A quite offensive ransomware variant has slithered outside hackers’ workshop: Jew Crypt virus. Ethno-religious group of the jewish people now has a crypto-virus named after it and the creators that organized this shallow attack were definitely not trying to praise the latter community. Good news is that this sample is easily treatable so you should not be too concerned over it: at least for the time being. Jew Crypt ransomware still has not been fully prepped and its release from the workshop might have been a simple attempt to test the ropes. For now, security researchers have discovered the secret code which should help victims escape a lock screen of the Jew Crypt virus. A questionable phrase ‘JewsDid911’ should be typed into the blank space and that should do the trick. Hackers responsible for this variant continued to be offensive by providing a defamatory caricature in the lock screen. We certainly hope that these hackers receive no money and their plans to infect devices completely fall through.
Vicious nature of Jew Crypt ransomware
Jew Crypt virus might still be preparing for battle, sharpening its encryption to reach a high-level of complexity. For now, these statements are hypothetical and we are unsure if we will ever have to update this article with a new piece of information. Certainly, we hope that this is going to be the very end of this infection and it will be soon disappear into oblivion. However, if there are any news about Jew Crypt virus vile activity, we are surely going to inform our readers. For now, if you get accidentally infected with this sample and see an annoying lock screen, you should type in ‘JewsDid911’ and it should vanish. You might be confused because a ransom note of Jew Crypt explicitly indicates that all of files in an infected device have been ruined by an unidentified algorithm for encryption. Since the lock screen won’t allow users to access their system, people might just assume that these statements fit the situation. However, Jew Crypt does not seem to initiate actual encryption: its biggest threat is that it blocks access to users’ desktops. Thankfully, this issue can be easily solved by typing the code we have already mentioned several times.
As for the actual infiltration of Jew Crypt virus, it is probably similar to every other ransomware infection. It lands in a device, makes unvalidated changes in Windows Registry Keys in order to run in the background and should turn to scanning for files and their encryption, but sticks to a simple lock screen. As we have mentioned, if there are any news about the future actions of Jew Crypt and its gang, we are going to update our article. Text in the ransom note:
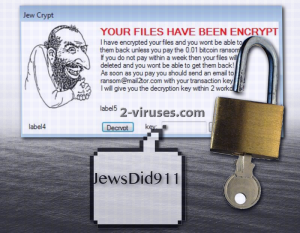
YOUR FILES HAVE BEEN ENCRYPT
I have encrypted your files and you wont be able to get them back unless you pay the 0.01 bitcoin ransomfee! If you do not pay within a week then your files will be deleted and you wont be able to get them back! As soon as you pay you should send and email to [email protected] with your transaction key and I will give you the decryption key within 2 workdays!
label5
label4 Decrypt key: What are bitcoins?
Jew Crypt does not initiate encryption
The price for saving the encrypted files is identified to be 0.01 BTC which equals to 8.99 US dollars. This is one of the lowest fees that we have ever seen: but how can it demand something for a process that is unnecessary? No encryption occurs, for that reason, people should not send money to hackers. Since the price is so low, some might become desperate and pay the money. However, we advise you to use the magic words ‘JewsDid911’ and escape Jew Crypt virus without further complications. If you are worried about getting infected with other variants of ransomware, you should store your files in other locations besides your hard drive.
Traveling habits of Jew Crypt ransomware
It is yet undetermined how Jew Crypt virus specifically infects devices. Since it is assigned to the category of ransomware infections, we can make assumptions. The first one is that the payload travels in infectious spam letters. If you ever notice a message from a source you do not recognize, please do not follow curiosity and open it. If you do that, then at least stay away from the executables that might be attached. Secondly, you should steer clear of websites or downloads that can potentially insert malicious executables into your device.
If you wish to run a scan with a reliable anti-malware tool to guarantee that your device is not infected with malware parasites, you can exploit Spyhunter or Malwarebytes. It will adequately inform you about the system’s condition and offer you removal. If Jew Crypt virus begins to use an algorithm for encryption and encodes files, you would read the following instructions for decryption. The section below also includes step-by-step guide for a manual removal.
Jew Crypt Ransomware quicklinks
- Vicious nature of Jew Crypt ransomware
- Jew Crypt does not initiate encryption
- Traveling habits of Jew Crypt ransomware
- Automatic Malware removal tools
- How to recover Jew Crypt ransomware encrypted files and remove the virus
- Step 1. Restore system into last known good state using system restore
- 1. Reboot your computer to Safe Mode with Command Prompt:
- 2.Restore System files and settings.
- Step 4. Use Data Recovery programs to recover Jew Crypt ransomware encrypted files
Automatic Malware removal tools
(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
How to recover Jew Crypt ransomware encrypted files and remove the virus
Step 1. Restore system into last known good state using system restore
1. Reboot your computer to Safe Mode with Command Prompt:
for Windows 7 / Vista/ XP
- Start → Shutdown → Restart → OK.
- Press F8 key repeatedly until Advanced Boot Options window appears.
- Choose Safe Mode with Command Prompt.

for Windows 8 / 10
- Press Power at Windows login screen. Then press and hold Shift key and click Restart.

- Choose Troubleshoot → Advanced Options → Startup Settings and click Restart.
- When it loads, select Enable Safe Mode with Command Prompt from the list of Startup Settings.

2.Restore System files and settings.
- When Command Prompt mode loads, enter cd restore and press Enter.
- Then enter rstrui.exe and press Enter again.

- Click “Next” in the windows that appeared.

- Select one of the Restore Points that are available before Jew Crypt ransomware has infiltrated to your system and then click “Next”.

- To start System restore click “Yes”.

Step 2. Complete removal of Jew Crypt virus
After restoring your system, it is recommended to scan your computer with an anti-malware program, like Spyhunter and remove all malicious files related to Jew Crypt ransomware. You can check other tools here.Step 3. Restore Jew Crypt ransomware affected files using Shadow Volume Copies
If you do not use System Restore option on your operating system, there is a chance to use shadow copy snapshots. They store copies of your files that point of time when the system restore snapshot was created. Usually Jew Crypt virus tries to delete all possible Shadow Volume Copies, so this methods may not work on all computers. However, it may fail to do so. Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8. There are two ways to retrieve your files via Shadow Volume Copy. You can do it using native Windows Previous Versions or via Shadow Explorer. a) Native Windows Previous Versions Right-click on an encrypted file and select Properties → Previous versions tab. Now you will see all available copies of that particular file and the time when it was stored in a Shadow Volume Copy. Choose the version of the file you want to retrieve and click Copy if you want to save it to some directory of your own, or Restore if you want to replace existing, encrypted file. If you want to see the content of file first, just click Open.
b) Shadow Explorer It is a program that can be found online for free. You can download either a full or a portable version of Shadow Explorer. Open the program. On the left top corner select the drive where the file you are looking for is a stored. You will see all folders on that drive. To retrieve a whole folder, right-click on it and select “Export”. Then choose where you want it to be stored.

Step 4. Use Data Recovery programs to recover Jew Crypt ransomware encrypted files
There are several data recovery programs that might recover encrypted files as well. This does not work in all cases but you can try this:- We suggest using another PC and connect the infected hard drive as slave. It is still possible to do this on infected PC though.
- Download a data recovery program.
- Install and scan for recently deleted files.








