Dedicated 2-viruses.com

How to fix Google Redirect Virus problem
Google redirect virus is a browser hijacker targeting google and other search engine search results and redirecting user to infected pages. These pages can be porn–related or full of advertising banners that make creators of this parasite money. Also, these pages might force you to pay something or give away your bank account details. Thus … Continued
We are dedicated to the cause of fighting malware on the largest battlefield in the world: the Internet. We are ready to face the challenge of making the internet a safe place, so that everyone could effectively exercise their right to browse the Internet without fear of suffering an identity theft, carding or an attack of a thousand pop-ups from outer space.
Our mission is to provide you with removal instructions for most of the dangerous malware that threatens Your internet freedom.
Latest parasites

ExtendedSprint Adware
Adware
Diavol/lock64 Ransomware
Ransomware
Verti-search.com Redirects
Browser Hijacker
M.startbrowser.co Redirects
Browser Hijacker
Searchsymphony.com Redirects
Browser Hijacker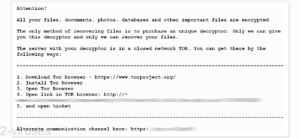
BitRansomware File Locker
Ransomware
Gamesearchtab.com Hijacker
Browser Hijacker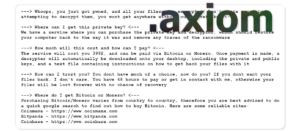
Axiom Wiper Ransomware
Ransomware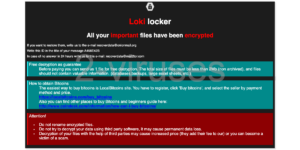
Loki Locker Ransomware
Ransomware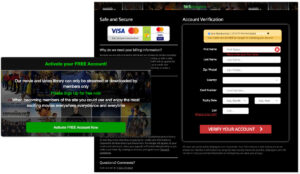



Recent Comments