programs to recover Mr403Forbidden ransomware virus encrypted files
Automatic Malware removal tools
(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
How to recover Mr403Forbidden ransomware virus encrypted files and remove the virus
Step 1. Restore system into last known good state using system restore
1. Reboot your computer to Safe Mode with Command Prompt:
for Windows 7 / Vista/ XP
- Start → Shutdown → Restart → OK.
- Press F8 key repeatedly until Advanced Boot Options window appears.
- Choose Safe Mode with Command Prompt.

for Windows 8 / 10
- Press Power at Windows login screen. Then press and hold Shift key and click Restart.

- Choose Troubleshoot → Advanced Options → Startup Settings and click Restart.
- When it loads, select Enable Safe Mode with Command Prompt from the list of Startup Settings.

2.Restore System files and settings.
- When Command Prompt mode loads, enter cd restore and press Enter.
- Then enter rstrui.exe and press Enter again.

- Click “Next” in the windows that appeared.

- Select one of the Restore Points that are available before Mr403Forbidden ransomware virus has infiltrated to your system and then click “Next”.

- To start System restore click “Yes”.

Step 2. Complete removal of Mr403Forbidden ransomware virus
After restoring your system, it is recommended to scan your computer with an anti-malware program, like Spyhunter and remove all malicious files related to Mr403Forbidden ransomware virus. You can check other tools here.Step 3. Restore Mr403Forbidden ransomware virus affected files using Shadow Volume Copies
If you do not use System Restore option on your operating system, there is a chance to use shadow copy snapshots. They store copies of your files that point of time when the system restore snapshot was created. Usually Mr403Forbidden ransomware virus tries to delete all possible Shadow Volume Copies, so this methods may not work on all computers. However, it may fail to do so. Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8. There are two ways to retrieve your files via Shadow Volume Copy. You can do it using native Windows Previous Versions or via Shadow Explorer. a) Native Windows Previous Versions Right-click on an encrypted file and select Properties → Previous versions tab. Now you will see all available copies of that particular file and the time when it was stored in a Shadow Volume Copy. Choose the version of the file you want to retrieve and click Copy if you want to save it to some directory of your own, or Restore if you want to replace existing, encrypted file. If you want to see the content of file first, just click Open.
b) Shadow Explorer It is a program that can be found online for free. You can download either a full or a portable version of Shadow Explorer. Open the program. On the left top corner select the drive where the file you are looking for is a stored. You will see all folders on that drive. To retrieve a whole folder, right-click on it and select “Export”. Then choose where you want it to be stored.

Step 4. Use Data Recovery programs to recover Mr403Forbidden ransomware virus encrypted files
There are several data recovery programs that might recover encrypted files as well. This does not work in all cases but you can try this:- We suggest using another PC and connect the infected hard drive as slave. It is still possible to do this on infected PC though.
- Download a data recovery program.
- Install and scan for recently deleted files.








