A disagreeable and ruthless Kee ransomware virus has emerged. Kee is an eminently despicable infection as it plans to delete all of victims’ files after a countdown hits zero. Astonishingly, this ransomware is not coming after income, but simply wishes to cause despair. From the information that the author of this variant discloses with victims, this ransomware appears to be a result of hatred of mankind. Download-installer.exe appears to be the payload that infiltrates into devices and launches, possibly AES, encryption. After running its sample through a number of anti-malware tools, it was determined that there is a very strong chance that this virus is based on HiddenTear open-source project. Infection exploits .NET framework and has multiple bizarre elements that do not appear to have any specific function.
Peculiar aspects of this ransomware
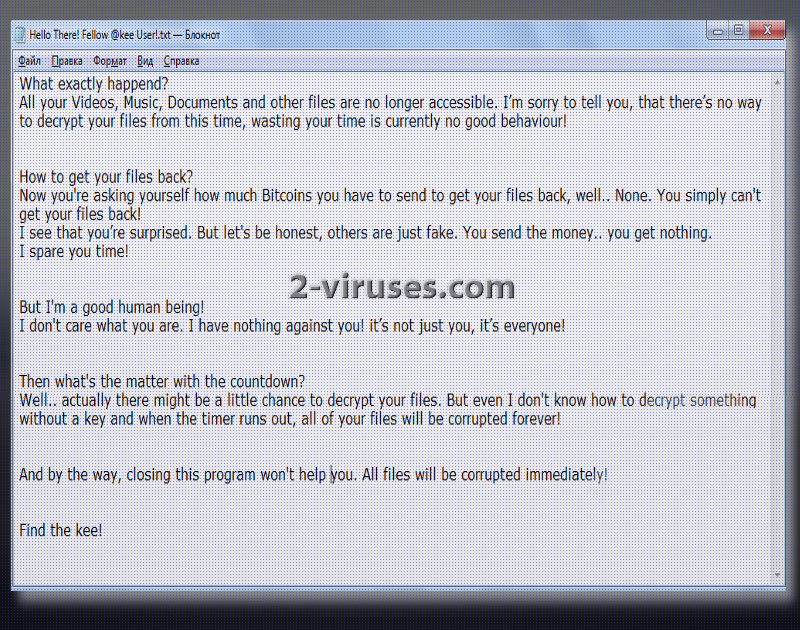
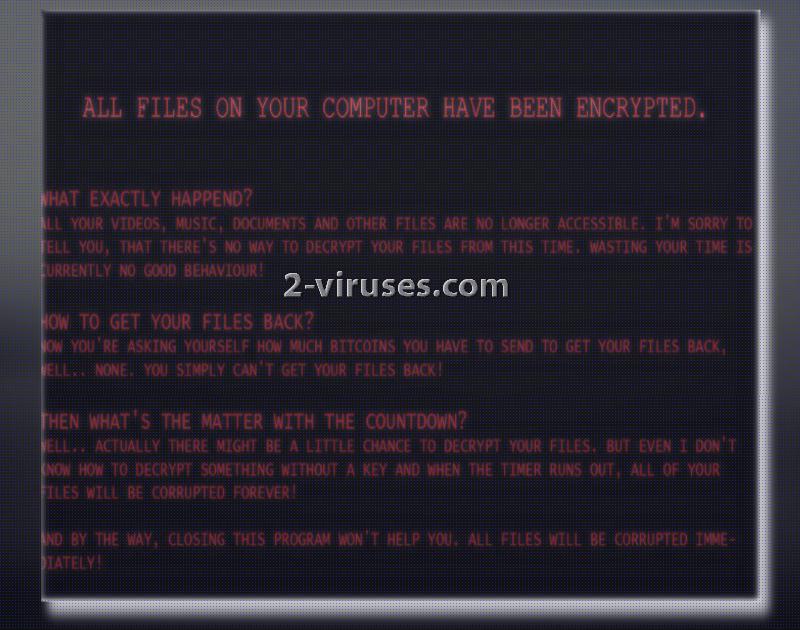
Since the author is not interested in money and revenue, he/she won’t leave any information on how victims can establish contact with the hacker. Instead, a window, a new background and a .txt file that get appended indicate that crook does not even know how to decrypt encoded digital data. The only option for victims is to find an alternative solution until the given time runs out. After that, killsw32l.dll process will delete all of users’ executables without any mercy.
Therefore, there is no support service that hackers would normally provide. According to the hacker, he/she is saving victims’ money and time since developers of ransomware are never planning to decrypt files even if ransoms are paid. This would not be so devastating if this variant would not intend to run a command for the sake of deleting all users’ digital data. Moreover, encrypted material will be separated from the remaining executables with a @kee extension.
After the Download-installer.exe ends up in operating systems, presumably Windows, it will initiate multiple configurations that will finally lead to file encryption and the grand announcement. In this case, crooks do not require anything and simply explain that a ransomware virus has finished file-encryption procedure.
Security researchers, after analyzing the structure of this variant, came to a conclusion that it has some peculiar aspects that are not essential for a ransomware to possess. For instance, there appears to be some secret buttons that would close the malicious program. Additionally, it has a bizarre spread () function, serving no particular purpose.
What are your options for file-recovery?
Since this ransomware is designed to mess with users, only a short amount of time will be given to complete file-decryption. There are no knowledge about whether this infection removes Shadow Volume Copies. Consider this as the option number one. Additionally, you can try universal file-recovery tools that can help decrypt data that has been ruined by a number of crypto-viruses. However, the primary option would be to contact security researchers and ask them to guide you through this difficult situation. If you have valuable data stored and waiting for you in backup storages: you are a lucky user. Simply remove this nasty infection with Spyhunter or Hitman and move onto the file-retrieval from back up storages or USB flash drives.
Tactics that ransomware exploits to infect operating systems
A specific method for distribution has not been determined, but we have a suspicion that this ransomware could be promoted as a free software update. This assumption is made because of the filename of the payload. You are strongly discouraged from downloading programs or patches from random sources. If you do, a variety of viruses could compromise your device. Stay away from online advertisements and unknown websites as they are one of the leading sources of ransomware payloads. You could also receive email letters from bizarre senders, aiming to convince you to download an attachment.
Kee Ransomware quicklinks
- Peculiar aspects of this ransomware
- What are your options for file-recovery?
- Tactics that ransomware exploits to infect operating systems
- Automatic Malware removal tools
- How to recover Kee ransomware encrypted files and remove the virus
- Step 1. Restore system into last known good state using system restore
- 1. Reboot your computer to Safe Mode with Command Prompt:
- 2.Restore System files and settings.
- Step 4. Use Data Recovery programs to recover Kee ransomware encrypted files
Automatic Malware removal tools
(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
How to recover Kee ransomware encrypted files and remove the virus
Step 1. Restore system into last known good state using system restore
1. Reboot your computer to Safe Mode with Command Prompt:
for Windows 7 / Vista/ XP
- Start → Shutdown → Restart → OK.
- Press F8 key repeatedly until Advanced Boot Options window appears.
- Choose Safe Mode with Command Prompt.

for Windows 8 / 10
- Press Power at Windows login screen. Then press and hold Shift key and click Restart.

- Choose Troubleshoot → Advanced Options → Startup Settings and click Restart.
- When it loads, select Enable Safe Mode with Command Prompt from the list of Startup Settings.

2.Restore System files and settings.
- When Command Prompt mode loads, enter cd restore and press Enter.
- Then enter rstrui.exe and press Enter again.

- Click “Next” in the windows that appeared.

- Select one of the Restore Points that are available before Kee virus has infiltrated to your system and then click “Next”.

- To start System restore click “Yes”.

Step 2. Complete removal of Kee ransomware
After restoring your system, it is recommended to scan your computer with an anti-malware program, like Spyhunter and remove all malicious files related to Kee virus. You can check other tools here.Step 3. Restore Kee ransomware affected files using Shadow Volume Copies
If you do not use System Restore option on your operating system, there is a chance to use shadow copy snapshots. They store copies of your files that point of time when the system restore snapshot was created. Usually Kee virus tries to delete all possible Shadow Volume Copies, so this methods may not work on all computers. However, it may fail to do so. Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8. There are two ways to retrieve your files via Shadow Volume Copy. You can do it using native Windows Previous Versions or via Shadow Explorer. a) Native Windows Previous Versions Right-click on an encrypted file and select Properties → Previous versions tab. Now you will see all available copies of that particular file and the time when it was stored in a Shadow Volume Copy. Choose the version of the file you want to retrieve and click Copy if you want to save it to some directory of your own, or Restore if you want to replace existing, encrypted file. If you want to see the content of file first, just click Open.
b) Shadow Explorer It is a program that can be found online for free. You can download either a full or a portable version of Shadow Explorer. Open the program. On the left top corner select the drive where the file you are looking for is a stored. You will see all folders on that drive. To retrieve a whole folder, right-click on it and select “Export”. Then choose where you want it to be stored.

Step 4. Use Data Recovery programs to recover Kee ransomware encrypted files
There are several data recovery programs that might recover encrypted files as well. This does not work in all cases but you can try this:- We suggest using another PC and connect the infected hard drive as slave. It is still possible to do this on infected PC though.
- Download a data recovery program.
- Install and scan for recently deleted files.