Striked ransomware virus progressed to the point where security researchers had to consult victims about the possible elimination and decryption processes. This crypto-virus surfaced sometime around the 6th of July; shockingly, no explicit explanations about this infection have not been made yet. The Python language was selected to generate the infection and the creation was produced into a Windows executable. Security tools provide us with evidence as they label it as Python/Filecoder.AH.
More about this threat
One of the victims of this infection provided information that helped security researchers figure out the payload of this infection. Nukem.exe and 80317e3194d8f7fd495b0bf06cae2295.exe.@ have been uploaded by victims as the possible sources of the malicious behavior in infected devices. A README_DECRYPT.html file is uploaded into victims’ desktops which opens a page in a preferred browser. Besides this file, you should have noticed a change when it comes to your digital data. While their filenames and sizes remain the same, the crypto-virus is programmed to append .#<email># id # <id> extension at the end.
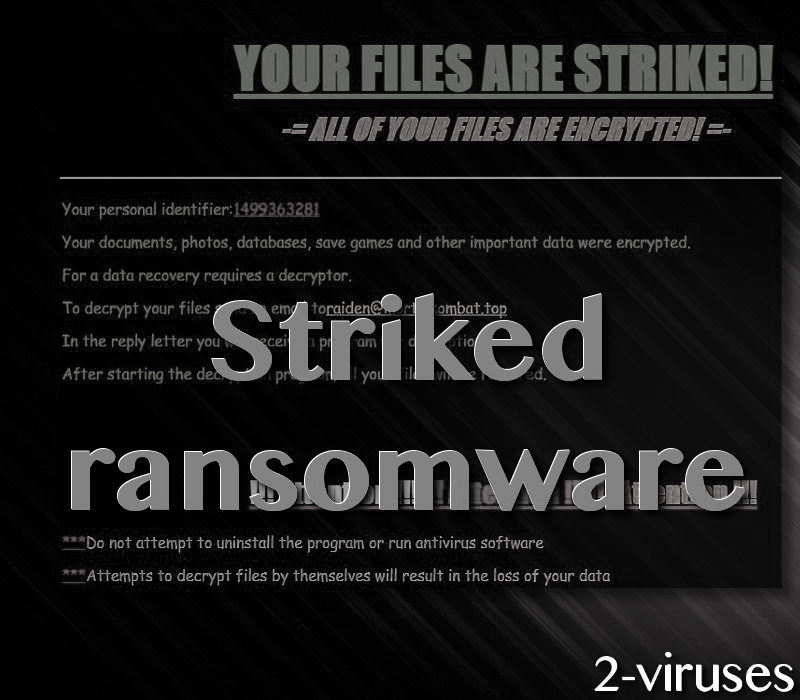
Ransomware features letters of demands: this variant is not an exception. The content of this file follows the standard template. The formula of a ransom note is simple: to inform a visitor that their files are encrypted with elaborate cryptography techniques, to threaten victims and to demand a generous payment for file-decryption. In this case, a additional steps are included. Hackers assign individual ID numbers (personal identifiers) for their victims. Also, for more than a brief explanation about the events, victims are requested to contact hackers via [email protected] email address.
It could be that this Striked crypto-virus is compiled by gaming-fanatics that wished to earn a couple of bucks. From the reports we dug out, there were no records of anyone contacting the latter email address. Even if the victims would have initiated a conversation, they might have not received any response. We doubt that authors of this infection would aim to require a lot of money. Following the custom demand plans, sums from 0.1 to 1 BTC prevail. This refers to a range from 237.68 to 2376.75 US dollars.
Decryption, removal and ways to avert crypto-viruses
We have not been introduced with methods that could be applied for a free file-recovery. Nevertheless, security researchers might need more time to analyze the received samples before more pleasant applications will be released. If analysts actually generate a free decryption tool, we will inform you as soon as we get the chance.
Even though the creators of this infection strongly suggest that victims would not attempt to uninstall the program or run antivirus software, this is something that you must do. To be cautious, you could copy all of the encrypted material and placed it somewhere safe. This action would protect your data from being affected during the process of ransomware-removal. For this purpose, you should scan your operating system with tools like Spyhunter or Malwarebytes.
As soon as the crypto-virus is gone from your OS, you can start engaging in the possible file-recovery techniques. One of them is the restoration of Shadow Volume Copies which could be your salvation. In addition to that, security researchers have introduced some universal file-recovery tools that also can initiate a change for the better. Nevertheless, the best option would be to to have your files stored in backup storages before a ransomware manages to scramble your digital data.
As for the distribution of this infection, it is guessed that the infection might have been inserted via remote control protocol. In addition to that, remember that ransomware infections can join your operating system in forms of seemingly-innocent email attachments, questionable website or even social networking sites.
Update of the 25 of July. As security researcher Michael Gillespie has managed to create a decryptor for this virus. Exploit it to recover your data.
Striked Ransomware Virus quicklinks
- More about this threat
- Decryption, removal and ways to avert crypto-viruses
- Automatic Malware removal tools
- How to recover Striked ransomware virus encrypted files and remove the virus
- Step 1. Restore system into last known good state using system restore
- 1. Reboot your computer to Safe Mode with Command Prompt:
- 2.Restore System files and settings.
- Step 4. Use Data Recovery programs to recover Striked ransomware virus encrypted files
Automatic Malware removal tools
(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
How to recover Striked ransomware virus encrypted files and remove the virus
Step 1. Restore system into last known good state using system restore
1. Reboot your computer to Safe Mode with Command Prompt:
for Windows 7 / Vista/ XP
- Start → Shutdown → Restart → OK.
- Press F8 key repeatedly until Advanced Boot Options window appears.
- Choose Safe Mode with Command Prompt.

for Windows 8 / 10
- Press Power at Windows login screen. Then press and hold Shift key and click Restart.

- Choose Troubleshoot → Advanced Options → Startup Settings and click Restart.
- When it loads, select Enable Safe Mode with Command Prompt from the list of Startup Settings.

2.Restore System files and settings.
- When Command Prompt mode loads, enter cd restore and press Enter.
- Then enter rstrui.exe and press Enter again.

- Click “Next” in the windows that appeared.

- Select one of the Restore Points that are available before Striked ransomware virus has infiltrated to your system and then click “Next”.

- To start System restore click “Yes”.

Step 2. Complete removal of Striked ransomware virus
After restoring your system, it is recommended to scan your computer with an anti-malware program, like Spyhunter and remove all malicious files related to Striked ransomware virus. You can check other tools here.Step 3. Restore Striked ransomware virus affected files using Shadow Volume Copies
If you do not use System Restore option on your operating system, there is a chance to use shadow copy snapshots. They store copies of your files that point of time when the system restore snapshot was created. Usually Striked ransomware virus tries to delete all possible Shadow Volume Copies, so this methods may not work on all computers. However, it may fail to do so. Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8. There are two ways to retrieve your files via Shadow Volume Copy. You can do it using native Windows Previous Versions or via Shadow Explorer. a) Native Windows Previous Versions Right-click on an encrypted file and select Properties → Previous versions tab. Now you will see all available copies of that particular file and the time when it was stored in a Shadow Volume Copy. Choose the version of the file you want to retrieve and click Copy if you want to save it to some directory of your own, or Restore if you want to replace existing, encrypted file. If you want to see the content of file first, just click Open.
b) Shadow Explorer It is a program that can be found online for free. You can download either a full or a portable version of Shadow Explorer. Open the program. On the left top corner select the drive where the file you are looking for is a stored. You will see all folders on that drive. To retrieve a whole folder, right-click on it and select “Export”. Then choose where you want it to be stored.

Step 4. Use Data Recovery programs to recover Striked ransomware virus encrypted files
There are several data recovery programs that might recover encrypted files as well. This does not work in all cases but you can try this:- We suggest using another PC and connect the infected hard drive as slave. It is still possible to do this on infected PC though.
- Download a data recovery program.
- Install and scan for recently deleted files.








