RedBoot ransomware virus was first detected several years back. At that time, security specialists did not pay much attention to it as the found sample was poorly coded and ended up being placed into category of unfinished ransomware. This in development threat resurfaced in 23rd of September (2017) and carries similarities to infections like NotPetya and Spora. RedBoot ransomware was prepared in AutoIT environment and appends .locked extension to all ruined data.
RedBoot virus acts like a ransomware and a wiper
Boot sectors (MBR a.k.a master boot record) might be influenced without any possibilities to reverse the damage. Security researchers categorize RedBoot virus between a crypto-infection and a wiper which was the term used to describe NotPetya (Is RedBoot a wiper?). However, hackers might have done a mistake while preparing this infection and the irreversible damage might be just a misunderstanding.
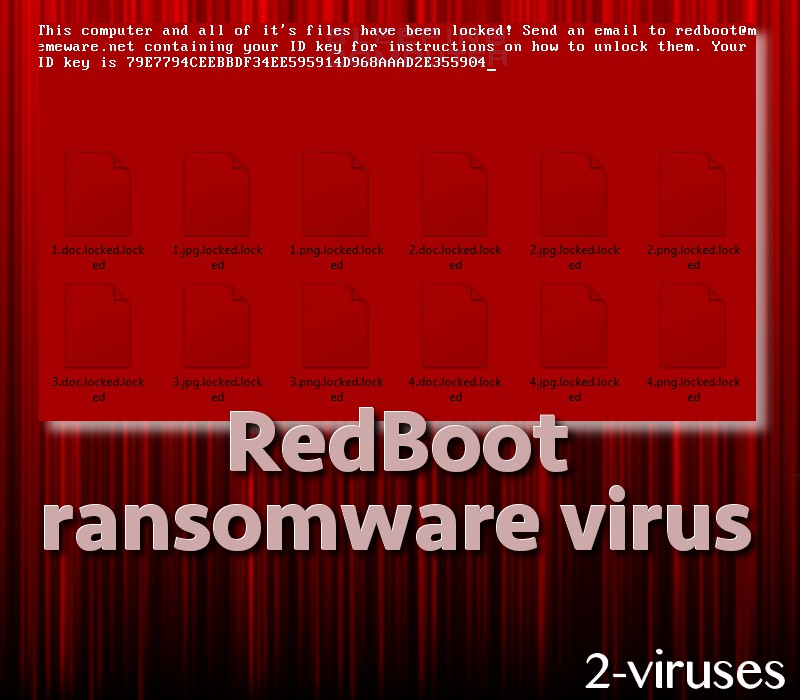
Soon after RedBoot malware gets a chance to be active, it will implant five files into infected operating systems. Executables called boot.asm, assembler.exe, main.exe and overwrite.exe are all placed into random folders. Firstly, these files will have to influenced master boot record (What is MBR?) and replace it with a harmful boot.bin file.
Then, the encryption of files will follow, leading up to the fact that some applications and processes will no longer be launchable. .locked extension will be appended to all sorts of files, from the ones that are a part of an OS and regular users’ pictures, videos and etc. This exact extension is not unusual: variants of ApolloLocker and BitPaymer have been noticed to leave the same extension to the data it encodes.
After RedBoot crypto-virus uses encryption to damage files, infection will automatically restart an operating system. However, it won’t launch normally and instead of presenting victims’ desktops, will show a short ransom note (Screen locked by ransomware). It will urge users to send email messages to [email protected]. Victims will be required to include specific ID numbers into the sent email messages. The exact sum of demanded bitcoins is unknown, but we do presume that this cryptocurrency will be required for file decryption. However, hackers might be incapable of helping their victims.
Ransomware removal, prevention and decryption
The fact that this RedBoot virus not only damages files but also MBR is not a good news. If this was intentional, the only presumable way to decrypt files might be to pay the demanded ransoms. However, if hackers are simply sloppy and left this mistake accidentally, then the influenced operating system might have no way of receiving aid. Of course, we have to wait for more elaborate analysis and wait for the results. Please be extremely cautious and try to avert this frightening infection.
Victims of RedBoot infection could have very little chance of recovering data with universal tools. Also, security researchers might also not be capable of helping them. However, you can help yourself. Store your digital information in backup storages or at least put them in USB flash drives (Benefits of data backup). If any type of infection influences your data in hard drives, then you will have no need to worry. If all surfers would backup their data, ransomware industry would die out as no one would pay the ransom. However, as long as people refuse to secure their information, crypto-viruses will thrive.
However, there the fact that more sophisticated and elaborate ransomware infections are being produced is undeniable. Some variant influence operating systems to the point that they are no longer functional. More frequent global attacks also do not suggest anything positive. If anything, the activity of ransomware infections has only increased in 2017.
Ransomware infections could slither thanks to poorly-protected RDP. Therefore, users should pay attention to the way they are secured. Additionally, do not interact with random pop-ups or websites. Users’ emailing accounts could also be filled with suspicious attachments. Please do not download files from letters that originate from unknown sources.
Redboot Ransomware Virus quicklinks
- RedBoot virus acts like a ransomware and a wiper
- Ransomware removal, prevention and decryption
- Automatic Malware removal tools
- How to recover RedBoot ransomware virus encrypted files and remove the virus
- Step 1. Restore system into last known good state using system restore
- 1. Reboot your computer to Safe Mode with Command Prompt:
- 2.Restore System files and settings.
- Step 4. Use Data Recovery programs to recover RedBoot ransomware virus encrypted files
Automatic Malware removal tools
(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
How to recover RedBoot ransomware virus encrypted files and remove the virus
Step 1. Restore system into last known good state using system restore
1. Reboot your computer to Safe Mode with Command Prompt:
for Windows 7 / Vista/ XP
- Start → Shutdown → Restart → OK.
- Press F8 key repeatedly until Advanced Boot Options window appears.
- Choose Safe Mode with Command Prompt.

for Windows 8 / 10
- Press Power at Windows login screen. Then press and hold Shift key and click Restart.

- Choose Troubleshoot → Advanced Options → Startup Settings and click Restart.
- When it loads, select Enable Safe Mode with Command Prompt from the list of Startup Settings.

2.Restore System files and settings.
- When Command Prompt mode loads, enter cd restore and press Enter.
- Then enter rstrui.exe and press Enter again.

- Click “Next” in the windows that appeared.

- Select one of the Restore Points that are available before RedBoot ransomware virus has infiltrated to your system and then click “Next”.

- To start System restore click “Yes”.

Step 2. Complete removal of RedBoot ransomware virus
After restoring your system, it is recommended to scan your computer with an anti-malware program, like Spyhunter and remove all malicious files related to RedBoot ransomware virus. You can check other tools here.Step 3. Restore RedBoot ransomware virus affected files using Shadow Volume Copies
If you do not use System Restore option on your operating system, there is a chance to use shadow copy snapshots. They store copies of your files that point of time when the system restore snapshot was created. Usually RedBoot ransomware virus tries to delete all possible Shadow Volume Copies, so this methods may not work on all computers. However, it may fail to do so. Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8. There are two ways to retrieve your files via Shadow Volume Copy. You can do it using native Windows Previous Versions or via Shadow Explorer. a) Native Windows Previous Versions Right-click on an encrypted file and select Properties → Previous versions tab. Now you will see all available copies of that particular file and the time when it was stored in a Shadow Volume Copy. Choose the version of the file you want to retrieve and click Copy if you want to save it to some directory of your own, or Restore if you want to replace existing, encrypted file. If you want to see the content of file first, just click Open.
b) Shadow Explorer It is a program that can be found online for free. You can download either a full or a portable version of Shadow Explorer. Open the program. On the left top corner select the drive where the file you are looking for is a stored. You will see all folders on that drive. To retrieve a whole folder, right-click on it and select “Export”. Then choose where you want it to be stored.

Step 4. Use Data Recovery programs to recover RedBoot ransomware virus encrypted files
There are several data recovery programs that might recover encrypted files as well. This does not work in all cases but you can try this:- We suggest using another PC and connect the infected hard drive as slave. It is still possible to do this on infected PC though.
- Download a data recovery program.
- Install and scan for recently deleted files.








