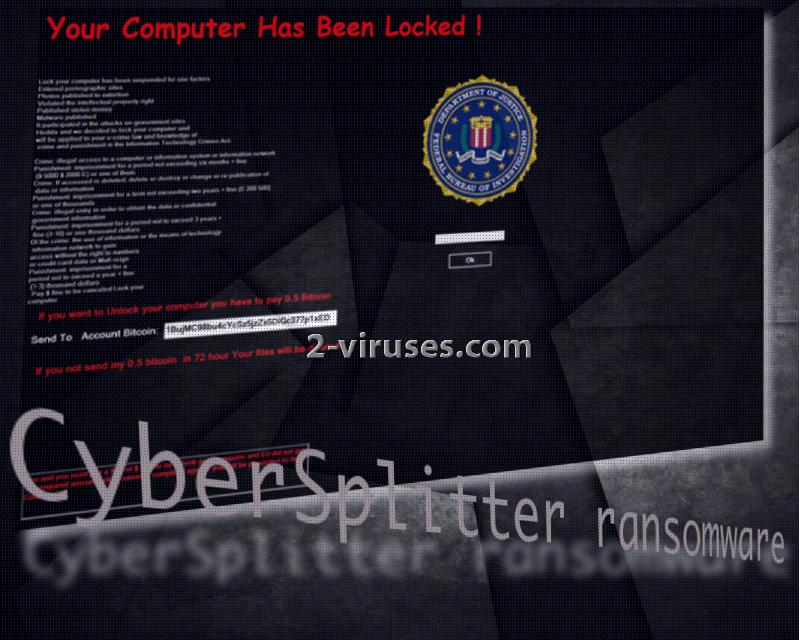
CyberSplitter virus explores a strategy as long as time: it poses as respectable authorities from FBI that have found users guilty of a number of different violations of law. Victims that notice its generated lock screen are accused of being suspected of a multitude of crimes. It might be that you are going to be blamed for participation in attacks against governmental websites, for publishing malware threats, for stealing money, for entering pornographic websites or for involvement in other offensive activities. Do not be mistaken by the official logo of Federal Bureau of Investigation: CyberSplitter was not produced by actual officers from this facility. This is a fabricated message, constructed by vicious crooks that wish to profit from their schemes. If infected victims wish to avoid penalties for their alleged crimes, they have to give in and pay the demanded amount of bitcoins. This is also a necessity since if victims won’t act in accordance with the set instructions, their files are threatened to be deleted. Nothing about this ransomware sounds convincing enough for people to actually believe that they are being warned by the legitimate FBI.
Main signs of a CyberSplitter ransomware
CyberSplitter ransomware is allegedly warning people that their activity online is going be punished if they do not negotiate. Since people that generated this message are not legitimate authorities, no fines or punishments will be applied to you if you refuse to pay. A different subject is your locked device and files that you keep in it. Everything that you store in your device is in jeopardy, as long as you have a malicious virus present. Do not surrender to intimidation and be skeptical when it comes to accusatios such as these. If you favor a secure browsing and have never performed any malicious activity online, you should not believe such accusations just because some unidentified source makes them. Controllers of CyberSplitter definitely do not hold the right to make statements that it does.
In addition to that, in a relatively short period of time, three different versions of CyberSplitter have been detected. However, only the first one pretends to be from FBI. The other samples do not clearly indicate their origin. All versions seem to stick with a specific amount of bitcoins to demand as the ransom: 0.5 BTC (approximately 530.76 US Dollars). No one should pay the required fee as it won’t lead to anything beneficial. The only realistic scenario is that you will be tricked into sending bitcoins and will be left without a functional code to unlock your device or prevent files from being deleted before 72 hours passes. It is yet unconfirmed whether CyberSplitter virus uses any specific extension to mark the encrypted data.
How could I escape CyberSplitter and its lock screen?
The only method we recommend is to wait until security researchers can provide you with a functional key. If you are in a hurry, you can try to contact security researchers and ask whether the process of figuring out CyberSplitter is in progress. Our goal is to always prevent people from paying the requested fee. Victims unknowingly become sponsors of future ransomware projects. Actually, the decryption of files is a rather delicate topic to discuss: very frequently decrypters take a lot of time to be made. For this reason, it is always better to follow even the most basic methods for ransomware prevention. One of the most popular trends to protect yourself from ransomware is to protect your data by storing it in multiple locations. You can keep your files in USB flash drives or backup storages, whichever fits you better. If you will have an additional location to retrieve your files, ransomware virus won’t stand a chance.
How did CyberSplitter end up in my system?
Since this is a ransomware infection, we have reasons to believe that its payload spreads in the most notorious ways. Campaigns of malicious executables could be released in order to distribute CyberSplitter virus. Resist opening email letters that might seem unfamiliar to you or are addressing issues that you have nothing to do with. When you open an email, always be certain that the email is reliable; that is the golden rule. Additionally, you are discouraged from entering domains that might be damaged by malicious exploit kits. A specific distribution for CyberSplitter is yet undetermined, but we can assume that it is one of the ones we have enumerated.
CyberSplitter virus can be deleted with Spyhunter or Malwarebytes. These anti-malware tools will be royal guardians to your device and eliminate every threat that you might encounter. Before initiating removal, you are advised to reboot your device in Safe Mode and copy all of the files that have been encrypted. Recommendations for manual removal are listed below.
Cybersplitter Ransomware quicklinks
- Main signs of a CyberSplitter ransomware
- How could I escape CyberSplitter and its lock screen?
- How did CyberSplitter end up in my system?
- Automatic Malware removal tools
- How to recover CyberSplitter ransomware encrypted files and remove the virus
- Step 1. Restore system into last known good state using system restore
- 1. Reboot your computer to Safe Mode with Command Prompt:
- 2.Restore System files and settings.
- Step 4. Use Data Recovery programs to recover CyberSplitter ransomware encrypted files
Automatic Malware removal tools
(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
How to recover CyberSplitter ransomware encrypted files and remove the virus
Step 1. Restore system into last known good state using system restore
1. Reboot your computer to Safe Mode with Command Prompt:
for Windows 7 / Vista/ XP
- Start → Shutdown → Restart → OK.
- Press F8 key repeatedly until Advanced Boot Options window appears.
- Choose Safe Mode with Command Prompt.

for Windows 8 / 10
- Press Power at Windows login screen. Then press and hold Shift key and click Restart.

- Choose Troubleshoot → Advanced Options → Startup Settings and click Restart.
- When it loads, select Enable Safe Mode with Command Prompt from the list of Startup Settings.

2.Restore System files and settings.
- When Command Prompt mode loads, enter cd restore and press Enter.
- Then enter rstrui.exe and press Enter again.

- Click “Next” in the windows that appeared.

- Select one of the Restore Points that are available before CyberSplitter virus has infiltrated to your system and then click “Next”.

- To start System restore click “Yes”.

Step 2. Complete removal of CyberSplitter ransomware
After restoring your system, it is recommended to scan your computer with an anti-malware program, like Spyhunter and remove all malicious files related to CyberSplitter virus. You can check other tools here.Step 3. Restore CyberSplitter ransomware affected files using Shadow Volume Copies
If you do not use System Restore option on your operating system, there is a chance to use shadow copy snapshots. They store copies of your files that point of time when the system restore snapshot was created. Usually CyberSplitter virus tries to delete all possible Shadow Volume Copies, so this methods may not work on all computers. However, it may fail to do so. Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8. There are two ways to retrieve your files via Shadow Volume Copy. You can do it using native Windows Previous Versions or via Shadow Explorer. a) Native Windows Previous Versions Right-click on an encrypted file and select Properties → Previous versions tab. Now you will see all available copies of that particular file and the time when it was stored in a Shadow Volume Copy. Choose the version of the file you want to retrieve and click Copy if you want to save it to some directory of your own, or Restore if you want to replace existing, encrypted file. If you want to see the content of file first, just click Open.
b) Shadow Explorer It is a program that can be found online for free. You can download either a full or a portable version of Shadow Explorer. Open the program. On the left top corner select the drive where the file you are looking for is a stored. You will see all folders on that drive. To retrieve a whole folder, right-click on it and select “Export”. Then choose where you want it to be stored.

Step 4. Use Data Recovery programs to recover CyberSplitter ransomware encrypted files
There are several data recovery programs that might recover encrypted files as well. This does not work in all cases but you can try this:- We suggest using another PC and connect the infected hard drive as slave. It is still possible to do this on infected PC though.
- Download a data recovery program.
- Install and scan for recently deleted files.