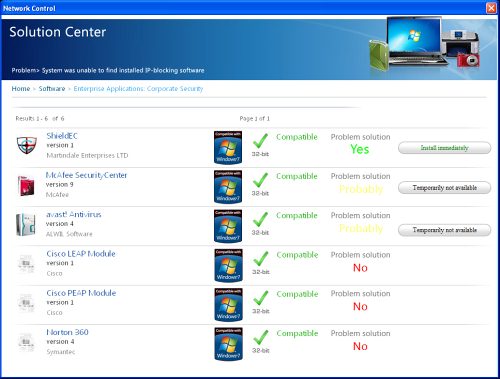
Network Control, sometimes called Network Control Solution Center, is a Trojan that pretends to be a legitimate security application. It states that remote administrator named Adam1 has changed some system files of Windows OS. This ransomaware is promoted mostly through the use of fake online scanners and other bogus websites which state that your computer is infected with spyware, adware, Trojans and other malware. It may also come bundled with other viruses or enter your computer through software vulnerabilities. Once installed, Network Control will state that your computer is not protected and that there is no firewall software on your PC. Then it will display Solution Center screen with a list of fake antivirus programs: Advanced Net Firewall, Shield EC, Personal Network Protect, IP Blockator, and Network Defender. Please don’t buy any of those programs. They are all bogus and won’t protect your computer in any way. Instead, please use the removal instructions below to remove Network Control and any related malware form your computer either manually or with an automatic removal tool.
The main process of NetworkControl is NC.exe located in C:\NetworkControl folder. This process launch automatically when Windows starts. Another very annoying thing about this virus is that it actually terminates nearly all legitimate programs and displays fake warning with the following text:
System Notification
Running applications blocked by the administrator Adam1.
The text of some of these alerts are:
Unable to find installed software
System was unable to find installed firewall software.
System Restore
Critical System Notification
Remote administrator Adam1 has changed some system files of Windows OS.
Checking will take several minutes.
Please do not turn off the computer – it can lead to system crash.
As you can see, Network Control is very annoying and even dangerous application. The main goal of this bogus program is to trick you into purchasing one of the fake antivirus products. If you have already purchased it then please contact your credit card company and dispute the charges. Then, please follow our removal recommendations carefully and remove Network Control from your computer. We strongly recommend you to use an automatic removal in order to completely remove the rogue program and any additional malware.
Automatic Malware removal tools
(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
Just did a cleanup of this. Thanks a million for the info. I’d just like to add that it also appears to hook into winlogon by way of the following registry key:
HKCU\software\microsoft\windows nt\currentversion\winlogon
“Shell” = “C:\NetworkControl\nc.exe -reboot”
Be sure to delete everything in the %tmp% (user temp), temp (system temp), and prefetch directories. I noticed malicious files beginning with ~DF*.tmp files in temp folders.
Also, are you sure the segoeui.ttf font file is malicious? The timestamp on this system leads me to believe it looks legit. I moved it to a quarantine folder anyway.
And finally on this particular system, practically every critical service (in services.msc) were set to disable. She said she had a friend try to fix this so I’d hate to even hazard a guess as to which caused this…the virus or the friend trying to be helpful.
Thanks again.
Royce Renteria
Additionally I determined the system was compromised as a result of a malicious jscript file (named ngjngvjfds) being kicked off from “%userprofile%\application data\AdobeUM\” which then appears to have spawned tmp.exe in the same directory as well as “seventh[2]” in the temp internet files directory. This leads me to assume the attack vector was a malicious adobe-related exploit; probably flash or acrobat.
Our computer received an “adam1” asking for permission. We tried everything suggested on this page and it did not work!!! We then had to purchase Norton. But in order to get on the internet and install it. We kept having to turn off our computer because the virus would seem to shut all computer options down after the computer had been on for 5-10 minutes. It finally got rid of the damn virus!!! According to Norton, it has only been around for about a week and only about 10 people are using it. We HAD TO GET Norton to remove it and still get it installed in the short timelines of turning our computer on and off.
Network control is more widely spread than 10 people. Apparently, there are couple versions of it.
I’m currently trying to clean this up on my mom’s computer. I think she got it from a link that came in a spoofed email from a friend of her’s.
It’s proving impossible. For one, the processes aren’t even showing up when I go into the task manager or through msconfig. They must start up with the trojan at some point…usually it appears about 4 or 5 minutes after you boot up the computer.
I went into regedit and I can’t find those registry entries at all. I ran a hijack this scan and…nothing.
Additionally, I have found where the program resides but it won’t let me remove them – even in safe mode and even when I take the computer offline.
I tried to repair the registry by rewriting it from the Windows cd…but it just starts right back up as soon as the computer reboots. I’m thinking that I’m probably just going to have to wipe her C drive out in order to get rid of this. On any given day, a quick scan of Malwarebytes could take about 10 minutes to perform. This virus doesn’t give you 10 minutes to do anything once you boot up so I can’t even complete a scan.
Carla : Could you list the location where the virus installed?
UPDATE: the source of this infection for the system I cleaned was a JAVA exploit for the 1st vector; I believe the Adobe vectors were subsequently used to further compromise the system. Both java and adobe apps on the system were severely out of date creating an extremely huge attack surface. It was only a matter of time. I uninstalled all of them and deleted java cache. She mentioned something about Adam as well, but I never saw it. After I had it cleaned up I was doing one final online-based scan overnight. Next morning it was fully compromised all over again. Come to find out she had the Alureon TDL3 TDSS rootkit. What a pain!!! No doubt it had the hidden encrypted virtual drive on “empty” arbitrary sectors toward the end of the hard drive. I cleaned up again using a PE (this way the rootkit compromised OS can’t hide malicious files as easily), manually cleaned it again (including offline registry editing) and then ran a disk erasing util to flip all bits to zero on the empty sectors of the drive. Ran scans including TDSS killer to help rid the residual malware and rootkit files. 2 days later constantly connected to the internet and running various online (and offline) scans and does not appear infected again. Even after reloading flash and acrobat (for which there is presently a zero day). She doesn’t need java so why expose her to those threats. Left it off.
Carla – if you’re only using antimalware tools to attack this, you’ll have a heck of a time, especially if yours has a TDL3 rootkit too. It may be worth it to reinstall. If this one I’m working on acts up again, I’m backing up her docs and favorites, slaving the drive to another machine, formatting it, debian wiping it to overwrite hidden encrypted virtual disks in “empty” sectors, and reinstalling windows. Best of luck.
Royce: I would recommend running TDSS killer on any system infected by rogues by default, as too many of them come with tdss rootkits.
Help me, have a pc with windows 7 64bit with this problem :s:s can’t reboot my system, don’t know what to do. HELP
Barend: If your PC no longer boots in normal and safe mode, you will have to bring it to repair shop. If it boots, try booting into safe mode (press F8 while booting). Then run msconfig and disable all startup entries from home directory. Then scan with our scanners.