Two days ago, on the 7th of December, 2016, a new in-development ransomware was detected by MalwareHunterTeam. It has been called Popcorn Time ransomware. According to the ransom note left by the coders of the virus, the ransomware was developed by a group of computer science students from Syria, one of whom writes that the crypto-malware was created for noble aspirations of helping the Syrian people, who are suffering from war for the last 5 years now. However, despite such altruistic allegations, the authors of Popcorn Time crypto-locker invite the victims to further spread the infection by offering them to infect the other two or more computers to gain the decryption key for free.
How does Popcorn Time Ransomware Infect the Systems?
Once the popcorn-time.exe file has been installed on the system, it will check whether the computer has already been infected with the code of the Popcorn Time file-encrypter. It is done by looking into the %AppData% folder for been_here and server_step_one files. If the latter files have been detected, the popcorn-time executable terminates itself. If the files have not been found on the directory, Popcorn Time encryption malware begins the procedure of encryption.
Popcorn Time file-encrypting virus uses AES-256 algorithm to carry out the actual process of encryption. Since this file-locker is still in its developmental version, it can only corrupt a test folder on the compromised machine’s desktop, which is called the Efiles folder. If the files of the following file types are found there, they get encrypted:
.1cd, .3dm, .3ds, .3fr, .3g2, .3gp, .3pr, .7z, .7zip, .aac, .aaf, .ab4, .accdb, .accde, .accdr, .accdt, .ach, .acr, .act, .adb, .adp, .ads, .aep, .aepx, .aes, .aet, .agdl, .ai, .aif, .aiff, .ait, .al, .amr, .aoi, .apj, .apk, .arch00, .arw, .as, .as3, .asf, .asm, .asp, .aspx, .asset, .asx, .atr, .avi, .awg, .back, .backup, .backupdb, .bak, .bar, .bay, .bc6, .bc7, .bdb, .bgt, .big, .bik, .bin, .bkf, .bkp, .blend, .blob, .bmd, .bmp, .bpw, .bsa, .c, .cas, .cdc, .cdf, .cdr, .cdr3, .cdr4, .cdr5, .cdr6, .cdrw, .cdx, .ce1, .ce2, .cer, .cfg, .cfr, .cgm, .cib, .class, .cls, .cmt, .config, .contact, .cpi, .cpp, .cr2, .craw, .crt, .crw, .cs, .csh, .csl, .css, .csv, .d3dbsp, .dac, .dar, .das, .dat, .dazip, .db, .db0, .db3, .dba, .dbf, .dbx, .db_journal, .dc2, .dcr, .dcs, .ddd, .ddoc, .ddrw, .dds, .der, .des, .desc, .design, .dgc, .dir, .dit, .djvu, .dmp, .dng, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .drf, .drw, .dtd, .dwg, .dxb, .dxf, .dxg, .easm, .edb, .efx, .eml, .epk, .eps, .erbsql, .erf, .esm, .exf, .fdb, .ff, .ffd, .fff, .fh, .fhd, .fla, .flac, .flf, .flv, .flvv, .forge, .fos, .fpk, .fpx, .fsh, .fxg, .gdb, .gdoc, .gho, .gif, .gmap, .gray, .grey, .groups, .gry, .gsheet, .h, .hbk, .hdd, .hkdb, .hkx, .hplg, .hpp, .htm, .html, .hvpl, .ibank, .ibd, .ibz, .icxs, .idml, .idx, .iff, .iif, .iiq, .incpas, .indb, .indd, .indl, .indt, .inx, .itdb, .itl, .itm, .iwd, .iwi, .jar, .java, .jnt, .jpe, .jpeg, .jpg, .js, .kc2, .kdb, .kdbx, .kdc, .key, .kf, .kpdx, .kwm, .laccdb, .layout, .lbf, .lck, .ldf, .lit, .litemod, .log, .lrf, .ltx, .lua, .lvl, .m, .m2, .m2ts, .m3u, .m3u8, .m4a, .m4p, .m4u, .m4v, .map, .max, .mbx, .mcmeta, .md, .mdb, .mdbackup, .mdc, .mddata, .mdf, .mdi, .mef, .menu, .mfw, .mid, .mkv, .mlb, .mlx, .mmw, .mny, .mos, .mov, .mp3, .mp4, .mpa, .mpeg, .mpg, .mpp, .mpqge, .mrw, .mrwref, .msg, .myd, .nc, .ncf, .nd, .ndd, .ndf, .nef, .nk2, .nop, .nrw, .ns2, .ns3, .ns4, .nsd, .nsf, .nsg, .nsh, .ntl, .nvram, .nwb, .nx2, .nxl, .nyf, .oab, .obj, .odb, .odc, .odf, .odg, .odm, .odp, .ods, .odt, .ogg, .oil, .orf, .ost, .otg, .oth, .otp, .ots, .ott, .p12, .p7b, .p7c, .pab, .pages, .pak, .pas, .pat, .pcd, .pct, .pdb, .pdd, .pdf, .pef, .pem, .pfx, .php, .pif, .pkpass, .pl, .plb, .plc, .plt, .plus_muhd, .pmd, .png, .po, .pot, .potm, .potx, .ppam, .ppj, .ppk, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .prel, .prf, .prproj, .ps, .psafe3, .psd, .psk, .pst, .ptx, .pwm, .py, .qba, .qbb, .qbm, .qbr, .qbw, .qbx, .qby, .qcow, .qcow2, .qdf, .qed, .qic, .r3d, .ra, .raf, .rar, .rat, .raw, .rb, .rdb, .re4, .rgss3a, .rim, .rm, .rofl, .rtf, .rvt, .rw2, .rwl, .rwz, .s3db, .safe, .sas7bdat, .sav, .save, .say, .sb, .sd0, .sda, .sdf, .ses, .shx, .sid, .sidd, .sidn, .sie, .sis, .sldasm, .sldblk, .sldm, .sldprt, .sldx, .slm, .snx, .sql, .sqlite, .sqlite3, .sqlitedb, .sr2, .srf, .srt, .srw, .st4, .st5, .st6, .st7, .st8, .stc, .std, .sti, .stl, .stm, .stw, .stx, .sum, .svg, .swf, .sxc, .sxd, .sxg, .sxi, .sxm, .sxw, .syncdb, .t12, .t13, .tap, .tax, .tex, .tga, .thm, .tif, .tlg, .tor, .txt, .upk, .v3d, .vbox, .vcf, .vdf, .vdi, .vfs0, .vhd, .vhdx, .vmdk, .vmsd, .vmx, .vmxf, .vob, .vpk, .vpp_pc, .vtf, .w3x, .wab, .wad, .wallet, .wav, .wb2, .wma, .wmo, .wmv, .wotreplay, .wpd, .wps, .x11, .x3f, .xf, .xis, .xla, .xlam, .xlk, .xll, .xlm, .xlr, .xls, .xlsb, .xlsb3dm, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .xqx, .xxx, .ycbcra, .yuv, .zip, .ztmp
Popcorn Time file-locking virus appends .filock extension to the encrypted files. For example, File.docx, after having been encrypted, will be renamed as File.docx.filock. The encryption is followed by the conversion of the two base64 strings into two files, one in the HTML file format, the other in the TXT file format, which contain the ransom note and are named by one and the same name, that of the restore_your_files.
The lock screen displayed by Popcorn Time ransomware:
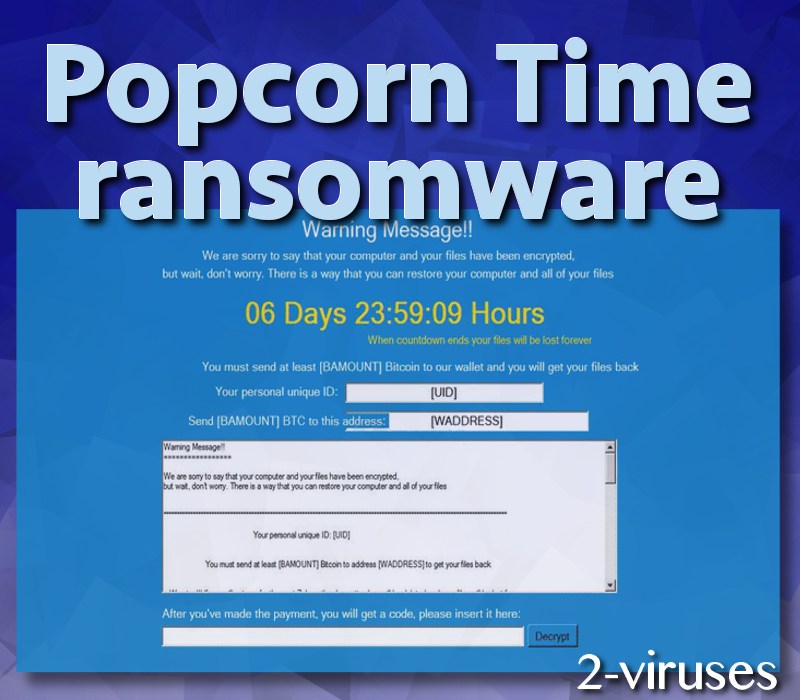
The text of the screen:
Warning Message!!
We are sorry to say that your computer and your files have been encrypted,
but wait, don’t worry. There is a way that you can restore your computer and all of your files
06 Days 23:59:09 Hours
When countdown ends your files will be lost forever
You must send at least [BAMOUNT] Bitcoin to our wallet and you will get your files back
Your personal unique ID: [UID]
Send [BAMOUNT] BTC to this address: [WADDRESSS]
After you’ve made the payment, you will get a code, please insert it here:
The automatically displayed HTML message looks the following:
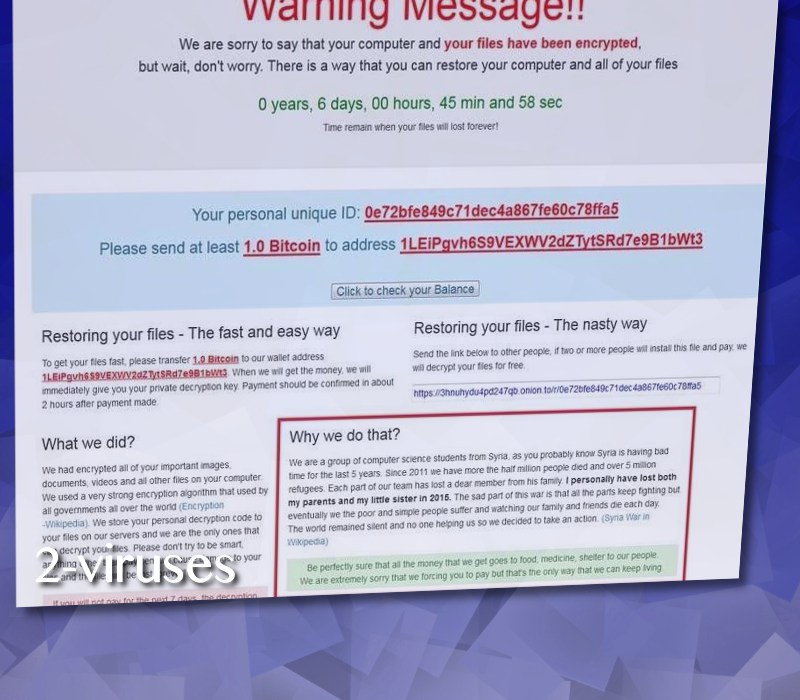
The text it contains:
Restoring your files – The fast and easy way
To get your files fast, please transfer 1.0 Bitcoin to our wallet address
1LeiPgvh6S9VEXWV2dZTytSRd7e9B1bWt3. When we will get the money, we will
immediately give you your private decryption key. Payment should be confirmed in about
2 hours after payment made.What we did?
We had encrypted all of your important images,
documents, videos and all other files on your computer.
We used a very strong encryption algorithm that used by
all governments all over the world (Encryption – Wikipedia).
We store your personal decryption code to
your files on our servers and we are the only ones that
can decrypt your files. Please don’t try to be smart,
anything other than payment will cause damage to your
files and the files will be lost forever!!!
If you will not pay for the next 7 days, the decryption
key will be deleted and your files will be lost forever.Restoring your files – The nasty way
Send the link below to other people, if two or more people will install this file and pay, we
will decrypt your files for free.
https://3hnuhydu4pd247qb.onion.to/r/0e72bfe849c71dec4a867fe60c78ffa5Why we do that?
We are a group of computer science students from Syria, as you probably know Syria is having bad
time for the last 5 years. Since 2011 we have more the half million people died and over 5 million
refugees. Each part of our team has lost a dear member from his family. I personally have lost both
my parents and my little sister in 2015. The sad part of this war is that all the parts keep fighting but
eventually we the poor and simple people suffer and watching our family and friends die each day.
The world remained silent and no one helping us so we decided to take an action. (Syria War in
Wikipedia)
Be perfectly sure that all the money that we get goes to food, medicine, shelter to our people.
We are extremely sorry that we forcing you to pay but that’s the only way that we can keep living.
7 days are given to pay the ransom of 1BTC to the 1LEiPgvh6S9VEXWV2dZTytSRd7e9B1bWt3 BTC address. 1 Bitcoin is worth 769.95 USD at this point in time. So this is the amount of money the encrypted files are valued. Interestingly, during the encryption, Popcorn Time virus will display a fake downloading screen, which will state the following:
Downloading and Installing
Please wait…
In addition to this, the malware have the certain strings in its code, which automatically deletes your files, if you enter the wrong decryption code for 4 times. On the final notes of Popcorn Time crypto-virus, it adds the following registry key to appear on the startup:
HKCUSOFTWAREMicrosoftWindowsCurrentVersionRun “Popcorn_Time” [path_to]popcorn_time.exe
And it communicates with the following servers:
https://3hnuhydu4pd247qb.onion.to
http://popcorn-time-free.net
How to Remove Popcorn Time Ransomware and Decrypt the Files?
For the removal of Popcorn Time ransomware download Spyhunter or Malwarebytes antivirus applications. You will also find the manual removal instructions at the end of the article, however, be very careful, if you decide to implement the manual removal of the malware. Either the automatic or manual removal of the ransomware must be done after the imaging of the encrypted data storage/-s.
For the decryption of the encrypted files, you can only use the general methods of the data restore, as there has not a decryptor from the trusted sources released yet. The trusted sources are the security companies and individual security researchers, but not the hackers of Popcorn Time ransomware, which under no means could be called a trusted source. The general file recovery techniques include the following: shadow copies, unmapped removable drives and data recovery software.
As regards the distribution of Popcorn Time ransomware, the specific methods employed to distribute the malware by its developers have not been disclosed yet. It has not been confirmed yet whether some fake version of the Popcorn Time movie downloading and streaming application is involved in its distribution. Thus, users are recommended to remain extra cautions as concerns the traditional sources of ransomware infections that are infected spam e-mails, fake downloads and compromised domains.
Popcorn Time Ransomware quicklinks
- How does Popcorn Time Ransomware Infect the Systems?
- How to Remove Popcorn Time Ransomware and Decrypt the Files?
- Automatic Malware removal tools
- How to recover Popcorn Time Ransomware encrypted files and remove the virus
- Step 1. Restore system into last known good state using system restore
- 1. Reboot your computer to Safe Mode with Command Prompt:
- 2.Restore System files and settings.
- Step 4. Use Data Recovery programs to recover Popcorn Time Ransomware encrypted files
Automatic Malware removal tools
(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
How to recover Popcorn Time Ransomware encrypted files and remove the virus
Step 1. Restore system into last known good state using system restore
1. Reboot your computer to Safe Mode with Command Prompt:
for Windows 7 / Vista/ XP
- Start → Shutdown → Restart → OK.
- Press F8 key repeatedly until Advanced Boot Options window appears.
- Choose Safe Mode with Command Prompt.

for Windows 8 / 10
- Press Power at Windows login screen. Then press and hold Shift key and click Restart.

- Choose Troubleshoot → Advanced Options → Startup Settings and click Restart.
- When it loads, select Enable Safe Mode with Command Prompt from the list of Startup Settings.

2.Restore System files and settings.
- When Command Prompt mode loads, enter cd restore and press Enter.
- Then enter rstrui.exe and press Enter again.

- Click “Next” in the windows that appeared.

- Select one of the Restore Points that are available before Popcorn Time Ransomware has infiltrated to your system and then click “Next”.

- To start System restore click “Yes”.

Step 2. Complete removal of Popcorn Time Ransomware
After restoring your system, it is recommended to scan your computer with an anti-malware program, like Spyhunter and remove all malicious files related to Popcorn Time Ransomware. You can check other tools here.Step 3. Restore Popcorn Time Ransomware affected files using Shadow Volume Copies
If you do not use System Restore option on your operating system, there is a chance to use shadow copy snapshots. They store copies of your files that point of time when the system restore snapshot was created. Usually Popcorn Time Ransomware tries to delete all possible Shadow Volume Copies, so this methods may not work on all computers. However, it may fail to do so. Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8. There are two ways to retrieve your files via Shadow Volume Copy. You can do it using native Windows Previous Versions or via Shadow Explorer. a) Native Windows Previous Versions Right-click on an encrypted file and select Properties → Previous versions tab. Now you will see all available copies of that particular file and the time when it was stored in a Shadow Volume Copy. Choose the version of the file you want to retrieve and click Copy if you want to save it to some directory of your own, or Restore if you want to replace existing, encrypted file. If you want to see the content of file first, just click Open.
b) Shadow Explorer It is a program that can be found online for free. You can download either a full or a portable version of Shadow Explorer. Open the program. On the left top corner select the drive where the file you are looking for is a stored. You will see all folders on that drive. To retrieve a whole folder, right-click on it and select “Export”. Then choose where you want it to be stored.

Step 4. Use Data Recovery programs to recover Popcorn Time Ransomware encrypted files
There are several data recovery programs that might recover encrypted files as well. This does not work in all cases but you can try this:- We suggest using another PC and connect the infected hard drive as slave. It is still possible to do this on infected PC though.
- Download a data recovery program.
- Install and scan for recently deleted files.








