Petya ransomware is newly released ransomware virus most popular in Germany, yet users from other countries might get infected as well. Ransomware message is written in English, so obviously it is targeted not only to Germany.
Petya ransomware operates differently from other ransomware infections. It encrypts whole hard disk rather than separate files. So your Computer becomes completely unusable and won’t boot to Windows till the disk is unencrypted or ransom is paid. Thus, no regular ransomware encryption software will work.
Petya Ransomware quicklinks
- Operation processes of Petya
- Many versions of Petya
- How to decrypt your files
- Automatic Malware removal tools

(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
So eventually if your computer is infected with this virus, it might result in permanent loss of your files and other viruses being infiltrated into your system. However, there is something that you can do in order to minimize the damage caused by Petya, yet you need to know how it operates and what options work the best.
This blog post is dedicated to this cause – to provide you with useful information about Petya and possible solutions to recover your files and remove the virus itself.
Operation processes of Petya
The basic scheme of how the virus works looks something like this:
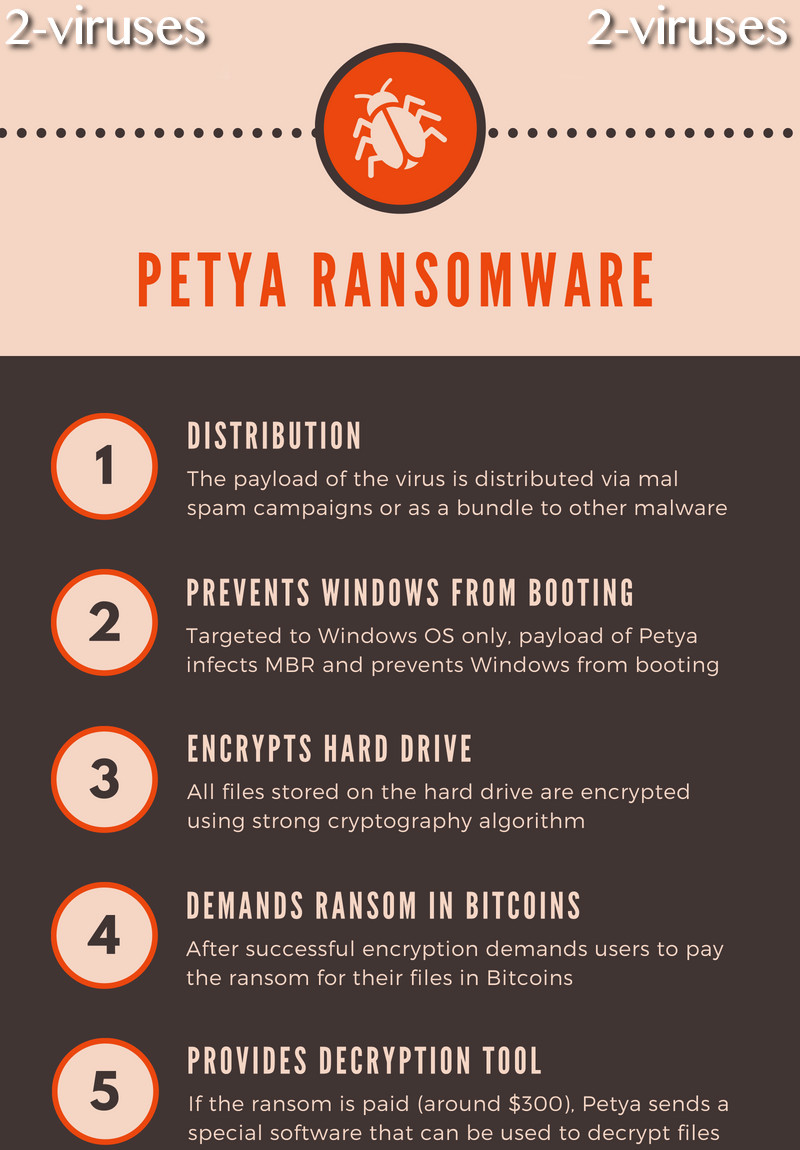
In most cases, Petya was distributed as PDF. Once the attachment was opened, the payload would be automatically uploaded and processes displayed in the infographic above would take place.
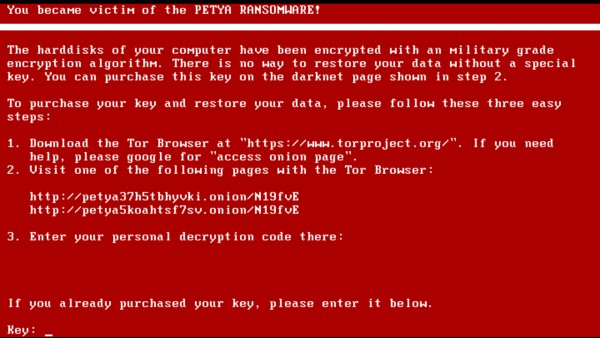
Once encryption of your disk is over, your computer will reboot automatically and your desktop wallpaper will be changed to this message:
It says:
You became victim of the PETYA RANSOMWARE!
The hard disks of your computer have been encrypted with an military grade encryption algorithm. There is no way to restore your data without a special key. You can purchase this key on the darkness page shown in step 2.
To purchase your key and restore your data, please follow these three easy steps:
- Download the Tor Browser at “https://www.torproject.org/” If you need help, please google for “access onion page”.
- Visit one of the following pages with the Tor Browser:
http://petya37h5tbhyvki.onion/N19fvE
http://petya5koahtsf7sv.onion/N19fvE- Enter your personal decryption code there:If you already purchase your key, please enter it below:
Key: _
Usually, this ransomware travels vie shared files on Dropbox. You should receive an email with invitation to view a file on dropbox and if you open it, the virus will automatically infect your system.
However, Petya ransomware only encrypts files stored on your hard drive, so files stored on shared network or cloud storage should not be affected.
Many versions of Petya
The virus is notorious not only for the high volume of computers it managed to infect but also an outburst of following viruses that were basically modified versions of Petya. All of those viruses went by the same logic – infect computers, lock personal files and demand for a ransom.
NotPetya virus is even worse than original Petya because it is categorized aswiper. I.e. this infection intentionally fails to create a tool that would allow restoring locked files. They are not interested in money, they just want to see users suffer and lose their files for good. Even though most of wiper ransomware infections simply delete all personal files from a hard drive, NotPetya seems to encrypt them instead.
Petya+ was released quickly after NotPetya virus as an attempt to take advantage of the well-known name and make some more fuss. Fortunately for users and unfortunately for developers of Petya+, they failed to create a successful distribution scheme and were soon tracked down. This infection was operating as screen locker and didn’t have encryption mechanism. Instead of that, they tried to swindle money from users by simply locking their screens and displaying misleading information.
There are also other viruses that were inspired by Petya, named after Petya or even made by the same crooks that made Petya.
How to decrypt your files
To eliminate the damage done by this virus, you should remove Petya ransomware from your computer and restore your files. To unlock files encrypted by Petya ransomware, you can pay the ransom and purchase the decryption key or restore them from a backup copy of your hard drive.
You can also use this Leostone and try to determine the decryption key. To use this tool, you will need to attach the drive affected by Petya ransomware to another computer and extract specific data from it. Fabian Wosar, a security researcher, has developed Petya which can collect data that is required to use Leostone tool. Just load your hard drive on an uninfected system and then run Petya Sector Extractor. Once it generates the data you need, copy paste it and run Leostone tool. It will generate a unique decryption key which you can use to decrypt your files. Beware that the creators of Petya ransomware can modify the code so that these tools would not work. So if you became a victim of this ransomware, be sure to run these tools as soon as possible.
Update as of July 11, 2017: decryption key for older Petya Ransomware version was released, it can be found here: New. However, it won’t work for those of you who were infected by the end of June, beginning of July 2017, because that’s when Petya was updated.
After you decrypt the hard drive, we recommend scanning PC with anti-malware tools ( Spyhunter, hitman ) to determine the way you got infected by Petya virus. This is important to prevent reinfection and other computer parasites.
On June 2017 Petya ransomware resurfaced again. We are still investigating if it is same or different version and if the removal procedure still work.

To secure your device from Petya, we are presenting you with reliable guidelines. Since there appears to be no kill switch that could be exploited to prevent Petna (NotPetya) from terrorizing Internet users, it is necessary to complete this tutorial to be safe.
1. Configure Windows to display file extensions. It is important to be sure that “Folder Options” would not be set to “Hide Extension for known file types”. Set is as seen in the table below.
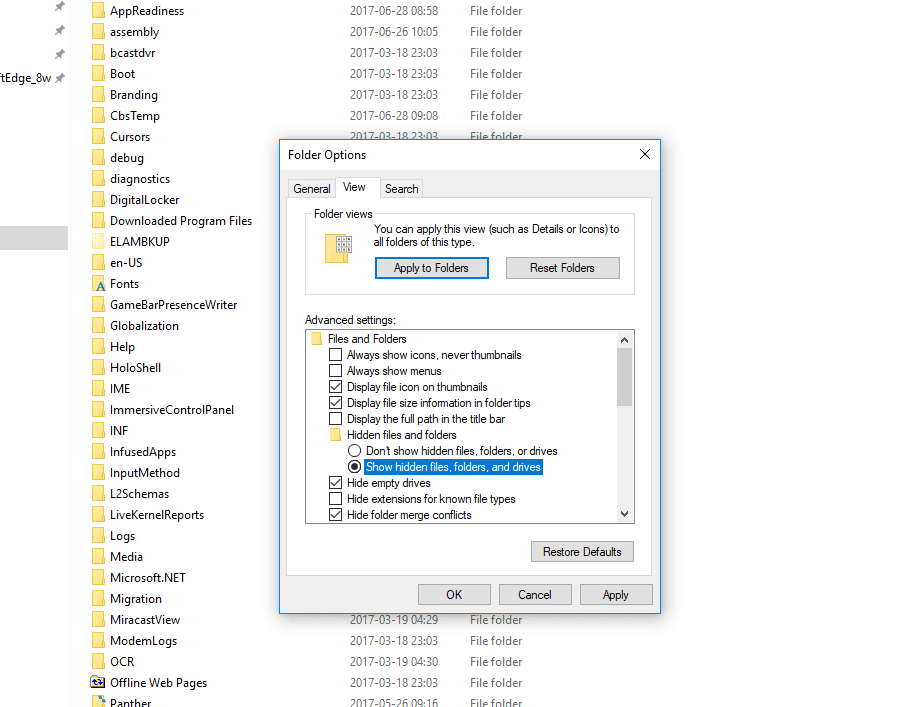
2. Now, C:\Windows folder should be launched.
3. Find notepad.exe entry in the latter folder.

4. This executable should be left-clicked. After than, hold a combination of CTRL+C to copy it ant CTRL+V to paste it.

5. Immediately after that you should see a table that requires you to provide administrator permission to copy to this folder.
6. Select continue.
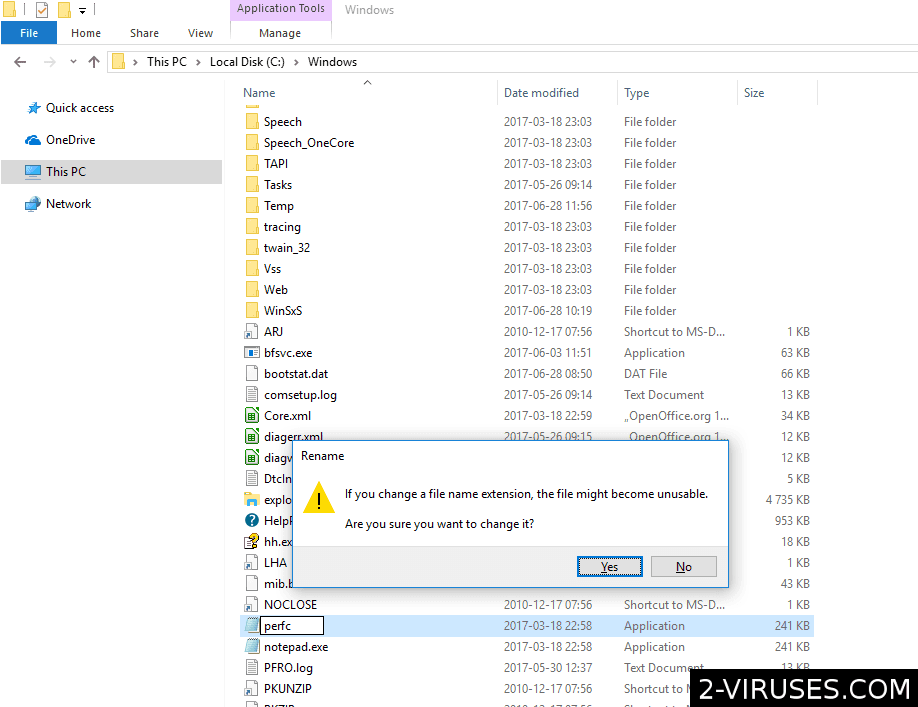
7. A new file should be noticed with the title of notepad – Copy.exe. Then, left-click on it and press F2 to rename the file. Instead of the notepad – Copy.exe title, write “perfc”. Press enter.

8. A table should appear, requiring you to confirm the modification you made to the file name. Press yes. Operating system will display another requirement for consent: click continue on it.
Now, the new perfc file is ready to be made read-only.
1. Right-click on it and find Properties.

2. A table should launch. Find Attributes in the General section.
3. Select Read-only.

4. Click Apply. Then, the OK button as well.
After finishing this tutorial, you will be protected from the Petya infection! To always be protected from similar infections, try regularly scanning your operating system with a sophisticated anti-malware tool Malwarebytes.
Automatic Malware removal tools
(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
What if a person uses data recovery tool that ignores MFT and looks through the disk? Can it still work in order to get back my files?
I have also heard that Leostone tool was created because the Petya hackers made some kind of mistake?
It is possible to use data recovery tools, but it is time consuming and files might be missing some parts. It is easier to use the decryptor as long as it works.
RUSSIA