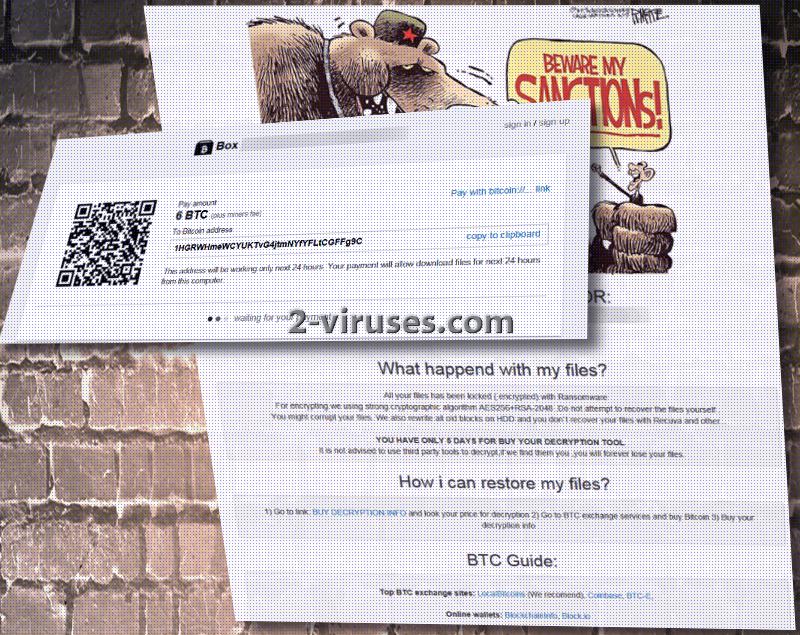
During the weekend, ransomware creators were not resting: they developed a number of new infections. One of them is a Sanctions crypto-virus, crafted as a response to the attempts of sanctioning Russia for its reprehensible actions in Ukraine. Main communist symbol of a hammer and a sickle are spotted in the caricature that Sanctions virus displays in its html ransom note. The image clearly mocks the restrictions of USA and other countries as if Russia is not bothered by these sanctions. From the mockery of this sample, we can assume that this infection is created by Russian hackers. More information about the variant and its relations to other viruses will be discussed in the following paragraphs.
Significant features of Sanctions ransomware
Dharma crypto-virus was immediately regarded as related to the Sanctions ransomware. Why? Both of these infections append .wallet extension to the files that it severely damages with encryption. However, the conclusion denied the link between these samples and it was determined that the extension might be the only thing that these two variants have in common. Why? Well, Dharma is a unique sample and its structure appears to differ from Sanctions virus.
Russians or hackers of different nationalities that constructed Sanctions ransomware appear to be obnoxiously greedy: they do not demand 1, 2, nor 3 Bitcoins, but 6. If US dollars are easier to comprehend: the demand sum equals $6868.50. If the creators are people from Russia, then the economic struggle is evident. These instructions are specified in a RESTORE_ALL_DATA.html file which opens up in victims’ preferred browser. AES-256 and RSA-2048 are indicated as the algorithms that Sanctions virus operates with.
Authors of Sanctions ransomware are not only greedy, but impatient. They give 5 days for victims to make a transaction of 6 bitcoins if they do not wish for a decryption key would be permanently deleted. Additionally, Sanctions virus marks each victim with a unique ID code. More information about the destination of bitcoins and other details are found in a website Satoshibox.com. We hope you won’t be convinced that paying the ransom is the way to go. Since 6 BTC might be out of this world for some people, it is possible that specific users are chosen as victims by the creators of Sanctions ransomware.
Sanctions ransomware and ways of restoring encrypted data
Sanctions ransomware is a recent infection and security researchers were not yet able to determine the best way to decrypt files that it damages. Some people have got infected with this voracious virus and the demanded ransom is 6 bitcoins, plus fees. If you get infected with this ransomware, its authors are against victims using universal file-recovery tools. It is explained that all of the data might be lost. However, we think that the most optimal way out of this situation is to remove the infection and then, try different ways of recovering files. Just last Friday we celebrated the world backup day: we hope that you took it as a reminder of storing files in backup storages for safety.
Sanctions ransomware and potential ways of getting infected with it
We are guessing that because the ransom is set so high, that ransomware might be targeting people that would find their data valuable enough to pay. Researchers raise a concern that specific people can be targeted by the hackers. However, it is possible that random people will also be exposed to the payload of Sanctions virus, so you should not lose your focus. Malicious executables can be transmitted in email letters or reach you from bizarre file-sharing facilities.
Spyhunter, Malwarebytes and Hitman anti-malware tools will help you remove all of the malicious content from your system. This includes browser hijackers, adware parasites and even ransomware infections like Sanctions virus.
Sanctions Ransomware quicklinks
- Significant features of Sanctions ransomware
- Sanctions ransomware and ways of restoring encrypted data
- Sanctions ransomware and potential ways of getting infected with it
- Automatic Malware removal tools
- How to recover Sanctions Ransomware encrypted files and remove the virus
- Step 1. Restore system into last known good state using system restore
- 1. Reboot your computer to Safe Mode with Command Prompt:
- 2.Restore System files and settings.
- Step 4. Use Data Recovery programs to recover Sanctions Ransomware encrypted files

Automatic Malware removal tools
(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
How to recover Sanctions Ransomware encrypted files and remove the virus
Step 1. Restore system into last known good state using system restore
1. Reboot your computer to Safe Mode with Command Prompt:
for Windows 7 / Vista/ XP
- Start → Shutdown → Restart → OK.
- Press F8 key repeatedly until Advanced Boot Options window appears.
- Choose Safe Mode with Command Prompt.

for Windows 8 / 10
- Press Power at Windows login screen. Then press and hold Shift key and click Restart.

- Choose Troubleshoot → Advanced Options → Startup Settings and click Restart.
- When it loads, select Enable Safe Mode with Command Prompt from the list of Startup Settings.

2.Restore System files and settings.
- When Command Prompt mode loads, enter cd restore and press Enter.
- Then enter rstrui.exe and press Enter again.

- Click “Next” in the windows that appeared.

- Select one of the Restore Points that are available before Sactions virus has infiltrated to your system and then click “Next”.

- To start System restore click “Yes”.

Step 2. Complete removal of Sanctions Ransomware
After restoring your system, it is recommended to scan your computer with an anti-malware program, like Spyhunter and remove all malicious files related to Sactions virus. You can check other tools here.Step 3. Restore Sanctions Ransomware affected files using Shadow Volume Copies
If you do not use System Restore option on your operating system, there is a chance to use shadow copy snapshots. They store copies of your files that point of time when the system restore snapshot was created. Usually Sactions virus tries to delete all possible Shadow Volume Copies, so this methods may not work on all computers. However, it may fail to do so. Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8. There are two ways to retrieve your files via Shadow Volume Copy. You can do it using native Windows Previous Versions or via Shadow Explorer. a) Native Windows Previous Versions Right-click on an encrypted file and select Properties → Previous versions tab. Now you will see all available copies of that particular file and the time when it was stored in a Shadow Volume Copy. Choose the version of the file you want to retrieve and click Copy if you want to save it to some directory of your own, or Restore if you want to replace existing, encrypted file. If you want to see the content of file first, just click Open.
b) Shadow Explorer It is a program that can be found online for free. You can download either a full or a portable version of Shadow Explorer. Open the program. On the left top corner select the drive where the file you are looking for is a stored. You will see all folders on that drive. To retrieve a whole folder, right-click on it and select “Export”. Then choose where you want it to be stored.

Step 4. Use Data Recovery programs to recover Sanctions Ransomware encrypted files
There are several data recovery programs that might recover encrypted files as well. This does not work in all cases but you can try this:- We suggest using another PC and connect the infected hard drive as slave. It is still possible to do this on infected PC though.
- Download a data recovery program.
- Install and scan for recently deleted files.