Trojan-Syria, full title Wana Decrypt0r Trojan-Syria Editi0n, is a ransomware virus that should be in charge of file encryption, supported by AES algorithm. Despite the fact that this functionality is on the table, and the structure of the virus suggest that such a process could be regulated, the first detected sample did not accomplish the encoding-procedure. Therefore, it was expected that the fully prepped attack will take place sometime in the future. As expected, the second variant is a more polished version and already encrypts files. The infection itself is based on the Hidden Tear open source project: new variants seem to never end.
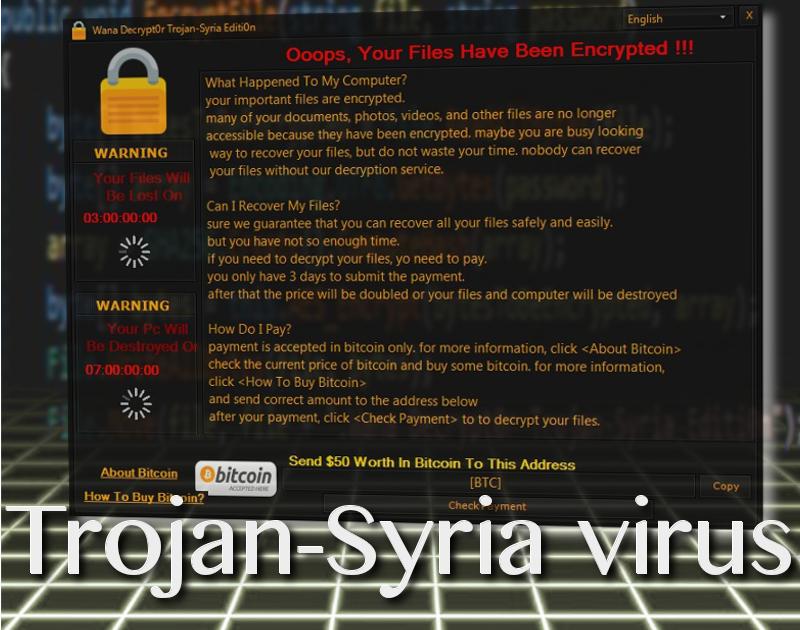
Exactly two samples have been detected of this infection, Wana Decrypt0r Trojan-Syria Editi0n.exe is the culprit that commences harmful activity. However, since it did not really encrypt files, every threat in the ransom note was empty. Even though this virus was bluffing, victims might have not know that. Demands for ransom were displayed in a screen-locker, announcing that a ransomware infection has managed to encode users’ data.
The lock-screen displays two countdowns. Both of them keep track of whether the fee has been paid. It is explained that if victims do not submit the necessary payment, all of their files will be lost. The second clock makes an even more ridiculous statement: after 7 days, PC will be destroyed. While the primary version did not encrypt files, these threats did not mean anything. Now, you should be careful and follow security researchers’ advises.
The ransom note also contains a bunch of grammatical and spelling errors, meaning that the creator of this variant is not a native English-speaking individual. The infection dares to demand 50 US dollars. In the bitcoin payment system, this translates into 0.01905 BTC. However, we hope that victims of this infection will aim to find help in time, before they submit the transaction and lose their money.
How to recover data and defeat the infection?
As encoding of files is commenced and concluded, you should be careful not to accidentally trigger file-deletion. The first detected version was expected to append .Wana Decrypt0r Trojan-Syria Editi0n extension to the locked files, but the authors probably decided to go with a shorter one at the end: .wannacry. It is no wonder that this crypto-virus imposes to be the notorious WannaCry. In total, 29 filetypes are being targeted to become no longer useable.
To carefully proceed with the removal of this ransomware and the decryption of ruined files, you must follow specific guidelines. Scroll down to find instructions that could help you with both of the procedures. Instead of repeating steps for the elimination of ransomware, you could simply run a full security scan with Spyhunter or Malwarebytes. These pieces of software will help you clean your computer from dangerous computer viruses. Before you could use them, you should start your device in a SafeMode (how-to is found bellow as well).
Many users wish to become immune to ransomware infections. In many cases, this is possible if people make the right call to store their valuable digital information in more than one location. For instance, use backup storages, USB flash drives or whichever option that seems the most convenient. If you have your data in multiple locations, them losing files in one of them won’t be as tragic. Remember to retrieve files ONLY after the ransomware is removed.
This crypto-virus does not use a sole strategy for distribution: it could use multiple ones. For instance, the malicious payload could be delivered via spam, social networking sites or installed automatically after an infectious website has been visited. These are the most trendy techniques for malware distribution, and ransomware is one of the nastiest of them all. Make sure to be cautious as many other crypto-viruses are waiting for a moment to strike.
Trojan Syria Virus quicklinks
- How to recover data and defeat the infection?
- Automatic Malware removal tools
- How to recover Trojan-Syria virus encrypted files and remove the virus
- Step 1. Restore system into last known good state using system restore
- 1. Reboot your computer to Safe Mode with Command Prompt:
- 2.Restore System files and settings.
- Step 4. Use Data Recovery programs to recover Trojan-Syria virus encrypted files
Automatic Malware removal tools
(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
How to recover Trojan-Syria virus encrypted files and remove the virus
Step 1. Restore system into last known good state using system restore
1. Reboot your computer to Safe Mode with Command Prompt:
for Windows 7 / Vista/ XP
- Start → Shutdown → Restart → OK.
- Press F8 key repeatedly until Advanced Boot Options window appears.
- Choose Safe Mode with Command Prompt.

for Windows 8 / 10
- Press Power at Windows login screen. Then press and hold Shift key and click Restart.

- Choose Troubleshoot → Advanced Options → Startup Settings and click Restart.
- When it loads, select Enable Safe Mode with Command Prompt from the list of Startup Settings.

2.Restore System files and settings.
- When Command Prompt mode loads, enter cd restore and press Enter.
- Then enter rstrui.exe and press Enter again.

- Click “Next” in the windows that appeared.

- Select one of the Restore Points that are available before Wana Decrypt0r Trojan-Syria Editi0n virus has infiltrated to your system and then click “Next”.

- To start System restore click “Yes”.

Step 2. Complete removal of Trojan-Syria virus
After restoring your system, it is recommended to scan your computer with an anti-malware program, like Spyhunter and remove all malicious files related to Wana Decrypt0r Trojan-Syria Editi0n virus. You can check other tools here.Step 3. Restore Trojan-Syria virus affected files using Shadow Volume Copies
If you do not use System Restore option on your operating system, there is a chance to use shadow copy snapshots. They store copies of your files that point of time when the system restore snapshot was created. Usually Wana Decrypt0r Trojan-Syria Editi0n virus tries to delete all possible Shadow Volume Copies, so this methods may not work on all computers. However, it may fail to do so. Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8. There are two ways to retrieve your files via Shadow Volume Copy. You can do it using native Windows Previous Versions or via Shadow Explorer. a) Native Windows Previous Versions Right-click on an encrypted file and select Properties → Previous versions tab. Now you will see all available copies of that particular file and the time when it was stored in a Shadow Volume Copy. Choose the version of the file you want to retrieve and click Copy if you want to save it to some directory of your own, or Restore if you want to replace existing, encrypted file. If you want to see the content of file first, just click Open.
b) Shadow Explorer It is a program that can be found online for free. You can download either a full or a portable version of Shadow Explorer. Open the program. On the left top corner select the drive where the file you are looking for is a stored. You will see all folders on that drive. To retrieve a whole folder, right-click on it and select “Export”. Then choose where you want it to be stored.

Step 4. Use Data Recovery programs to recover Trojan-Syria virus encrypted files
There are several data recovery programs that might recover encrypted files as well. This does not work in all cases but you can try this:- We suggest using another PC and connect the infected hard drive as slave. It is still possible to do this on infected PC though.
- Download a data recovery program.
- Install and scan for recently deleted files.