January took an interesting and frightening turn when novel viruses began to pop. Just yesterday, our researchers were concerned with a complicated Spora virus which showed high-level encryption and resistance. Now, without advance warning, we have to introduce a new ransomware infection which definitely is not your typical virus. This time cunning hackers decided to profit by helping amateur programmers design new ransomware viruses. Facility which offers such assistance was noticed to be endorsed in secretive domains that are popular hangouts for people, interested in hacking. Now, if a person formulates an idea for a virus, but does not have capacities to construct such a threat, he can use resources that are provided Satan ransomware service. This fast-ransomware-delivery requires a party to register on their site. Surprisingly, this service does not have a fee, but if the registered users gain profit, some percentage from it is going to belong to the founders of Satan ransomware service. Users will only get 70% of their first profit, but the more revenue they bring, the more this percentage is going to grow.
Satan ransomware service: it is here to help and to spread terror
Once Satan ransomware strikes, it will target over a hundred file types and turn then into a bunch of useless and unrecognizable executables, appended with .stn extension. Users won’t be able to tell one file from another since their former titles are going to be changed. Its payload is going to get dropped into one of the folders, and experts discovered that it can be found under the name TaskHost.exe. In addition to that, Satan virus will implement another process: it will delete a big part of data in C: Drive. As it has become accustomed, victims are going to be informed about their situation and ID number in a HTML file, called HELP_DECRYPT_FILES.
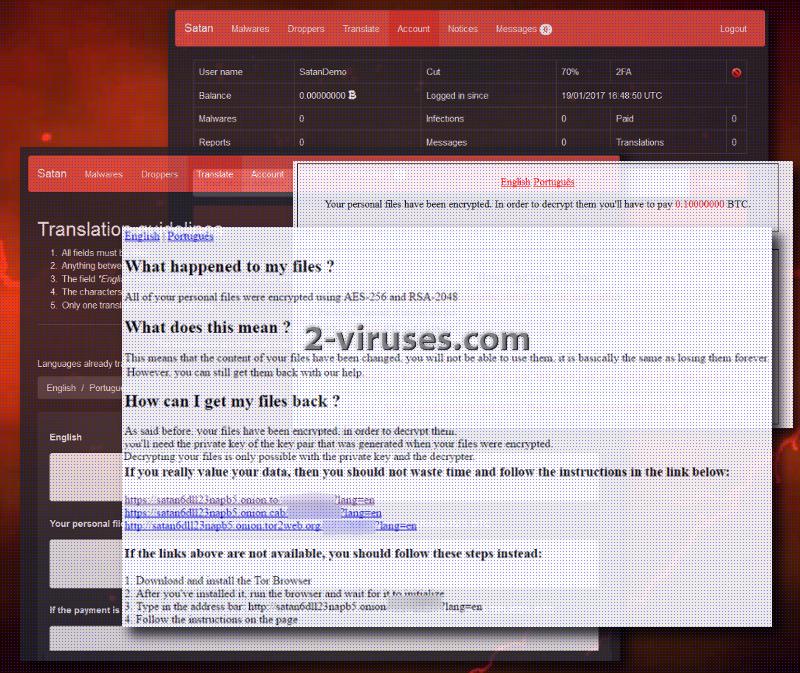
Until now, creating a ransomware required some knowledge even if people exploited Hidden Tear project as an example for their variant. Now, with Satan ransomware service, crafting a crypto-virus is as easy as online shopping or creating a profile for your account. All you have to do is register, fill in some blank spaces and bam: your ransomware infection is ready to bring misery. A striving hacker that registers in Satan ransomware service will have to create a Bitcoin account. When the process of creating a ransomware is finished, it is going to be possible to keep track of the number of infected people and how many of them paid the ransom.
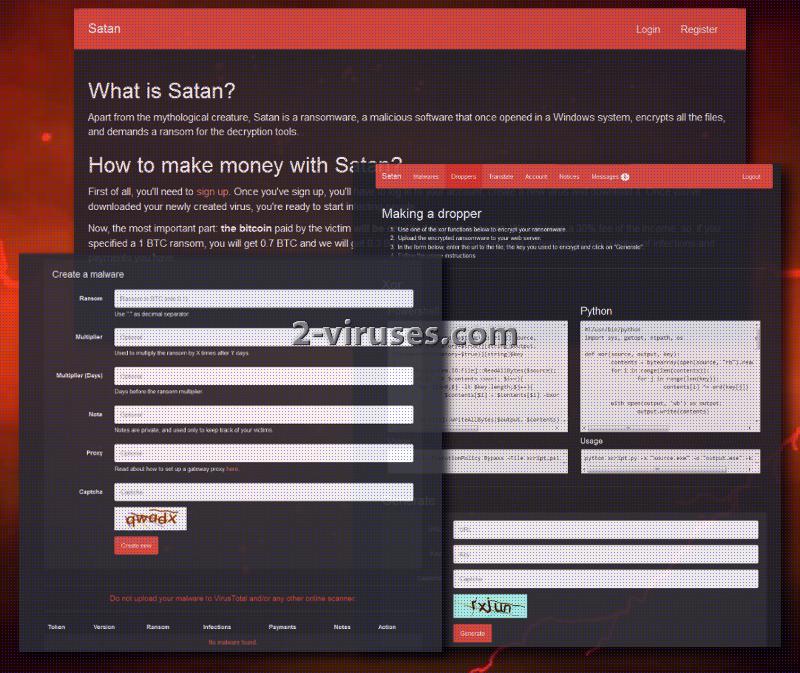
Preparing a new ransomware sample, supported by resources from Satan himself, is relatively simple. Users will have to decide on a ransom and whether it is going to be doubled if a victim fails to send money via the given period of time. Then, user has to encrypt the created malware with one of the provided xor functions (either Powershell or Python). This will lead to the creation of the malicious executable, or a.k.a payload, which is going to be transmitted.
Is it possible to send Satan ransomware back to hell and revive my files?
At the moment a free decryptor for this variant is not available. Experts might be having some difficulties in coming up with a tool to restore files, but there is always a chance that they are going to succeed. With confidence in security specialists, we count the days until Satan ransomware will no longer be a threat. For now, people should be careful not to get infected with it. However, you should also be prepared for an infection. You can do this by uploading your files in online backup storages that protect files from being tampered with. In addition to that, you can simply keep files in your USB flash drivers but never keep them plugged into your device. If a ransomware slithers into your device, it might affect files in the flash drive as well.
So, decryption is off-limits. What is relevant about the distribution of Satan ransomware?
One of the most effective ways to distribute a payload of ransomware is to add it to fake spam letters. Such messages are usually written to convince people that their accounts, taxes, refunds, flights or other important details are compromised. For more information, recipients are advised to click on the provided links or download executables. If they do as told, and the file turns out to be malicious, then they will activate a ransomware virus and it will begin its secretive plan. Because of this simple mistake, all of your files can become encrypted. If you do not want to be jeopardized, always make sure that the sender is trustworthy.
Now, the information about elimination of Satan ransomware. Even though its decryption is a complicated task, its removal is easier. You can remove it either manually, or automatically. The second option requires users to have an up-to-date anti-malware tool, like Spyhunter or Hitman. Manual removal is going to be done after instructions below are follow through-fully.
Satan Ransomware quicklinks
- Satan ransomware service: it is here to help and to spread terror
- Is it possible to send Satan ransomware back to hell and revive my files?
- So, decryption is off-limits. What is relevant about the distribution of Satan ransomware?
- Automatic Malware removal tools
- How to recover Satan ransomware encrypted files and remove the virus
- Step 1. Restore system into last known good state using system restore
- 1. Reboot your computer to Safe Mode with Command Prompt:
- 2.Restore System files and settings.
- Step 4. Use Data Recovery programs to recover Satan ransomware encrypted files
Automatic Malware removal tools
(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
How to recover Satan ransomware encrypted files and remove the virus
Step 1. Restore system into last known good state using system restore
1. Reboot your computer to Safe Mode with Command Prompt:
for Windows 7 / Vista/ XP
- Start → Shutdown → Restart → OK.
- Press F8 key repeatedly until Advanced Boot Options window appears.
- Choose Safe Mode with Command Prompt.

for Windows 8 / 10
- Press Power at Windows login screen. Then press and hold Shift key and click Restart.

- Choose Troubleshoot → Advanced Options → Startup Settings and click Restart.
- When it loads, select Enable Safe Mode with Command Prompt from the list of Startup Settings.

2.Restore System files and settings.
- When Command Prompt mode loads, enter cd restore and press Enter.
- Then enter rstrui.exe and press Enter again.

- Click “Next” in the windows that appeared.

- Select one of the Restore Points that are available before Satan virus has infiltrated to your system and then click “Next”.

- To start System restore click “Yes”.

Step 2. Complete removal of Satan ransomware
After restoring your system, it is recommended to scan your computer with an anti-malware program, like Spyhunter and remove all malicious files related to Satan virus. You can check other tools here.Step 3. Restore Satan ransomware affected files using Shadow Volume Copies
If you do not use System Restore option on your operating system, there is a chance to use shadow copy snapshots. They store copies of your files that point of time when the system restore snapshot was created. Usually Satan virus tries to delete all possible Shadow Volume Copies, so this methods may not work on all computers. However, it may fail to do so. Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8. There are two ways to retrieve your files via Shadow Volume Copy. You can do it using native Windows Previous Versions or via Shadow Explorer. a) Native Windows Previous Versions Right-click on an encrypted file and select Properties → Previous versions tab. Now you will see all available copies of that particular file and the time when it was stored in a Shadow Volume Copy. Choose the version of the file you want to retrieve and click Copy if you want to save it to some directory of your own, or Restore if you want to replace existing, encrypted file. If you want to see the content of file first, just click Open.
b) Shadow Explorer It is a program that can be found online for free. You can download either a full or a portable version of Shadow Explorer. Open the program. On the left top corner select the drive where the file you are looking for is a stored. You will see all folders on that drive. To retrieve a whole folder, right-click on it and select “Export”. Then choose where you want it to be stored.

Step 4. Use Data Recovery programs to recover Satan ransomware encrypted files
There are several data recovery programs that might recover encrypted files as well. This does not work in all cases but you can try this:- We suggest using another PC and connect the infected hard drive as slave. It is still possible to do this on infected PC though.
- Download a data recovery program.
- Install and scan for recently deleted files.








