Jaff ransomware virus is a recently located infection which holds users’ digital data hostage until a demanded ransom is paid. Jaff virus is not an innovative variant as it pursues strategies that have already been introduced by preceding samples. It is confirmed that it is currently being intensively transmitted by a botnet. So please be careful when viewing the messages you receive in your email accounts. Crypto-virus combines RSA-2048 cipher with AES-256 algorithm for the sake of making data-recovery even more complicated. If you happen to receive an email letter with a title of “Scan_846554573“ or similar, do not download. nm.pdf files that they contain as attachments. This executable will not present content in Adobe Reader but launch an additional file in the version of Microsoft Office you have installed.
Analysis of this ransomware sample
We have already established that the source of this infection is malicious spam emails. If you download the attachment and attempt to launch it in Adobe Reader, you will notice explanations that JDDVDH.docm should be launched instead. In some cases, the recommended executable will run itself, without users’ participation.
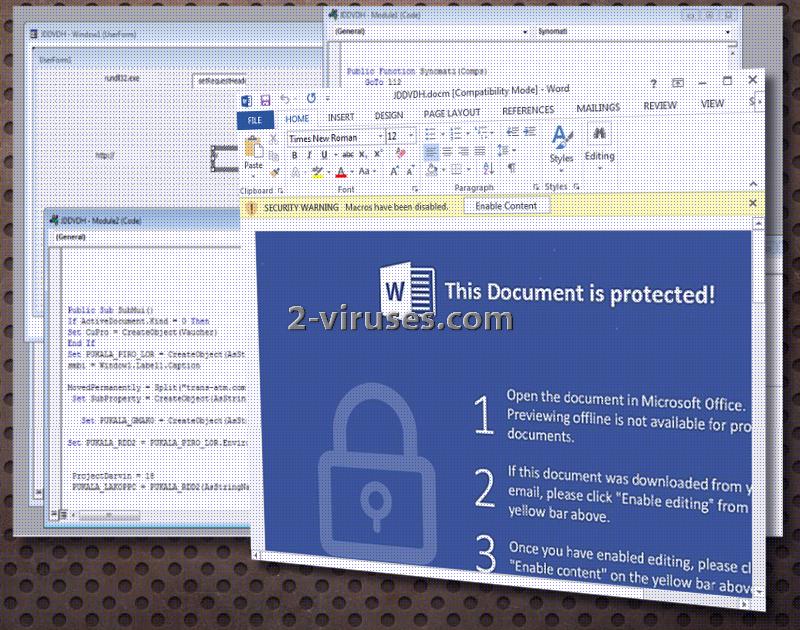
Then, you will be introduced with a Security Warning, informing that this document is protected and you have to Enable both content and editing features. This might seem like a frequent action to perform, but since this .docm file is harmful, it will launch malicious macros. They will install the actual payload of Jaff crypto-virus and place it in an operating system.
The payload could be f87346b.exe, 924c84415.exe or 04_pitupi20.exe as they all were discovered to be inserted by this specific infection. Security tools indicated this infection in 25% detection rate. This specific crypto-virus will choose from variety of files to apply the combination of ciphers on.
After digital data is encoded, the .jaff extension will be appended to every file. Sometime before the encryption is concluded, the ransomware will take advantage out of Internet connection and contact their C&C server, located at Fkksjobnn43.org/a5/ domain. However, the payload only informs hackers that another operating system has been infected.
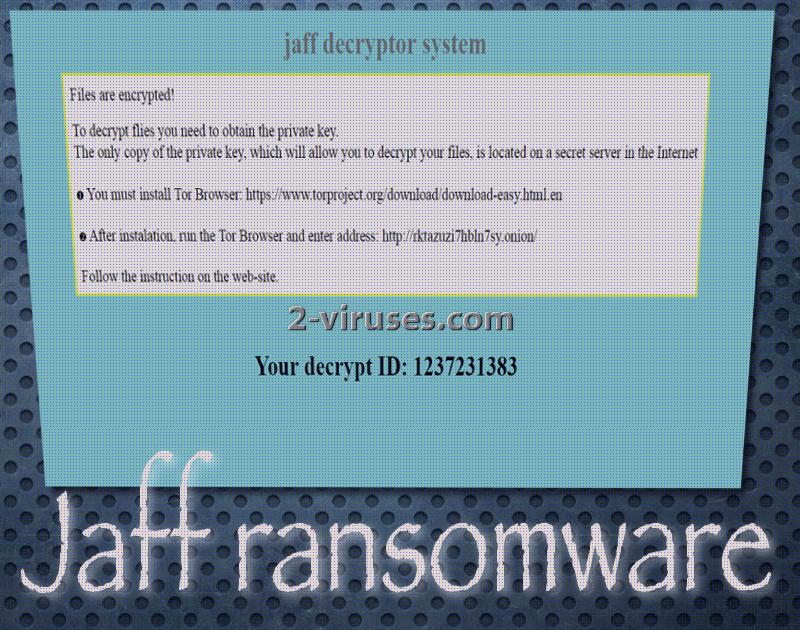
Desktop backgrounds are also going to be replaced with a WallpapeR.bmp file. In random folders infection will also place three ransom notes which will open in different applications. One of them, ReadMe.html will be opened in your preferred browser, while ReadMe.txt and ReadMe.bmp will launch in other appropriate applications. Even though Jaff ransomware requires users to enter a TOR website, its design appears to be copied from Locky. Individual ID numbers of victims will come in handy when it comes to accessing these websites.
Ransom demands and possible methods for decryption
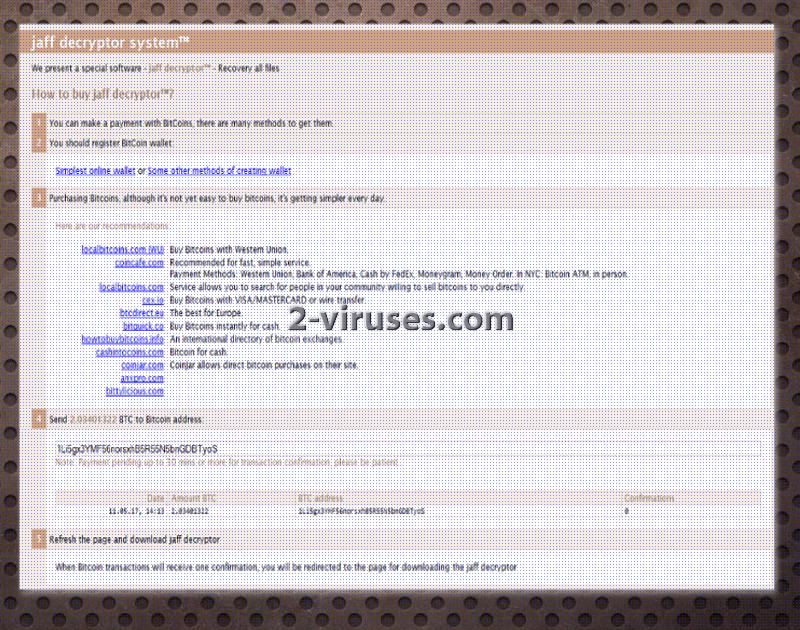
Some of the victims indicated that they were required to pay 1.82196031 BTC which translated into, approximately, 3253.53 US Dollars! This is already a steep price, but it possible that in other cases, even higher sums are going to be required. 2 BTC (around 3577.76) could also be a fee for file-decryption. However, we do not recommend wasting such hefty amounts of cash. If you have become affected with this variant, contact reliable security researchers that will help you decrypt files for free. Fabian Wosar works closely with these matters and could be the one to help you. In many cases, file-decryption takes a long time so we recommend that you try to contact researchers as soon as possible.
UPDATE: decryption tool for Jaff ransomware finally arrived. You can download it from here.
For the future: remember to store your files in backup storages. USB flash drives are also a secure device to keep your valuable digital information. This is a life-saving decision when it comes to ransomware.
How does this ransomware spread?
We have already made a statement in the previous paragraphs on this subject. We indicated that malicious spam campaigns were chosen to distribute this crypto-virus. For the sake of transmitting messages successfully, a botnet was assigned for the job (Necurs). If you have received email messages that seem similarly to the ones that we described in the beginning of this article, delete them from your inbox immediately. We should not ignore other methods that ransomware viruses can exploit for their distribution. This includes, distribution via malicious advertisements, tainted websites or social networking sites.
Before attempting to pursue file-decoding, you are to remove the infection itself. Spyhunter or Malwarebytes could be the tools to help you out in this compromising situation.
Jaff Ransomware quicklinks
- Analysis of this ransomware sample
- Ransom demands and possible methods for decryption
- How does this ransomware spread?
- Automatic Malware removal tools
- How to recover Jaff ransomware encrypted files and remove the virus
- Step 1. Restore system into last known good state using system restore
- 1. Reboot your computer to Safe Mode with Command Prompt:
- 2.Restore System files and settings.
- Step 4. Use Data Recovery programs to recover Jaff ransomware encrypted files

Automatic Malware removal tools
(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
How to recover Jaff ransomware encrypted files and remove the virus
Step 1. Restore system into last known good state using system restore
1. Reboot your computer to Safe Mode with Command Prompt:
for Windows 7 / Vista/ XP
- Start → Shutdown → Restart → OK.
- Press F8 key repeatedly until Advanced Boot Options window appears.
- Choose Safe Mode with Command Prompt.

for Windows 8 / 10
- Press Power at Windows login screen. Then press and hold Shift key and click Restart.

- Choose Troubleshoot → Advanced Options → Startup Settings and click Restart.
- When it loads, select Enable Safe Mode with Command Prompt from the list of Startup Settings.

2.Restore System files and settings.
- When Command Prompt mode loads, enter cd restore and press Enter.
- Then enter rstrui.exe and press Enter again.

- Click “Next” in the windows that appeared.

- Select one of the Restore Points that are available before Jaff virus has infiltrated to your system and then click “Next”.

- To start System restore click “Yes”.

Step 2. Complete removal of Jaff Decryption System ransomware
After restoring your system, it is recommended to scan your computer with an anti-malware program, like Spyhunter and remove all malicious files related to Jaff ransomware. You can check other tools here.Step 3. Restore Jaff virus affected files using Shadow Volume Copies
If you do not use System Restore option on your operating system, there is a chance to use shadow copy snapshots. They store copies of your files that point of time when the system restore snapshot was created. Usually Jaff Decryption System ransomware tries to delete all possible Shadow Volume Copies, so this methods may not work on all computers. However, it may fail to do so. Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8. There are two ways to retrieve your files via Shadow Volume Copy. You can do it using native Windows Previous Versions or via Shadow Explorer. a) Native Windows Previous Versions Right-click on an encrypted file and select Properties → Previous versions tab. Now you will see all available copies of that particular file and the time when it was stored in a Shadow Volume Copy. Choose the version of the file you want to retrieve and click Copy if you want to save it to some directory of your own, or Restore if you want to replace existing, encrypted file. If you want to see the content of file first, just click Open.
b) Shadow Explorer It is a program that can be found online for free. You can download either a full or a portable version of Shadow Explorer. Open the program. On the left top corner select the drive where the file you are looking for is a stored. You will see all folders on that drive. To retrieve a whole folder, right-click on it and select “Export”. Then choose where you want it to be stored.

Step 4. Use Data Recovery programs to recover Jaff ransomware encrypted files
There are several data recovery programs that might recover encrypted files as well. This does not work in all cases but you can try this:- We suggest using another PC and connect the infected hard drive as slave. It is still possible to do this on infected PC though.
- Download a data recovery program.
- Install and scan for recently deleted files.








