A more feminine name has been selected to be known as a novel crypto-ransomware virus. This time, the floor is open for Princess Locker which enters into systems more like a shady lady than a true dame. It has been spotted just a couple of days ago and Michael Gillespie was the person that first discovered it. This luxurious highness insists that her victims would pay a surprising amount of bitcoins. Exactly how much? Continue on reading this article and you will find out enough about this virus.
About Princess Locker Ransomware
Princess Locker virus manages to infect computer devices pretty standardly, without exploiting any significant technologies or methods. Its strategy is to distribute the payload of this variant and hope that people will download it, one way or another. After such goal has been reached and the payload has started to take root in the infected device, then Princess Locker runs a scan for files to encrypt. Once this search is concluded, ransomware can ruin files win AES encryption. This virus does not have one special extension to add to the corrupted files, but rather a bunch of additions that can be distinct for every infected victim. However, Princess Locker virus manages to craft two identical executables for its targeted systems.
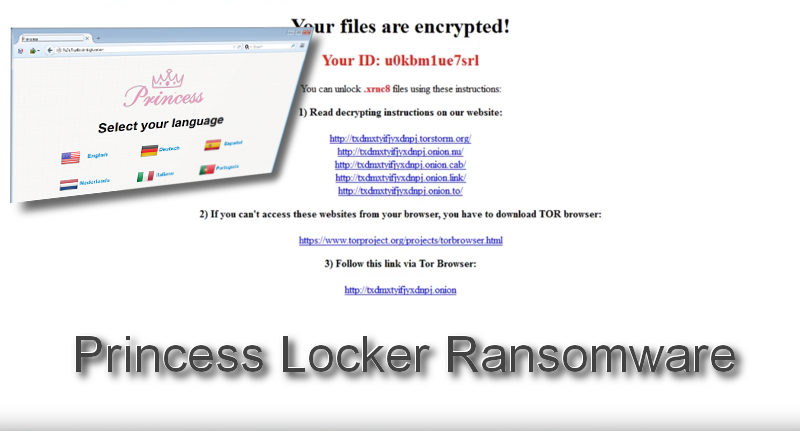
We are referring to the ransom notes that explain the course of action that have to be taken in order to restore the encrypted files. They are going to be named !_HOW_TO_RESTORE_[extension].TXT and !_HOW_TO_RESTORE_[extension].html, where the extension is the encrypted filename extension, which is a combination of 4 to 6 characters of any letters and numbers. For instance, the encrypted file will look like Text.doc.dgf7. This extension is also the unique ID of the infection. The ransom letter usually includes the personalized ID number as well. In order to get more details about the Princess Locker virus, you will have to access one of the enumerated websites. However, users might not be able to enter these domains unless they download TOR browser. In the mentioned webpages, victims will have to use their ID number to get login and to see the further instructions.
Once they enter any of the enumerated links, they will be transferred to a domain, requiring for the user to pick an appropriate language. As this screen seems to feature a number of languages, this means that the Princess Locker virus targets a wide range of people around the world. Furthermore, the accessed domain will also introduce a possibility of decrypting one selected executable. The size of this file has to be no bigger than 1 MB.
How to Decrypt Files Encrypted by Princess Locker Ransomware
Even though the creators of Princess Locker virus went through a lot of trouble to generate a quite elaborate scam, you should not think that they are going to keep their word and decrypt victims’ files. Furthermore, this ransomware demands for a ridiculous amount of bitcoins: 3 (around 1841.64 US Dollars). Since users are timed and if the clock strikes zero and they have not yet paid the demanded ransom, the sum is capable of growing up to 6 bitcoins. This is a freakishly heavy fee and we strongly urge you not to meet the requirements. In fact, there is no need to, as the free decryptor by the security expert hasherezade is available:
You can also download it from here: link.
For the future, always remember to store your files in backup storages or USB flash drives.
How is Princess Locker Ransomware Distributed?
Princess Locker virus presumably spreads like any other ransomware. The payloads of this infection can be hiding under seemingly innocent executables. If you receive a bizarre letter in your email account, please make sure that its source is trustworthy. However, sometimes crooks craft notifications about purchases or taxes that strike as reliable. Be careful when opening messages that do seem real. Before downloading an attachment or entering an indicated domain, be aware of the fact that such visitation can lead to Princess Locker ransomware virus. If you notice this infection in your system, you can try to remove it manually. Nevertheless, such action can sometimes do more damage than good. If you are not an experienced user, please run a full security scan with tools like Spyhunter or Hitman. These programs are going to take care of your security problems.
Update of the 20th of February, 2017. Princess Locker, after being silent for quite some time, was noticed to start using a new title for its ransom note. Now, infected victims will be introduced to @_USE_TO_FIX_JJnY.txt file.
Update of the 14th of March, 2018. A second version of Princess Locker has been detected. It demands 0.06 BTC at the beginning, but after some time, the ransom triples. In addition to this, the Princess Locker 2.0 virus appends random extensions to encrypted data. Victims will also notice a _THIS_TO_FIX.txt file with instructions.