CryptoLocker (alias Cryptographic Locker) is one application that you would not like to find on your computer. A lot of users confuse it with Locky ransomware, but this virus is not related to it. Locky ransomware uses .locky extension, you can read more about it here: https://www.2-viruses.com/remove-locky-ransomware. While the Cryptolocker virus uses 6 random letters written in the lower case as the extension for the encrypted files. For instance, File.pdf.ghjytr would be the name of the file locked by this virus.
It is listed as ransomware — a type of malware that encrypts all personal files stored on your computer. Due to it being on your PC you will have a lot of difficulties dealing with this situation.
CryptoLocker infected half a million computers and encrypted their files, making them unusable, their data — inaccessible. Luckily, files encrypted by the virus are recoverable using a decrypter linked to in the updates section.
The malware still needs to be deleted before that, otherwise, it will repeatedly re-encrypt the files.
| CryptoLocker features |
|
|---|---|
| Distribution |
|
| Useful precautions |
|
| Removal of CryptoLocker virus |
|
CryptoLocker symptoms
Once CryptoLocker is installed on your computer, you will see the following message, named as HOW_TO_RESTORE_FILES, in the TXT and HTML file format:
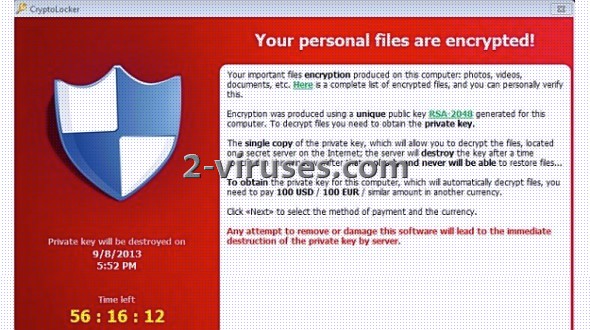
“Your personal files are encrypted!
Your important files encryption produced on this computer: photos, videos, documents, etc. Here is a complete list of encrypted files, and you can personally verify this.
Encryption was produced using a unique public key RSA-2048 generated for this computer. To decrypt files you need to obtain the private key. The single copy of the private key, which will allow you to decrypt the files, located on a secret server on the Internet: the server will destroy the key after a time specified in this window. After that, nobody and never will be able to restore files…
To obtain the private key for this computer, which will automatically decrypt files, you need to pay 100 USD/ 100 EUR / similar amount in another currency.
Any attempt to remove or damage this software will lead to the immediate destruction of the private key by server”
Don’t get too scared by the last statement of this message. Even though this ransomware is pretty serious and you will not be able to get back your encrypted files, you can remove CryptoLocker and prevent it from operating on your system as well as causing some more damage. The CryptoLocker virus is very similar to CryptoFortress, Buyunlockcode ransomware, CTB Locker ransomware, Simplelocker, TeslaCrypt, CryptoDefense, and CryptoWall. These infections are recognized by most competent anti-malware programs and can be completely removed and the decryption key won’t be deleted.
Perhaps the only difference is that all of those ransomware infections ask you to pay 500 euros/usd, not 100, so CryptoLocker is a better option, in a way. This ransomware uses Bitcoin payment system – a ransom has to be paid using it, so it is harder to track hackers who stand behind this. And it still tries to scare people into paying by insisting that the decryption key will be destroyed after an amount of time. As we later learn, this was just another lie designed to manipulate people.
How to remove CryptoLocker
As we have mentioned before, you need to remove this malicious application from your computer if you don’t want any other files to be encrypted in the future. To do this, you should download a trusted anti-malware scanner that is professional and could deal with this issue, such as SpyHunter. Scan your PC with it and it will detect and remove the ransomware automatically. It is advised to regularly scan your computer with one of these anti-malware programs if you don’t want to lose any data or money due to CryptoLocker or any other similar malware.
Updates
Update of the 2nd of March, 2017. We have discovered that CryptoLocker ransomware is back. In 2015-2016, distribution and the general activity of CryptoLocker was close to a minimum, but now, hackers seem to have reconsidered their position and are determined to transmit CryptoLocker once again. People from Europe is identified to be as the main audience to receive the newly distributed CryptoLocker variant. It spreads via malicious spam campaigns.
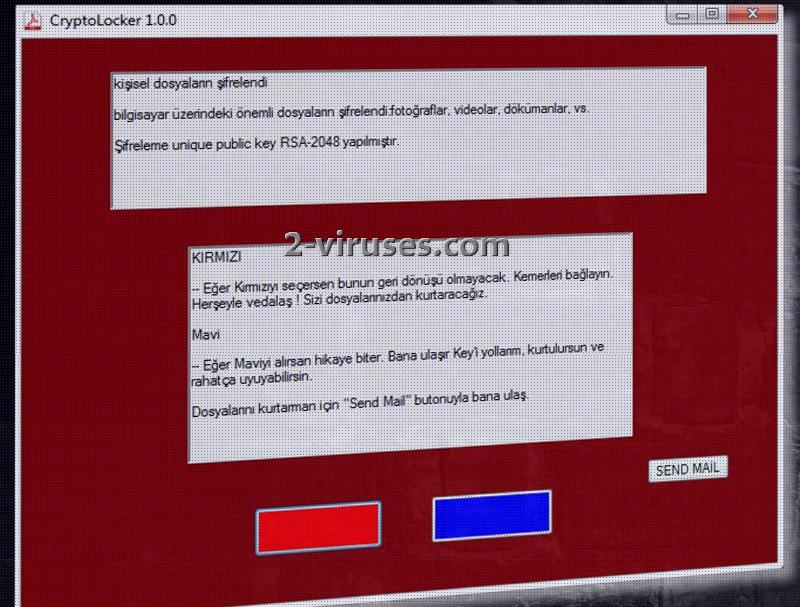
Update of the 13th of March, 2017. Early spring appears to be an active time for the CryptoLocker virus. A fresh variant has been revealed and it targets Turkish-speaking users. Its ransom note is written in Turkish as well.
Update: the decrypter is now available at here: link. You can download it absolutely for free and successfully decrypt your files.
CryptoLocker was taken down after law enforcement from multiple countries united to take down the Gameover Zeus botnet which had been distributing this cryptovirus. Thanks to this operation, those victims of CryptoLocker who kept their files got the chance to decrypt them without paying any money to the criminals.
I hear if you pay the fee it gives up the files to you? is it true?