FCP ransomware is a dangerous virus that can attack your system and cause lethal damage. As most of ransomware infections, it aims to infect computers and encrypt files stored on the system. It is unusual that this ransomware does not add any extension to the encrypted files, as other ransomware tend to do.
If your computer gets infected, 4 new files will appear on your desktop. They are called “Chinese_national_flag.png’, ‘ FCP Decryptor.exe’, ‘READ_ME_HELP_ME.png’ and ‘ READ_ME_HELP_ME.TXT’.
Both PNG (portable network graphics) files will be opened automatically immediately after that. One of them, called “Chinese_national_flag.png’ is simply a flag of Chine, so it is pretty obvious that developers of this infection is from the country. Or at least they want you to think that way. The second one, called ‘READ_ME_HELP_ME.png’ is a so-called ransom note – information about your current situation and instructions what you should do next. It looks like this:
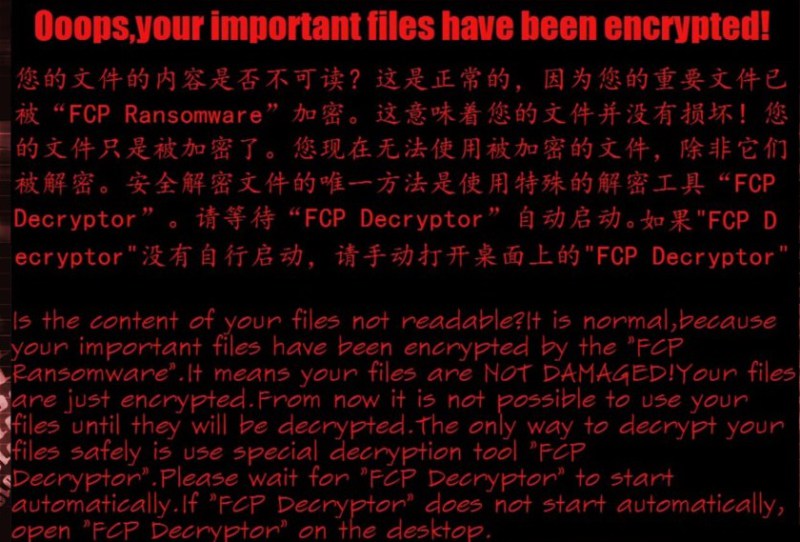
Original text of the ransom note:
Ooops, your important files have been encrypted!
Is the content of your files not readable?
It is normal,because your important files have been encrypted by the “FCP Ransomware”.
It means your files are NOT DAMAGED!Your files are just encrypted.
From now it is not possible to use your files until they will be decrypted.
The only way to decrypt your files safely is use special decryption tool “FCP Decryptor”.
Please wait for “FCP Decryptor” to start automatically.
If “FCP Decryptor” does not start automatically, open “FCP Decryptor” on the desktop.
As you can see, a victim is informed that all his files are encrypted and can’t be opened. The only way to restore them – use the decryptor provided by FCP ransomware. And this leads us to the next file form the desktop – ‘ FCP Decryptor.exe’. It will also start automatically after some time. On the first window you will be suggested to input file path you would like to decrypt and hit enter. The decryptor will encrypt some files from that directory just to prove that they have working technology and can solve your problems. However, decryptor is not free, and the following message looks like this:
Decrypt all files you should buy Advanced Edition FCP Decryptor.
Way of buying:Send 0.050 bitcoins to the specified address(Worth about $303).
Address:1Mz7153hMuFiFcOme1T73mGsDzqAtMbBwX
Send a message to the E-mail address after payment:
E-mail:[email protected]
Title :Buy FCP Decryptor
Content: Your payment information
You will get a reply after send E-mail,The message contains an activation code,
Please enter below.
Press [Enter] to confirm,FCP Decryptor will decrypt all encrypted filesíú
Now you are asked to purchase “Advanced Edition FCP Decryptor’ which costs 0.050 bitcoins, about $300 at the current exchange rate. Crypto email is also from China, so most probably this virus origins from China.
However, even if you experienced that their decryptor is working and it managed to encrypt some of your files, we suggest not to purchase advanced edition of FCP Decryptor. 300USD is not a small amount and by paying the ransom you would support cyber criminals, so they could develop more viruses like this and infect other computers. Besides that, even if you pay the ransom it is not guaranteed that your files will be encrypted – you can never trust them.
As for now, there are no working and free decryptor for this particular FCP ransomware virus, but we will update this post as soon as one is ready. There is still a chance to retrieve your files without paying the ransom – restore them from a backup. By performing a system restore, you will set your system to the date previous to infection and all your files and system will be good to go. However, in order to do that, you need a valid copy of your hard drive which is stored on an external storage. If it is stored on your computer, FCP ransomware most probably corrupted it as well. Take a look at our tutorial how to perform a system restore: https://www.2-viruses.com/how-to-do-a-system-restore.
Fcp Ransomware quicklinks
- Automatic Malware removal tools
- How to recover FCP ransomware encrypted files and remove the virus
- Step 1. Restore system into last known good state using system restore
- 1. Reboot your computer to Safe Mode with Command Prompt:
- 2.Restore System files and settings.
- Step 4. Use Data Recovery programs to recover FCP ransomware encrypted files
Automatic Malware removal tools
(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
How to recover FCP ransomware encrypted files and remove the virus
Step 1. Restore system into last known good state using system restore
1. Reboot your computer to Safe Mode with Command Prompt:
for Windows 7 / Vista/ XP
- Start → Shutdown → Restart → OK.
- Press F8 key repeatedly until Advanced Boot Options window appears.
- Choose Safe Mode with Command Prompt.

for Windows 8 / 10
- Press Power at Windows login screen. Then press and hold Shift key and click Restart.

- Choose Troubleshoot → Advanced Options → Startup Settings and click Restart.
- When it loads, select Enable Safe Mode with Command Prompt from the list of Startup Settings.

2.Restore System files and settings.
- When Command Prompt mode loads, enter cd restore and press Enter.
- Then enter rstrui.exe and press Enter again.

- Click “Next” in the windows that appeared.

- Select one of the Restore Points that are available before FCP ransomware has infiltrated to your system and then click “Next”.

- To start System restore click “Yes”.

Step 2. Complete removal of FCP ransomware
After restoring your system, it is recommended to scan your computer with an anti-malware program, like Spyhunter and remove all malicious files related to FCP ransomware. You can check other tools here.Step 3. Restore FCP ransomware affected files using Shadow Volume Copies
If you do not use System Restore option on your operating system, there is a chance to use shadow copy snapshots. They store copies of your files that point of time when the system restore snapshot was created. Usually FCP ransomware tries to delete all possible Shadow Volume Copies, so this methods may not work on all computers. However, it may fail to do so. Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8. There are two ways to retrieve your files via Shadow Volume Copy. You can do it using native Windows Previous Versions or via Shadow Explorer. a) Native Windows Previous Versions Right-click on an encrypted file and select Properties → Previous versions tab. Now you will see all available copies of that particular file and the time when it was stored in a Shadow Volume Copy. Choose the version of the file you want to retrieve and click Copy if you want to save it to some directory of your own, or Restore if you want to replace existing, encrypted file. If you want to see the content of file first, just click Open.
b) Shadow Explorer It is a program that can be found online for free. You can download either a full or a portable version of Shadow Explorer. Open the program. On the left top corner select the drive where the file you are looking for is a stored. You will see all folders on that drive. To retrieve a whole folder, right-click on it and select “Export”. Then choose where you want it to be stored.

Step 4. Use Data Recovery programs to recover FCP ransomware encrypted files
There are several data recovery programs that might recover encrypted files as well. This does not work in all cases but you can try this:- We suggest using another PC and connect the infected hard drive as slave. It is still possible to do this on infected PC though.
- Download a data recovery program.
- Install and scan for recently deleted files.








