An offensive crypto-virus has emerged and it goes by the name of Malabu ransomware. AES algorithm for encryption help this virus gain some leverage, but Malabu did not take long to lose it. Considering, this is a poorly-written ransomware, based on the HiddenTear open source code. Additionally, the infection was revealed not to generate unique encryption/decryption keys. This means that a static key is utilized; this also translates into another positive news. Skilfully, security researchers updated their StupidDecryptor (the download process will begin immediately after you click on this shortcut) which is capable of reversing the effects that a number of ransomware infections have brought. From the tittle of the tool for decryption you should be able to tell that the addressed infections are shabby and would not be classified as sophisticated samples of malware.
Traits of Malabu ransomware
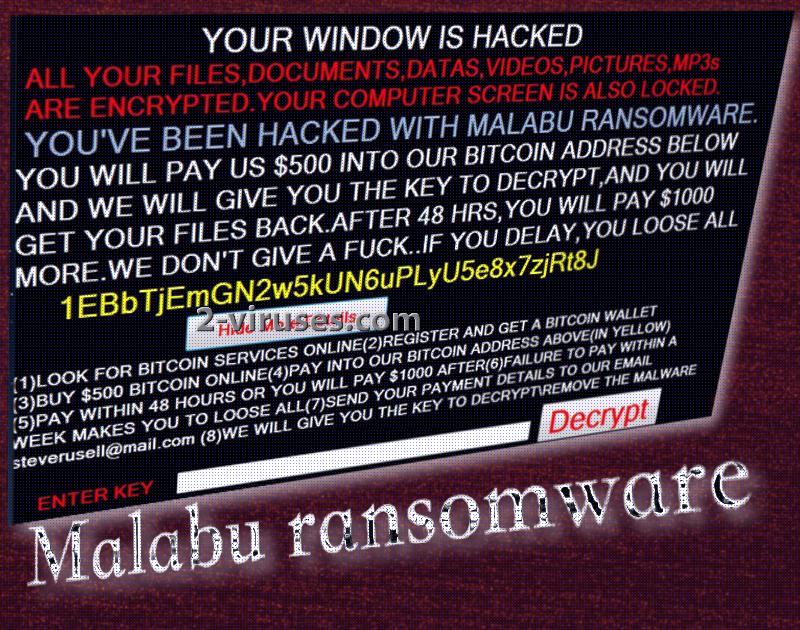
We have already briefly mentioned several features of Malabu cryto-virus, reminding users that ransomware, based on the open source project, is still being developed. These variants usually use AES encryption and so does Malabu sample. Infection also features a lock-screen which prevents victims from accessing their entire operating system. The image below displays the message which is seen once a device is locked. Malabu rasomware expresses demands for 500 US dollars to be send via bitcoin payment system. According to the latest rates, 0.41494 equals the required sum. If demands are not carried out in the next 48 hours after the lock-screen is displayed, the ransom doubles.
Malabu virus leaves an email address to receive letters from victims that have obediently followed the listed orders. [email protected] is the account, controlled by the creators of Malabu infection. Could it be that the hacker used his own name, Steve Rusell? The reasons for using a real name in the contact address remain unknown. In other news, Malabu crypto-virus proceeds similarly to Rijndael infection. How? They both append .fucked extension to the encrypted data and this is rather inappropriate. However, actions of ransomware creators are all shameless.
After looking at the sample of Malabu crypto-virus, we have determined that Malabu-X.exe is its payload. After it obtains a position in a device, the payload will begin its vicious activity, starting from making modifications to Windows Registry Keys. Ransomware has to complete this modification if the payload is to run automatically in the background, conclude encryption and present a screen-locker. Thankfully, this variant is not to be feared as a specific decryptor has already been indicated as capable of restoring files that Malabu ransomware encoded. Do NOT pay the ransom and click download to get the tool for decryption!
How to protect your files from Malabu ransomware and other variants of this malware group?
Malabu crypto-virus can be averted if you use appropriate security measures for your data. There are all sorts of online backup storages that will keep your files safe. Make sure you choose a reliable service to be guaranteed that your data is properly protected. Pay attention to reviews from security researchers and former/current users of a specific online backup storage. An alternative is to place your files into USB flash drives. The problem with this is that people tend to plug in these drives and leave them connected to their computers. Many ransomware variants are capable of encrypting data on all connected resources, including USB flash drives.
Ways to become infected with Malabu ransomware
If you catch Malabu crypto-virus, consider yourself lucky: not all infections are decryptable. There are a lot of sources to receive these viruses from and people are advised to pay special attention during their browsing. For example, email facilities can assist in hackers’ plans of distributing malware. Malicious documents and other files could be appended as attachments to email letters that are to be sent around to random people. If you happen to receive questionable email letters, allegedly addressing urgent matters, always be certain that they are sent from official email addresses. Additionally, ransomware could be spread via vulnerable websites, affected by exploit kits.
With the increasing amount of malware threats, users are recommended to secure their devices with reliable security software. Before proceeding to decrypt files with the tool that was mentioned before, there is still one task you must complete. Of course, we are referring to the fact that you have to remove the infection in advance. Spyhunter, Plumbytes and Malwarebytes will detect all threats and offer quick removal.
Malabu Ransomware quicklinks
- Traits of Malabu ransomware
- How to protect your files from Malabu ransomware and other variants of this malware group?
- Ways to become infected with Malabu ransomware
- Automatic Malware removal tools
- How to recover Malabu ransomware encrypted files and remove the virus
- Step 1. Restore system into last known good state using system restore
- 1. Reboot your computer to Safe Mode with Command Prompt:
- 2.Restore System files and settings.
- Step 4. Use Data Recovery programs to recover Malabu ransomware encrypted files
Automatic Malware removal tools
(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
How to recover Malabu ransomware encrypted files and remove the virus
Step 1. Restore system into last known good state using system restore
1. Reboot your computer to Safe Mode with Command Prompt:
for Windows 7 / Vista/ XP
- Start → Shutdown → Restart → OK.
- Press F8 key repeatedly until Advanced Boot Options window appears.
- Choose Safe Mode with Command Prompt.

for Windows 8 / 10
- Press Power at Windows login screen. Then press and hold Shift key and click Restart.

- Choose Troubleshoot → Advanced Options → Startup Settings and click Restart.
- When it loads, select Enable Safe Mode with Command Prompt from the list of Startup Settings.

2.Restore System files and settings.
- When Command Prompt mode loads, enter cd restore and press Enter.
- Then enter rstrui.exe and press Enter again.

- Click “Next” in the windows that appeared.

- Select one of the Restore Points that are available before Malabu virus has infiltrated to your system and then click “Next”.

- To start System restore click “Yes”.

Step 2. Complete removal of Malabu ransomware
After restoring your system, it is recommended to scan your computer with an anti-malware program, like Spyhunter and remove all malicious files related to Malabu virus. You can check other tools here.Step 3. Restore Malabu ransomware affected files using Shadow Volume Copies
If you do not use System Restore option on your operating system, there is a chance to use shadow copy snapshots. They store copies of your files that point of time when the system restore snapshot was created. Usually Malabu virus tries to delete all possible Shadow Volume Copies, so this methods may not work on all computers. However, it may fail to do so. Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8. There are two ways to retrieve your files via Shadow Volume Copy. You can do it using native Windows Previous Versions or via Shadow Explorer. a) Native Windows Previous Versions Right-click on an encrypted file and select Properties → Previous versions tab. Now you will see all available copies of that particular file and the time when it was stored in a Shadow Volume Copy. Choose the version of the file you want to retrieve and click Copy if you want to save it to some directory of your own, or Restore if you want to replace existing, encrypted file. If you want to see the content of file first, just click Open.
b) Shadow Explorer It is a program that can be found online for free. You can download either a full or a portable version of Shadow Explorer. Open the program. On the left top corner select the drive where the file you are looking for is a stored. You will see all folders on that drive. To retrieve a whole folder, right-click on it and select “Export”. Then choose where you want it to be stored.

Step 4. Use Data Recovery programs to recover Malabu ransomware encrypted files
There are several data recovery programs that might recover encrypted files as well. This does not work in all cases but you can try this:- We suggest using another PC and connect the infected hard drive as slave. It is still possible to do this on infected PC though.
- Download a data recovery program.
- Install and scan for recently deleted files.