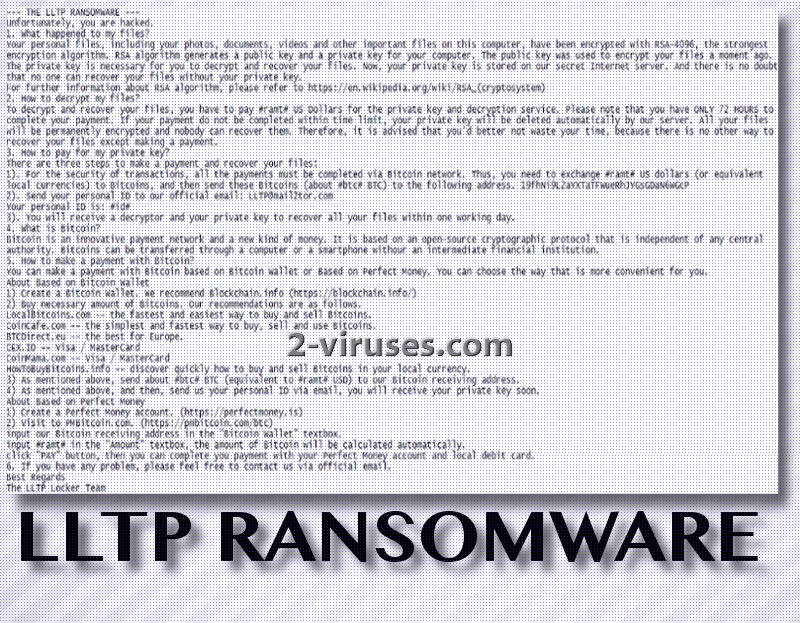
LLTP (Locker) crypto-virus is classified among ransomware samples that use a combination of ciphers to complicate the decryption process for its victims. An AES algorithm is first applied to ruin data with the public encryption key, while the private key is encrypted with a RSA cryptography. After these are processes are concluded, users’ data is no longer usable. In the ransom note, hackers refer to themselves as the LLTP Locker Team and request that all payments would be made via an anonymous system: bitcoin. [email protected] email address is the one that victims can write to if they face difficulties while sending the required payment. The email will also be necessary to contact after the ransom has been successfully sent to 19fhNi9L2aYXTaTFWueRhJYGsGDaN6WGcP bitcoin wallet. A period of 72 hours is given for people to arrange their thoughts and decide whether paying the ransom is worth it. Even though hackers claim to permanently delete private decryption key after the given time passes, we still do not feel like paying the fee is the best option.
Procedures that LLTP ransomware initiates
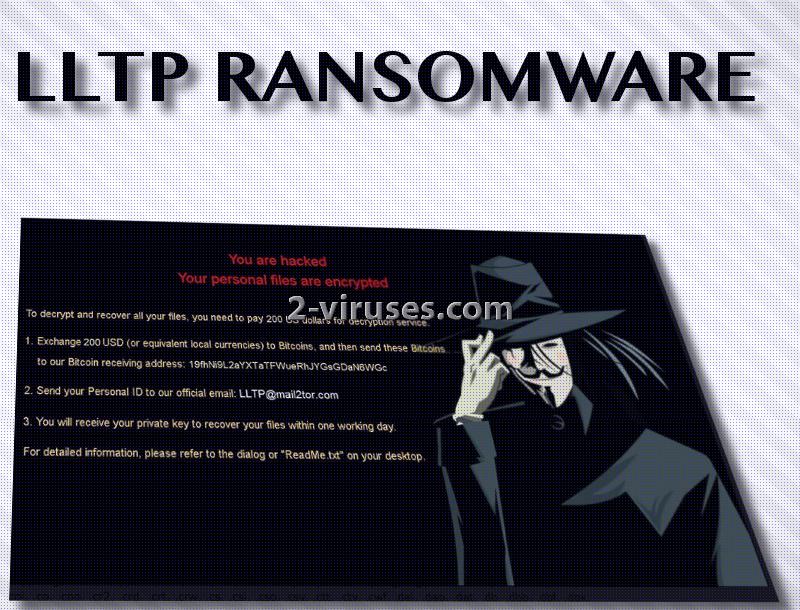
LLTP crypto-virus appears to have a few things in common with TrumpLocker and VenusLocker infections. Their screen-locker features the same picture with a cartoon version of a dark silhouette, wearing an iconic anonymous mask. It appears this ransomware won’t be influenced by the fact that there might be no Internet connection in the infected device.
File-encrypting can be initiated in an offline mode as well. Moniestealer.co.nf domain appears to be the one that LLTP virus is programmed to contact and provide certain details about the infected victim. As a response, hackers will not hesitate to send a public key for encryption. However, for this scenario to play out, device has to be connected to Internet. If not, the LLTP ransomware will still succeed in initiating encryption.
The ransomware will create new folders and subfolders to store malicious executables and to places all encrypted data in a location called ‘vault’. It also generates a RAR archive but the purpose for this file is yet undetermined. While dealing with its affairs, LLTP virus will start a command to delete all Shadow Volume Copies since this feature can help people restore files completely for free. Ransom notes are called ReadMe.txt ad LEAME.txt.
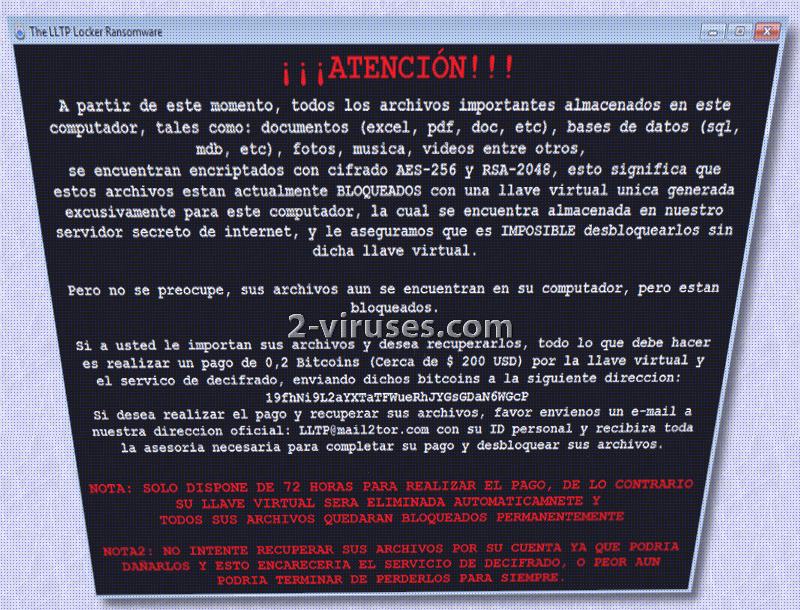
There are also a Spanish version of the ransom note, meaning that it attempts to infect not only English-speaking users. The encrypted data is appended with a long, unique extension: .ENCRYPTED_BY_LLTP. It is after a number of different files, which means, that it won’t have any issues in finding which executables to encrypt with AES-256.
How can I restore my files? LLTP ransomware has ruined them
If you are asking us this question, we cannot give you the best news. Decryption is still vague, but we hope that you won’ be tempted to pay the ransom that hackers demand. Presumably, they will require about 0.2 Bitcoins that are approximately 203.66 US dollars. If you are concerned whether creating file-recovery tools is an issue, you should remember that there are a number of tools already. You can try decrypting your files with any of them: it might be that they will function. However, since LLTP ransomware threatens to permanently destroy files, you should copy all of the encoded data in a safe location (USB flash drive or something different). Then, remove the infection. This task can be done either manually or automatically. Spyhunter or Hitman will assist you in the automatic removal. For the possible decryption options, you should read this whole article.
Distribution of LLTP ransomware
Hackers will spread LLTP ransomware in a couple of ways. First, it will send spam campaigns that will offer to download attachments, which are going to be payloads of an infection. You should not open random messages I your inbox and try to keep your device clean from unknown files. In addition to that, reacting to deceptive advertisements and visiting questionable websites can also easily result in an infection with malware. If you wish to have a more secure browsing, we advise you to be a client of legitimate domains and services.
Lltp Ransomware quicklinks
- Procedures that LLTP ransomware initiates
- How can I restore my files? LLTP ransomware has ruined them
- Distribution of LLTP ransomware
- Automatic Malware removal tools
- How to recover LLTP ransomware encrypted files and remove the virus
- Step 1. Restore system into last known good state using system restore
- 1. Reboot your computer to Safe Mode with Command Prompt:
- 2.Restore System files and settings.
- Step 4. Use Data Recovery programs to recover LLTP ransomware encrypted files
Automatic Malware removal tools
(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
How to recover LLTP ransomware encrypted files and remove the virus
Step 1. Restore system into last known good state using system restore
1. Reboot your computer to Safe Mode with Command Prompt:
for Windows 7 / Vista/ XP
- Start → Shutdown → Restart → OK.
- Press F8 key repeatedly until Advanced Boot Options window appears.
- Choose Safe Mode with Command Prompt.

for Windows 8 / 10
- Press Power at Windows login screen. Then press and hold Shift key and click Restart.

- Choose Troubleshoot → Advanced Options → Startup Settings and click Restart.
- When it loads, select Enable Safe Mode with Command Prompt from the list of Startup Settings.

2.Restore System files and settings.
- When Command Prompt mode loads, enter cd restore and press Enter.
- Then enter rstrui.exe and press Enter again.

- Click “Next” in the windows that appeared.

- Select one of the Restore Points that are available before LLTP virus has infiltrated to your system and then click “Next”.

- To start System restore click “Yes”.

Step 2. Complete removal of LLTP Locker ransomware
After restoring your system, it is recommended to scan your computer with an anti-malware program, like Spyhunter and remove all malicious files related to LLTP ransomware. You can check other tools here.Step 3. Restore LLTP virus affected files using Shadow Volume Copies
If you do not use System Restore option on your operating system, there is a chance to use shadow copy snapshots. They store copies of your files that point of time when the system restore snapshot was created. Usually LLTP Locker ransomware tries to delete all possible Shadow Volume Copies, so this methods may not work on all computers. However, it may fail to do so. Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8. There are two ways to retrieve your files via Shadow Volume Copy. You can do it using native Windows Previous Versions or via Shadow Explorer. a) Native Windows Previous Versions Right-click on an encrypted file and select Properties → Previous versions tab. Now you will see all available copies of that particular file and the time when it was stored in a Shadow Volume Copy. Choose the version of the file you want to retrieve and click Copy if you want to save it to some directory of your own, or Restore if you want to replace existing, encrypted file. If you want to see the content of file first, just click Open.
b) Shadow Explorer It is a program that can be found online for free. You can download either a full or a portable version of Shadow Explorer. Open the program. On the left top corner select the drive where the file you are looking for is a stored. You will see all folders on that drive. To retrieve a whole folder, right-click on it and select “Export”. Then choose where you want it to be stored.

Step 4. Use Data Recovery programs to recover LLTP ransomware encrypted files
There are several data recovery programs that might recover encrypted files as well. This does not work in all cases but you can try this:- We suggest using another PC and connect the infected hard drive as slave. It is still possible to do this on infected PC though.
- Download a data recovery program.
- Install and scan for recently deleted files.








