LockeR ransomware virus uses a very straight-forward name, considering the fact that the infection encodes data with a combination of RSA-2048 and AES-256 algorithms for encryption. Just like with the My Decryptor crypto-malware, victims of Locker will also be urged to enter one of the Lockerrwhuaf2jjx.onion.link TOR websites for more explicit instructions and demands.
The primary information is provided in a [How_To_Decrypt_Files].txt executable which will presumably be placed in a location that is easily noticeable (for instance, desktop). Since the ransomware (What is ransomware?) is not reported to append an original extension to the files, you should recognize it from the .txt file and the TOR website it is linked to. With the growing threat of ransomware infections, you should be aware of the newest infections, their traits and ways to avoid it.
Symptoms of LockeR crypto-virus and ways to recognize it
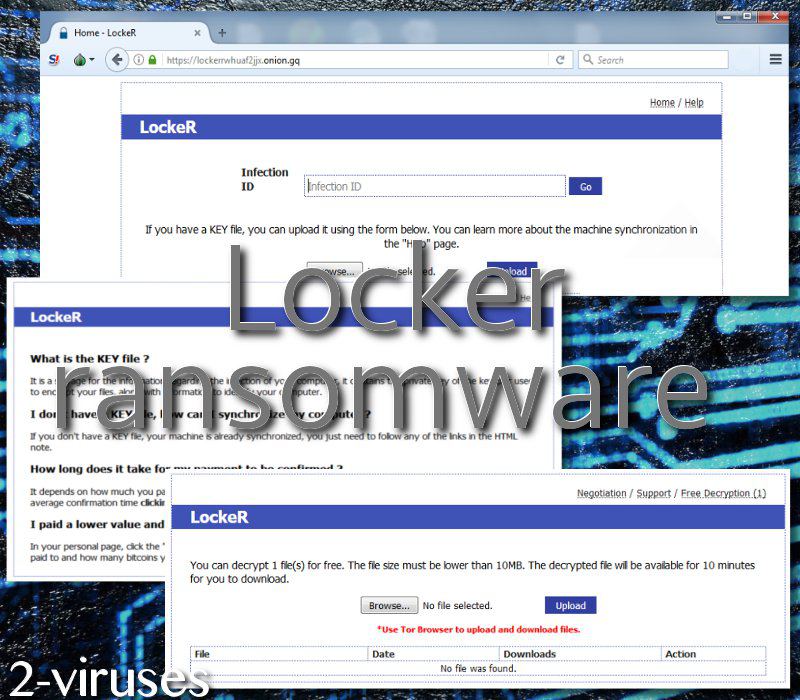
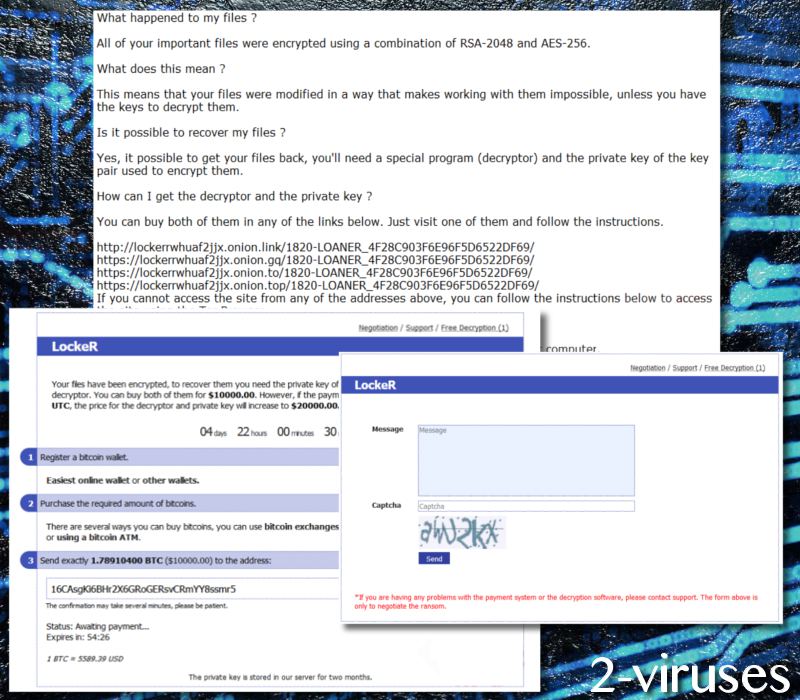
In the launched TOR domain, users are required to type in their infection ID. Then, they are presented with the requirements to have encrypted digital data recovered. Authors of LockeR crypto-malware are especially greedy as they are demanding 1.78910400 BTC which is approximately $9544.67. Of course, infections like BitPaymer also stood out with their demanded ransoms. This is a gigantic sum and we hope that none of the victims will feel desperate enough to buy this this amount of bitcoins and make a transaction to 16CAsgKi6BHr2X6GRoGERsvCRmYY8ssmr5 wallet. However, if the sum is not paid until the given deadline comes, the price will double.
Also, LockeR gives users a chance to recover one encoded file. The executable has to correspond with one rule: it has to be smaller than 10 MB. In addition to this TOR website, the ransomware also has a support service which is supposed help victims send the ransoms or decrypt their files. However, since hackers are not worthy of trust, we do not think that paying the ransom can be indicated as the best choice (When ransomware strikes, should you pay?).
Paying the ransom: not the best idea
In this case, paying the demanded ransom is impossible for many users since not everyone has nearly $10000 just laying around the house. Therefore, file-recovery by paying the fee is not feasible. However, even if you do have the resources to pay hackers off, we do not think that this is the best option to go with. If you have not noticed, but ransomware industry is booming and dozens of new infections begin circulating with every new week. If users would stop paying ransoms, these infections would lose their ability to profit.
Nevertheless, people are still neglecting a very important activity: storing important executables into backup storages or other safe locations. Even your USB flash drive will do if you will not keep it connected to the operating system at all times. If you manage to upload files into an alternative location, then ransomware infection will no longer pose as a threat. Since you will have an addition source of files, you can remove the infection and retrieve files into operating system once it is properly cleaned.
What are the main ways to become infected with ransomware infections?
One of the most popular ways to spread ransomware is to send malicious email letters to random online inboxes. Of course, in some cases the campaigns are targeted against particular people, meaning that infections that require higher ransoms might be attempting to infect people of a higher social statuses. We hope you will not open random email messages.
Also, do not decide to download ransom file attachments or follow suspicious links. Hover over the URL and see where it is really going to lead you. It might be that a malicious website will be launched, waiting to find vulnerabilities in operating systems. This means that those domains are hosting exploit kits and hoping to use system flaws for the purpose of distributing malware parasites. To keep operating systems properly-managed, we hope you will run a scan with Spyhunter.
Locker Ransomware 2 quicklinks
- Symptoms of LockeR crypto-virus and ways to recognize it
- Paying the ransom: not the best idea
- What are the main ways to become infected with ransomware infections?
- Automatic Malware removal tools
- How to recover LockeR ransomware encrypted files and remove the virus
- Step 1. Restore system into last known good state using system restore
- 1. Reboot your computer to Safe Mode with Command Prompt:
- 2.Restore System files and settings.
- Step 4. Use Data Recovery programs to recover LockeR ransomware encrypted files
Automatic Malware removal tools
(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
How to recover LockeR ransomware encrypted files and remove the virus
Step 1. Restore system into last known good state using system restore
1. Reboot your computer to Safe Mode with Command Prompt:
for Windows 7 / Vista/ XP
- Start → Shutdown → Restart → OK.
- Press F8 key repeatedly until Advanced Boot Options window appears.
- Choose Safe Mode with Command Prompt.

for Windows 8 / 10
- Press Power at Windows login screen. Then press and hold Shift key and click Restart.

- Choose Troubleshoot → Advanced Options → Startup Settings and click Restart.
- When it loads, select Enable Safe Mode with Command Prompt from the list of Startup Settings.

2.Restore System files and settings.
- When Command Prompt mode loads, enter cd restore and press Enter.
- Then enter rstrui.exe and press Enter again.

- Click “Next” in the windows that appeared.

- Select one of the Restore Points that are available before LockeR ransomware has infiltrated to your system and then click “Next”.

- To start System restore click “Yes”.

Step 2. Complete removal of LockeR ransomware
After restoring your system, it is recommended to scan your computer with an anti-malware program, like Spyhunter and remove all malicious files related to LockeR ransomware. You can check other tools here.Step 3. Restore LockeR ransomware affected files using Shadow Volume Copies
If you do not use System Restore option on your operating system, there is a chance to use shadow copy snapshots. They store copies of your files that point of time when the system restore snapshot was created. Usually LockeR ransomware tries to delete all possible Shadow Volume Copies, so this methods may not work on all computers. However, it may fail to do so. Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8. There are two ways to retrieve your files via Shadow Volume Copy. You can do it using native Windows Previous Versions or via Shadow Explorer. a) Native Windows Previous Versions Right-click on an encrypted file and select Properties → Previous versions tab. Now you will see all available copies of that particular file and the time when it was stored in a Shadow Volume Copy. Choose the version of the file you want to retrieve and click Copy if you want to save it to some directory of your own, or Restore if you want to replace existing, encrypted file. If you want to see the content of file first, just click Open.
b) Shadow Explorer It is a program that can be found online for free. You can download either a full or a portable version of Shadow Explorer. Open the program. On the left top corner select the drive where the file you are looking for is a stored. You will see all folders on that drive. To retrieve a whole folder, right-click on it and select “Export”. Then choose where you want it to be stored.

Step 4. Use Data Recovery programs to recover LockeR ransomware encrypted files
There are several data recovery programs that might recover encrypted files as well. This does not work in all cases but you can try this:- We suggest using another PC and connect the infected hard drive as slave. It is still possible to do this on infected PC though.
- Download a data recovery program.
- Install and scan for recently deleted files.








