Fake WindowsUpdater (other names: File Security Protected virus, Fake WU virus) was assigned, without any reluctance, to the group of ransomware. The most plausible tactic for distribution of this ransomware is through Fake Windows Updaters which can be found in file-sharing domains, social networking sites or email inboxes. Limit the amount of files and programs you download and when you do download something from the Internet, be positive that the content won’t be an agent of detrimental schemes. Fake WindowsUpdater crypto-virus appears to be using a relatively clear encryption mode, referred to by the name Electronic Codebook. During this procedure, the files to be encoded will be divided into blocks, an each and one of them will be corrupted individually. The algorithm to do this will be AES-256.
Description of Fake WindowsUpdater ransomware
Fake WindowsUpdater ransomware was detected only yesterday, on 4th of April. There are two files that could be exploited as payloads. One of them is WindowsUpdater.exe and another one is Transaction-Report.docx.exe. Have you ever been offered to download these executables? In case the answer is yes, we will not hesitate and offer you our assistance in the removal of this ransomware. If your files are not yet encrypted, which means that it is still possible to prevent a ransomware infection from fully corrupting data. You have to run a full security scan with an anti-malware tool. If Spyhunter, Plumbytes or Hitman finds potential threats, you are to remove them all.
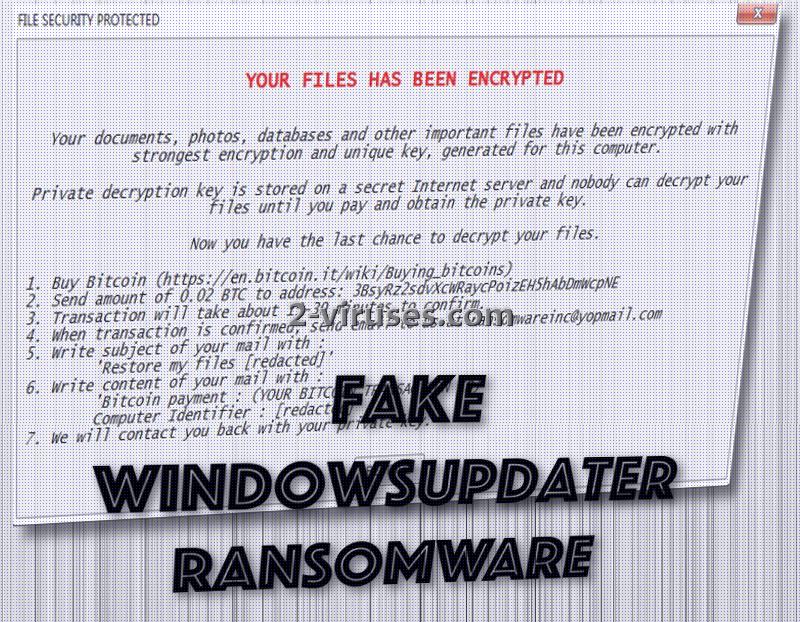
Fake WindowsUpdater crypto-virus can display a ransom note in a form of a grey table. There is no knowledge whether it will block access to the rest of the device. You might be surprised to hear that this sample demands one of the smallest ransoms we have seen: approximately 23 US dollars, 22.71 to be exact. Hackers do not set limitations of time in which the fee should be send. It merely leaves behind its bitcoin wallet and reminds victims that only the concealed private key of decryption is capable of bringing files back to their original state.
However, developers of Fake WindowsUpdater ransomware will demand that the indicated amount of dollars would be converted into bitcoins first. It takes 15-30 minutes to confirm a transaction. In the meanwhile, victims of this variant have to send a private email to [email protected] address. Subject of the message is supposed to be “Restore my files”, accompanied by the “Bitcoin payment: (victims’ bitcoin transaction number). Computer identifier: [ID]”.
Then, hackers will allegedly provide a functional key for decryption. After that users are presumably required to click “RESTORE” button. Ganedata.co.uk/ransomware/ransomware.php is the hackers C&C server which will be solely operated to exchange information between the Fake WindowsUpdater virus and its authors. All of the miscellaneous files that the virus can encrypt will be appended with a popular extension: .encrypted.
Ways of saving files, corrupted by Fake WindowsUpdater ransomware
Fake WindowsUpdater crypto-virus can select from hundreds of file-types to complete encryption: none of your data is safe from it. For now, there is no cure for the files, but we expect that security researchers will give un update on this topic soon. Since this sample was detected yesterday, there is no reason to expect that the free tool for decryption will be generated so quickly. However, there are universal tricks for decryption that might function. Look below to learn about Shadow Volume copies and other methods, used for file-recovery. As for immunity from ransomware: you are advised to upload files into backup storages and keep them there.
Distribution methods that Fake WindowsUpdater ransomware can adopt
Fake WindowsUpdater virus can be spread with two files that we mentioned before. If you notice that an unknown source is offering you an update for Windows, make sure that Microsoft is involved. Most of the time, if the patches are not downloaded from the legitimate Microsoft’s page, then some other parties might be trying deceive you. In addition to that, reminders to update your operating system can also arrive in your email inboxes. If you notice these propositions, please refuse them.
Fake Windowsupdater Ransomware quicklinks
- Description of Fake WindowsUpdater ransomware
- Ways of saving files, corrupted by Fake WindowsUpdater ransomware
- Distribution methods that Fake WindowsUpdater ransomware can adopt
- Automatic Malware removal tools
- How to recover Fake WindowsUpdater ransomware encrypted files and remove the virus
- Step 1. Restore system into last known good state using system restore
- 1. Reboot your computer to Safe Mode with Command Prompt:
- 2.Restore System files and settings.
- Step 4. Use Data Recovery programs to recover Fake WindowsUpdater ransomware encrypted files
Automatic Malware removal tools
(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
How to recover Fake WindowsUpdater ransomware encrypted files and remove the virus
Step 1. Restore system into last known good state using system restore
1. Reboot your computer to Safe Mode with Command Prompt:
for Windows 7 / Vista/ XP
- Start → Shutdown → Restart → OK.
- Press F8 key repeatedly until Advanced Boot Options window appears.
- Choose Safe Mode with Command Prompt.

for Windows 8 / 10
- Press Power at Windows login screen. Then press and hold Shift key and click Restart.

- Choose Troubleshoot → Advanced Options → Startup Settings and click Restart.
- When it loads, select Enable Safe Mode with Command Prompt from the list of Startup Settings.

2.Restore System files and settings.
- When Command Prompt mode loads, enter cd restore and press Enter.
- Then enter rstrui.exe and press Enter again.

- Click “Next” in the windows that appeared.

- Select one of the Restore Points that are available before File Security Protected virus has infiltrated to your system and then click “Next”.

- To start System restore click “Yes”.

Step 2. Complete removal of Fake WU virus
After restoring your system, it is recommended to scan your computer with an anti-malware program, like Spyhunter and remove all malicious files related to Fake WindowsUpdater ransomware. You can check other tools here.Step 3. Restore File Security Protected virus affected files using Shadow Volume Copies
If you do not use System Restore option on your operating system, there is a chance to use shadow copy snapshots. They store copies of your files that point of time when the system restore snapshot was created. Usually Fake WU virus tries to delete all possible Shadow Volume Copies, so this methods may not work on all computers. However, it may fail to do so. Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8. There are two ways to retrieve your files via Shadow Volume Copy. You can do it using native Windows Previous Versions or via Shadow Explorer. a) Native Windows Previous Versions Right-click on an encrypted file and select Properties → Previous versions tab. Now you will see all available copies of that particular file and the time when it was stored in a Shadow Volume Copy. Choose the version of the file you want to retrieve and click Copy if you want to save it to some directory of your own, or Restore if you want to replace existing, encrypted file. If you want to see the content of file first, just click Open.
b) Shadow Explorer It is a program that can be found online for free. You can download either a full or a portable version of Shadow Explorer. Open the program. On the left top corner select the drive where the file you are looking for is a stored. You will see all folders on that drive. To retrieve a whole folder, right-click on it and select “Export”. Then choose where you want it to be stored.

Step 4. Use Data Recovery programs to recover Fake WindowsUpdater ransomware encrypted files
There are several data recovery programs that might recover encrypted files as well. This does not work in all cases but you can try this:- We suggest using another PC and connect the infected hard drive as slave. It is still possible to do this on infected PC though.
- Download a data recovery program.
- Install and scan for recently deleted files.