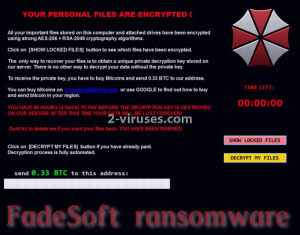
FadeSoft crypto-virus has made its first appearance in the online society and explained to have emerged from the ransomware category. By displaying a demanding ransom note with the introductory words ‘YOUR PERSONAL FILES ARE ENCRYPTED’, it simply had no choice but to join the disgraceful and wicked clan of ransomware. The new villainous member has incorporated details from Resident Evil, more specifically, the logo of Umbrella Corps. Creators of FadeSoft virus explain that it encrypts files with AES-256 and RSA-2048. The latter one is presumably exploited to encode the decryption key itself. To receive it straight from the attackers, victims are expected to make a transaction of 33.56 US dollars in a form of bitcoins. In this currency, you would be sending approximately 0.033 BTC. Despite the fact that that fee sounds quite agreeable, you are roughly discouraged from making payments to hackers’ bitcoin wallet. If you do otherwise, your money will end up in the hands of skilled but vicious programmers who will accept your bitcoins as an encouragement to continue with ransomware infections in the future.
Sinful temper of FadeSoft ransomware
Does FadeSoft crypto-virus mark its territory, or rather the data it prevented from opening, with a unique extension? Not to our knowledge. To match this feature, variant displays a button, called ‘Show Locked Files’. After clicking it, victims should be introduced with the files that got wrecked with encryption. Users inability to access important data is the ponderable argument in favor of paying the ransom. However, an even more weighty fact should be recognized: hackers might take their victims as fools and lure them in with a promise of an automatic decryption software. In reality, victims’ might get stuck with a bunch of encrypted files and a memory of wasted dollars. FadeSoft virus initiates its activity in a system after slithering inside and releases its poison. Firstly, it will reach Windows Registry Keys and make sure that the payload of FadeSoft ransomware would have the privilege of being launched. The payload is programmed to contact its creators via C&C servers. For this to be possible, FadeSoft ransomware inserts TOR browser and Privoxy to have the competence to accomplish it.
FadeSoft virus can choose from over 300 file types for encryption: for this reason, we do believe that basically any piece of data in your hard drive could be corrupted. We have not encountered reports that would give any hints about an extension appended to the damaged content. We also have reason to believe that FadeSoft ransomware will delete Shadow Volume Copies to make sure that the decryption progress would be even more difficult to pursue. If you notice the window that FadeSoft virus displays as its ransom, then your system has become a host of a ransomware infection. From this moment, you have only 96 hours to arrive at a decision about your next move. More details about decryption process are to be found in the following section.
FadeSoft ransomware and ways to resurrect your files
There is no magical dragon to summon if you wish to decrypt files that FadeSoft virus has left impaired. All you can do is attempt to decrypt files in a couple of ways: first of all, you might check Shadow Volume Copies. If there is any chance that the virus left them intact, you are encouraged to be aware of such advantage. In addition to that, you should also give it a go with universal file-recovery tools. More info about the latter options can be found below. However, we are also obligated to remind our visitors that storing data in backup storages is not an overly-protective action. In fact, it is encouraged. Retrieving files from storages is easy: if an ransomware successfully wrecks your data, it is a calming thing to remember that you can easily get them back from another location. For now, a free decryption software has not been released.
Techniques that FadeSoft ransomware can embrace for distribution
FadeSoft ransomware can be exploiting tactics that have been well-recognized in crypto-viruses. Malicious spam letters are one of the very likely distributors of this infection, but it might not be the only one. Exploit kits are frequently noticed as the culprits of ransomware transmission and there is no evidence to suggest that FadeSoft ransomware could not be spread like this. Distribution and removal seem awfully related topics, so we are going to jump straight to it. If you are a victim of FadeSoft virus, you are encouraged to remove it as soon as possible. Before doing so, you should save the encrypted data in another location, like an USB flash drive, just in case. This ransomware infection could be programmed to delete the encrypted data if its payload gets removed. For an easy elimination process, use Spyhunter or Malwarebytes. Handy details about manual removal and decryption of files are listed below.
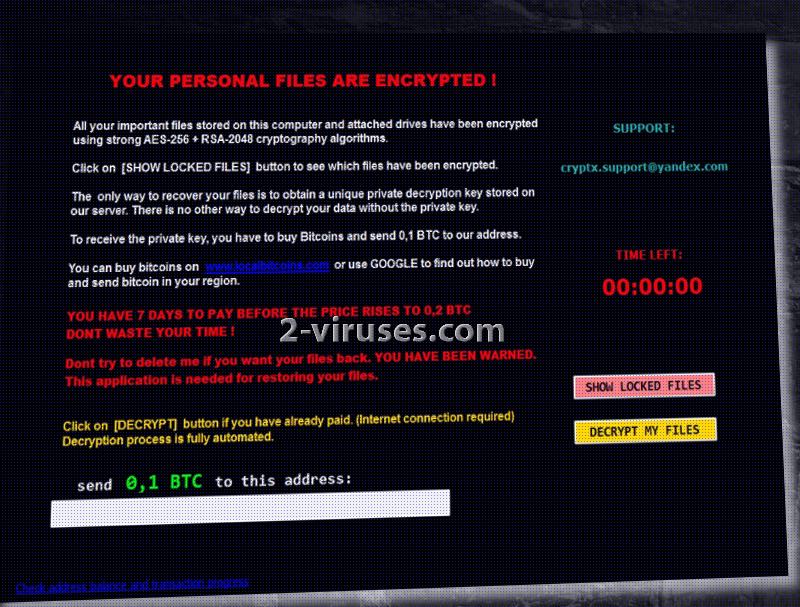
Update of the 13th of March, 2017. A new version of Fadesoft ransomware has been spotted. It demands less money than its former sample: 0,1 BTC. if victims do not pay this fee in the next 7 days, price will increase to 0,2 BTC. It also requires people to contact [email protected] email address.
Update of the 31st of March, 2017. A CryptoSearch tool was released which will help victims find all of the files that have been encrypted by FadeSoft. Since this ransomware does not append any extension to corrupted data, discovering all can be difficult. Download it from here.
Fadesoft Ransomware quicklinks
- Sinful temper of FadeSoft ransomware
- FadeSoft ransomware and ways to resurrect your files
- Techniques that FadeSoft ransomware can embrace for distribution
- Automatic Malware removal tools
- How to recover FadeSoft ransomware encrypted files and remove the virus
- Step 1. Restore system into last known good state using system restore
- 1. Reboot your computer to Safe Mode with Command Prompt:
- 2.Restore System files and settings.
- Step 4. Use Data Recovery programs to recover FadeSoft ransomware encrypted files
Automatic Malware removal tools
(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
How to recover FadeSoft ransomware encrypted files and remove the virus
Step 1. Restore system into last known good state using system restore
1. Reboot your computer to Safe Mode with Command Prompt:
for Windows 7 / Vista/ XP
- Start → Shutdown → Restart → OK.
- Press F8 key repeatedly until Advanced Boot Options window appears.
- Choose Safe Mode with Command Prompt.

for Windows 8 / 10
- Press Power at Windows login screen. Then press and hold Shift key and click Restart.

- Choose Troubleshoot → Advanced Options → Startup Settings and click Restart.
- When it loads, select Enable Safe Mode with Command Prompt from the list of Startup Settings.

2.Restore System files and settings.
- When Command Prompt mode loads, enter cd restore and press Enter.
- Then enter rstrui.exe and press Enter again.

- Click “Next” in the windows that appeared.

- Select one of the Restore Points that are available before FadeSoft virus has infiltrated to your system and then click “Next”.

- To start System restore click “Yes”.

Step 2. Complete removal of FadeSoft ransomware
After restoring your system, it is recommended to scan your computer with an anti-malware program, like Spyhunter and remove all malicious files related to FadeSoft virus. You can check other tools here.Step 3. Restore FadeSoft ransomware affected files using Shadow Volume Copies
If you do not use System Restore option on your operating system, there is a chance to use shadow copy snapshots. They store copies of your files that point of time when the system restore snapshot was created. Usually FadeSoft virus tries to delete all possible Shadow Volume Copies, so this methods may not work on all computers. However, it may fail to do so. Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8. There are two ways to retrieve your files via Shadow Volume Copy. You can do it using native Windows Previous Versions or via Shadow Explorer. a) Native Windows Previous Versions Right-click on an encrypted file and select Properties → Previous versions tab. Now you will see all available copies of that particular file and the time when it was stored in a Shadow Volume Copy. Choose the version of the file you want to retrieve and click Copy if you want to save it to some directory of your own, or Restore if you want to replace existing, encrypted file. If you want to see the content of file first, just click Open.
b) Shadow Explorer It is a program that can be found online for free. You can download either a full or a portable version of Shadow Explorer. Open the program. On the left top corner select the drive where the file you are looking for is a stored. You will see all folders on that drive. To retrieve a whole folder, right-click on it and select “Export”. Then choose where you want it to be stored.

Step 4. Use Data Recovery programs to recover FadeSoft ransomware encrypted files
There are several data recovery programs that might recover encrypted files as well. This does not work in all cases but you can try this:- We suggest using another PC and connect the infected hard drive as slave. It is still possible to do this on infected PC though.
- Download a data recovery program.
- Install and scan for recently deleted files.