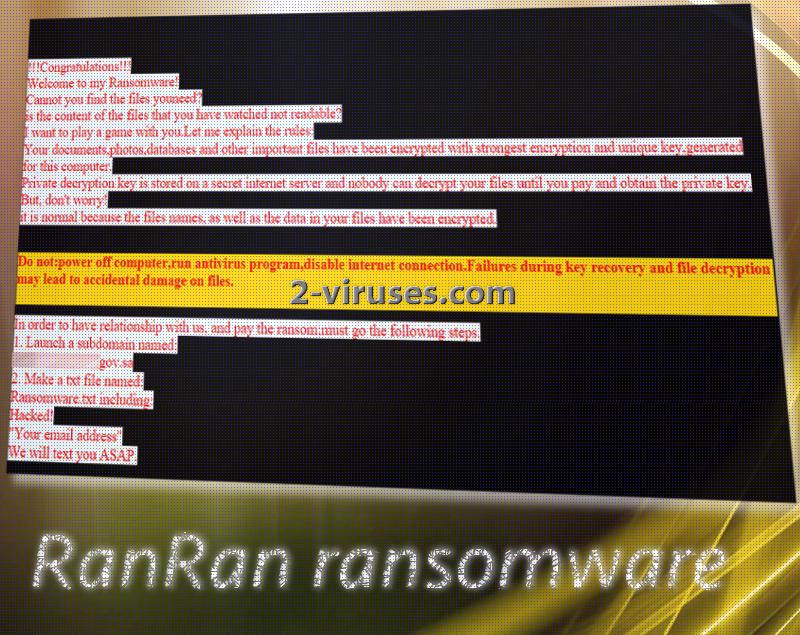
This ransomware seems to incorporate awfully political statements and surprisingly, does not require people to pay a ransom but demands them to pursue another action. Victims are supposed to make controversial statements about the king of Saudi Arabia. If you feel flustered about this variant, please continue on reading this article as it will provide you with all of the necessary information. RanRan virus is unique sample and we surely advise you to learn more about it. Since it is extremely easy to become infected with malware, we suggest you to always be cautious, avoid questionable links, websites, ads, email letters or messages/posts in social networking sites. RanRan virus is mostly targeting a one specific Middle-Eastern region. Instead of making transactions of bitcoins, victims of RanRan ransomware are encouraged to create a subdomain, ending in a gov.sa and a .txt executable called Ransomware.txt. The email is supposed to contain the victims’ email addresses that hackers are to allegedly going to contact them.
More details about RanRan ransomware
Currently, the exact way that RanRan exploits to gain access in devices is not clearly distinguished. However, this variant is not a strong one as security researchers can already provide professional assistance in the decryption process. Thanks to some significant flaws in the codes of RanRan virus, 2 tools for file-recovery are already available for people from Saudi Arabia. Speaking of the actual encryption process, RanRan variant uses a quite unique strategy to ruin data.
Files of different sizes are going to be encrypted with separate keys. The ransomware is going to create a “pubkey” folder in the C disk which will be appended with a key for encryption (RSA). If there is a malfunction in this process, ransomware does not plan to give up. It will take advantage out of md5 hash which functions as a code for RC4. In one way or another, RanRan virus will get the job of encryption done and every corrupted executable will be joined by a .zXz extension.
To match the extension it adds to the ruined data, RanRan virus also uploads a .zXz file on the desktop. After victims launch it, it will open up in one of the browsers they have installed. The message contains enough grammatical mistakes to suggest that it was not written by a fluent English speaker. Since it targets mostly people from Saudi Arabia, it is possible than a hacker from this country is responsible for it. This ransomware might be a some sort of rebellious act against the king of Saudi Arabia, but we doubt that this is the way to make a difference.
Decrypting files that have been corrupted by RanRan ransomware
Since RanRan virus seems to be created by amateurs, it is not considered a threat anymore. Not one, but two tools for decryption are now available for the victims of this variant. Click here to get transferred to a page in GitHub which will provide you with the public tools, designed to recover files. All of the necessary information will be found on the site. However, if you wish to be completely safe from ransomware, you should find the time to store your files in backup storages. There is a number of facilities that offer such a service. In addition to that, storing files in USB flash drives is also a good idea.
Potential ways to distribute RanRan ransomware
Before closing and spying on a number of processes, RanRan virus has to enter your device first. The exact way that hackers have selected to transmit this variant has not been determined, but we have a couple of guesses. First of all, it might be that random political letters could be sent to people from Saudi Arabia. The messages will presumably feature an attachment which will turn out to be the payload of RanRan virus. We always advise our readers to be careful while opening letters because you can never know: maybe you have been selected as a recipient of a spam letter.
To eliminate the RanRan virus, you have to select one out of two options. First one is the manual removal, but it might be difficult to pursue it if you do not have any experience in the removal of malware. An easier selection would be to employ an anti-malware tool for this job. Spyhunter or Malwarebytes will successfully detect and destroy all of the malware threats.
Ranran Ransomware quicklinks
- More details about RanRan ransomware
- Decrypting files that have been corrupted by RanRan ransomware
- Potential ways to distribute RanRan ransomware
- Automatic Malware removal tools
- How to recover RanRan ransomware encrypted files and remove the virus
- Step 1. Restore system into last known good state using system restore
- 1. Reboot your computer to Safe Mode with Command Prompt:
- 2.Restore System files and settings.
- Step 4. Use Data Recovery programs to recover RanRan ransomware encrypted files

Automatic Malware removal tools
(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
How to recover RanRan ransomware encrypted files and remove the virus
Step 1. Restore system into last known good state using system restore
1. Reboot your computer to Safe Mode with Command Prompt:
for Windows 7 / Vista/ XP
- Start → Shutdown → Restart → OK.
- Press F8 key repeatedly until Advanced Boot Options window appears.
- Choose Safe Mode with Command Prompt.

for Windows 8 / 10
- Press Power at Windows login screen. Then press and hold Shift key and click Restart.

- Choose Troubleshoot → Advanced Options → Startup Settings and click Restart.
- When it loads, select Enable Safe Mode with Command Prompt from the list of Startup Settings.

2.Restore System files and settings.
- When Command Prompt mode loads, enter cd restore and press Enter.
- Then enter rstrui.exe and press Enter again.

- Click “Next” in the windows that appeared.

- Select one of the Restore Points that are available before RanRan virus has infiltrated to your system and then click “Next”.

- To start System restore click “Yes”.

Step 2. Complete removal of RanRan ransomware
After restoring your system, it is recommended to scan your computer with an anti-malware program, like Spyhunter and remove all malicious files related to RanRan virus. You can check other tools here.Step 3. Restore RanRan ransomware affected files using Shadow Volume Copies
If you do not use System Restore option on your operating system, there is a chance to use shadow copy snapshots. They store copies of your files that point of time when the system restore snapshot was created. Usually RanRan virus tries to delete all possible Shadow Volume Copies, so this methods may not work on all computers. However, it may fail to do so. Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8. There are two ways to retrieve your files via Shadow Volume Copy. You can do it using native Windows Previous Versions or via Shadow Explorer. a) Native Windows Previous Versions Right-click on an encrypted file and select Properties → Previous versions tab. Now you will see all available copies of that particular file and the time when it was stored in a Shadow Volume Copy. Choose the version of the file you want to retrieve and click Copy if you want to save it to some directory of your own, or Restore if you want to replace existing, encrypted file. If you want to see the content of file first, just click Open.
b) Shadow Explorer It is a program that can be found online for free. You can download either a full or a portable version of Shadow Explorer. Open the program. On the left top corner select the drive where the file you are looking for is a stored. You will see all folders on that drive. To retrieve a whole folder, right-click on it and select “Export”. Then choose where you want it to be stored.

Step 4. Use Data Recovery programs to recover RanRan ransomware encrypted files
There are several data recovery programs that might recover encrypted files as well. This does not work in all cases but you can try this:- We suggest using another PC and connect the infected hard drive as slave. It is still possible to do this on infected PC though.
- Download a data recovery program.
- Install and scan for recently deleted files.








