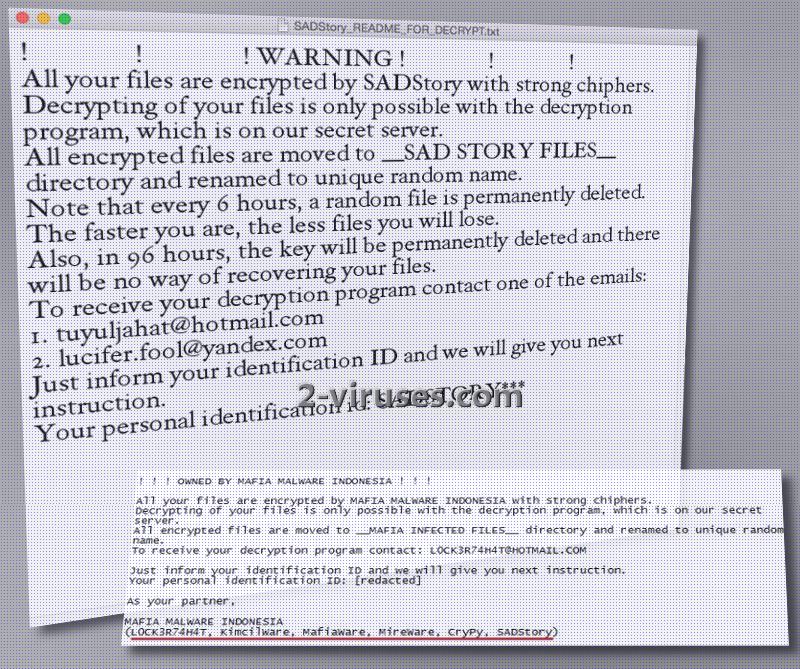
SADStory is a new crypto-virus, designed by the same group of crooks that are responsible for MafiaWare variant. Mafia Malware Indonesia is a collective of hackers that do not strike as extremely skilled professionals. Their developed infections are classified as weak as they are based on open source codes like HiddenTear. Such ransomware is not that difficult to sort out and crack. SADStory virus is the most recent product of the Indonesian group. At first, the group hid the fact that they were responsible for a bunch of ransomware infections, but after security researchers were on to find them, Mafia Malware Indonesia updated SADStory virus and listed the infections that they are responsible for.
Explaining SADStory ransomware and its flaws
It is presumable that SADStory virus will not only encrypt files with complicated ciphers, but also place them in one convenient location. Instructions and demands are explained in a .txt file which gets placed into devices. The executable contains regular content: hackers state that a system is infected, files are encrypted and the only possible solution is to receive a decryption program from crooks’ secret server. Users can find a directory called _SAD STORY FILES_ in which all encrypted data is stored. Encoded executables will be modified to feature .sad extension at the very end. Authors of SADStory ransomware encourage victims not to rebel: they should contact either [email protected] or [email protected].
SADStory virus claims that after every 6 hours, ransomware will randomly delete 1 file. After 96 hours, the key for decryption will be deleted and it will be impossible to restore it. SADStory virus is developed in the Python programming language. More than 200 file types are targeted. ReadMe-how_to_get_free_office365-idGHDGFGf426142GE25.pdf.exe file is supposedly the payload that arrives from the Internet to starts the activity of SADStory ransomware.
It appears to be that the filename poses as a some sort of tutorial on how to get a free Microsoft Office application. After scanning the executable from malware, we noticed that definitely not all anti-malware tools detect anything malicious in this executable. However, some of them did. One of them indicates the threat as Win32.Trojan-Ransom.CryPy.A. CryPy is another infection that Mafia Malware Indonesia have created over the course of their career.
How can the .sad files be restored?
SADStory ransomware will encrypt files and move them to one location. The data will not be usable after a ransomware has finished encoding it. It may be that you can remove the infection without worrying that it will delete all of the files it placed in _SAD STORY FILES_. We cannot state that the encrypted data won’t put up a fight. However, since SADStory ransomware is based on open-source codes, there is a chance that this variant is decryptable. Currently, no users have reported about becoming victims of this sample. Until SADStory virus infects people and poses a real threat, security researchers should not pay too much attention to such junk ransomware. Bear in mind that storing files into alternative locations is a very beneficial decision. As long as you have stored your data in multiple places, you can be more safe not to lose them.
Let’s explain the transmission of SADStory
SADStory ransomware variant will presumably use the most common tactics for distribution. Since the file that is identified as the payload indicates that it helps people download Microsoft Office tools completely free-of-charge, we presume that the file can be offered to users in various online file-sharing facilities. Unsuspecting users might download it without realizing that the file is malicious. Additionally, the payload can be trasmitted via malicious email letters that feature attachments. Make sure not to download any content that is not 100% legitimate and reliable. Such downloads very frequently turn out to be malware.
Sadstory Ransomware quicklinks
- Explaining SADStory ransomware and its flaws
- How can the .sad files be restored?
- Let’s explain the transmission of SADStory
- Automatic Malware removal tools
- How to recover SADStory ransomware encrypted files and remove the virus
- Step 1. Restore system into last known good state using system restore
- 1. Reboot your computer to Safe Mode with Command Prompt:
- 2.Restore System files and settings.
- Step 4. Use Data Recovery programs to recover SADStory ransomware encrypted files

Automatic Malware removal tools
(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
How to recover SADStory ransomware encrypted files and remove the virus
Step 1. Restore system into last known good state using system restore
1. Reboot your computer to Safe Mode with Command Prompt:
for Windows 7 / Vista/ XP
- Start → Shutdown → Restart → OK.
- Press F8 key repeatedly until Advanced Boot Options window appears.
- Choose Safe Mode with Command Prompt.

for Windows 8 / 10
- Press Power at Windows login screen. Then press and hold Shift key and click Restart.

- Choose Troubleshoot → Advanced Options → Startup Settings and click Restart.
- When it loads, select Enable Safe Mode with Command Prompt from the list of Startup Settings.

2.Restore System files and settings.
- When Command Prompt mode loads, enter cd restore and press Enter.
- Then enter rstrui.exe and press Enter again.

- Click “Next” in the windows that appeared.

- Select one of the Restore Points that are available before SADStory virus has infiltrated to your system and then click “Next”.

- To start System restore click “Yes”.

Step 2. Complete removal of SADStory ransomware
After restoring your system, it is recommended to scan your computer with an anti-malware program, like Spyhunter and remove all malicious files related to SADStory virus. You can check other tools here.Step 3. Restore SADStory ransomware affected files using Shadow Volume Copies
If you do not use System Restore option on your operating system, there is a chance to use shadow copy snapshots. They store copies of your files that point of time when the system restore snapshot was created. Usually SADStory virus tries to delete all possible Shadow Volume Copies, so this methods may not work on all computers. However, it may fail to do so. Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8. There are two ways to retrieve your files via Shadow Volume Copy. You can do it using native Windows Previous Versions or via Shadow Explorer. a) Native Windows Previous Versions Right-click on an encrypted file and select Properties → Previous versions tab. Now you will see all available copies of that particular file and the time when it was stored in a Shadow Volume Copy. Choose the version of the file you want to retrieve and click Copy if you want to save it to some directory of your own, or Restore if you want to replace existing, encrypted file. If you want to see the content of file first, just click Open.
b) Shadow Explorer It is a program that can be found online for free. You can download either a full or a portable version of Shadow Explorer. Open the program. On the left top corner select the drive where the file you are looking for is a stored. You will see all folders on that drive. To retrieve a whole folder, right-click on it and select “Export”. Then choose where you want it to be stored.

Step 4. Use Data Recovery programs to recover SADStory ransomware encrypted files
There are several data recovery programs that might recover encrypted files as well. This does not work in all cases but you can try this:- We suggest using another PC and connect the infected hard drive as slave. It is still possible to do this on infected PC though.
- Download a data recovery program.
- Install and scan for recently deleted files.