It is easy to assume that WinRarer virus won’t inflict encryption on its victims. The main goal of this recently emerged variant is to gather files in one archive and lock it with a complexed password. Or is it? In fact, creators of this infection probably feel that putting files in a secured archive is not enough. To make their creation even more scary, they made WinRarer encode data with AES-128 cipher before placing it in a common resting place. We can assure our readers that guessing the correct code won’t be a possibility since the creators of ransomware are rarely sloppy. Usually, passwords that are selected by crooks are complicated, containing numbers, letters and other signs that make it impossible to simply crack it. Locked files are going to be placed in an archive with .ace extension. WinRarer virus has come to the fore as a ransomware virus and should be treated as one. After the infection has slithered into your operated device and locked your files in an archive, it is going to randomly drop ransom notes as .htm and .jpg files. The opened notes will contain instructions for further actions. As it turns out, WinRarer virus is one of those infections that urge people to download TOR browser which often serves the needs of shady programmers. Furthermore, similarly to other viruses, this one will also be interested in locking your screen and displaying an image with instructions.
About WinRarer Virus
WinRarer virus is placed in a category of ransomware because of its aims and objectives. The payload of this variant is expected to be downloaded by poor Internet users. Then, the reign of a virus can begin. At first, activity of the payload is usually subtle and does not attract attention. Nevertheless, the necessary operations are carried out under your nose. Modifications to your Windows Registry Keys and scanning for files to encrypt and lock are going to happen all around you, while your focus is distracted by other aspects of life. WinRarer virus will manage to keep its existence a secret until there is no way to reverse the damage that has been done.
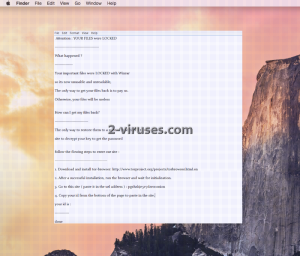
Once AES-128 encryption cipher has influenced your data and the payload has placed all of the encoded files in one locked archive, there won’ be much you can do without help from trustworthy security researchers. Since this powerful variant not only encrypts data but also locks it in .ace file, the retrieval of files are going to require efforts. See the following imagery to see examples of the lockscreen and the ransom note. This will give you an idea of what infected victims see.
How is WinRarer Virus Distributed?
The payload of WinRarer ransomware is probably dropped in places that are infamous for exposing users to potentially harmful content. Even though you might not expect that your email inbox is one of those places, received letters are often not what they seem. Many messages that originate from authorities are fabricated and sent around for one purpose only: spreading payloads of ransomware viruses. Before opening letters or downloading attachments from them, always be certain of the reliability of the sender. If the transmitter’s email address looks unfamiliar, then delete it.
How to Decrypt Files Encrypted by WinRarer Virus?
Contacting cyber criminals that have crafted WinRarer ransomware is not an action that you should be doing. Instead, focus on other alternatives that could help you to get back your files. The instructions that are left behind by this virus are specifically advising people to download TOR browser and visit a provided website. In the domain, victims can use their ID number and find out the exact sum of money that is required for decryption. The fee is not necessarily relevant since you should not pay it even if it is small. Surprisingly, the creators WinRarer virus invite others to start their own ransomware project. We strongly discourage you from thinking about this as such actions would make you nothing more than a cyber criminal. If you happen to be infected with this variant and wish to be assisted, leave a comment below and our group is going to get back to you shortly. You should also bear in mind that ransomware viruses should be eliminated. If you are worried about the encrypted data, make a copy of the locked archive (in case the payload is programmed to delete the encrypted files). Spyhunter or Hitman can help you with the task of removal.
Winrarer Virus quicklinks
- About WinRarer Virus
- How is WinRarer Virus Distributed?
- How to Decrypt Files Encrypted by WinRarer Virus?
- Automatic Malware removal tools
- How to recover WinRarer virus encrypted files and remove the virus
- Step 1. Restore system into last known good state using system restore
- 1. Reboot your computer to Safe Mode with Command Prompt:
- 2.Restore System files and settings.
- Step 4. Use Data Recovery programs to recover WinRarer virus encrypted files

Automatic Malware removal tools
(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
How to recover WinRarer virus encrypted files and remove the virus
Step 1. Restore system into last known good state using system restore
1. Reboot your computer to Safe Mode with Command Prompt:
for Windows 7 / Vista/ XP
- Start → Shutdown → Restart → OK.
- Press F8 key repeatedly until Advanced Boot Options window appears.
- Choose Safe Mode with Command Prompt.

for Windows 8 / 10
- Press Power at Windows login screen. Then press and hold Shift key and click Restart.

- Choose Troubleshoot → Advanced Options → Startup Settings and click Restart.
- When it loads, select Enable Safe Mode with Command Prompt from the list of Startup Settings.

2.Restore System files and settings.
- When Command Prompt mode loads, enter cd restore and press Enter.
- Then enter rstrui.exe and press Enter again.

- Click “Next” in the windows that appeared.

- Select one of the Restore Points that are available before WinRarer virus has infiltrated to your system and then click “Next”.

- To start System restore click “Yes”.

Step 2. Complete removal of WinRarer virus
After restoring your system, it is recommended to scan your computer with an anti-malware program, like Spyhunter and remove all malicious files related to WinRarer virus. You can check other tools here.Step 3. Restore WinRarer virus affected files using Shadow Volume Copies
If you do not use System Restore option on your operating system, there is a chance to use shadow copy snapshots. They store copies of your files that point of time when the system restore snapshot was created. Usually WinRarer virus tries to delete all possible Shadow Volume Copies, so this methods may not work on all computers. However, it may fail to do so. Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8. There are two ways to retrieve your files via Shadow Volume Copy. You can do it using native Windows Previous Versions or via Shadow Explorer. a) Native Windows Previous Versions Right-click on an encrypted file and select Properties → Previous versions tab. Now you will see all available copies of that particular file and the time when it was stored in a Shadow Volume Copy. Choose the version of the file you want to retrieve and click Copy if you want to save it to some directory of your own, or Restore if you want to replace existing, encrypted file. If you want to see the content of file first, just click Open.
b) Shadow Explorer It is a program that can be found online for free. You can download either a full or a portable version of Shadow Explorer. Open the program. On the left top corner select the drive where the file you are looking for is a stored. You will see all folders on that drive. To retrieve a whole folder, right-click on it and select “Export”. Then choose where you want it to be stored.

Step 4. Use Data Recovery programs to recover WinRarer virus encrypted files
There are several data recovery programs that might recover encrypted files as well. This does not work in all cases but you can try this:- We suggest using another PC and connect the infected hard drive as slave. It is still possible to do this on infected PC though.
- Download a data recovery program.
- Install and scan for recently deleted files.