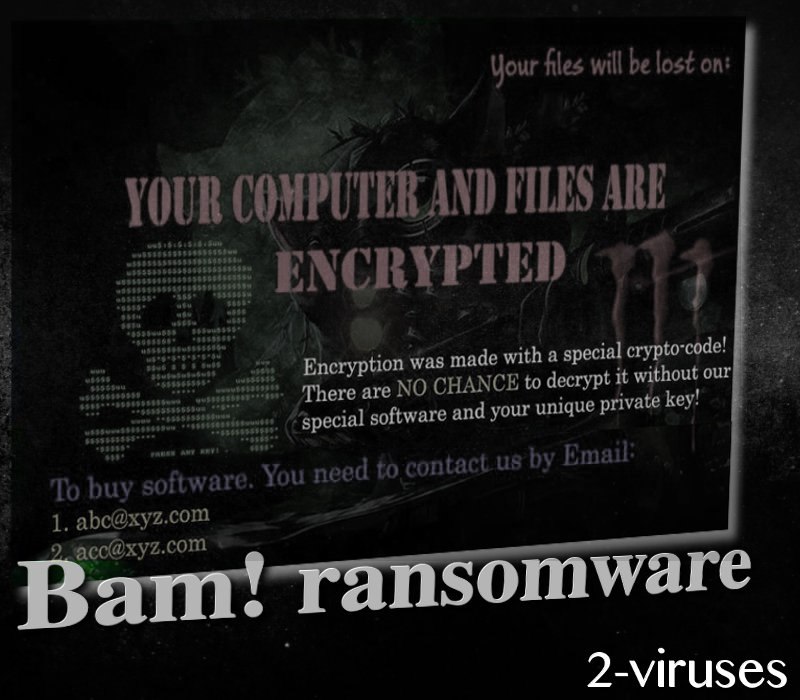
Bam! ransomware virus commenced its activity at the end of July and is known for appending .bam, extension to the digital files that become encrypted with a special crypto-code. It does not append any .txt or .html executables to get victims familiar with the terms of the release of their files. It sets an eye-stabbing background image as a desktop and displays brief letter of demands. At the top of the new background, people will see a countdown which will suggest that victims have only 24 hours to figure out a plan of action against this infection.
Investigation of this crypto-virus
Hackers are explaining that the only method to reclaim files as they were it is to contact crooks via email. [email protected] and [email protected] are the addresses that people are advised to write letters and require more information. The ransom is not identified in the ransom background: therefore, victims that are interested in paying have no choice but to contact hackers via the left contact information.
Different hackers might require differing payments, but the range from 0.01 and 1 BTC seems to be the most prevailing among infections. This means that crooks could be demanding only 27.45 US dollars or moving up to the sum of disturbing 2745.08 US dollars. Whichever the case, security researchers emphasize that paying the ransom is never the right choice.
Ransomware.exe is the main source of malicious activity and it will extract, delete and make modifications. People that analyze their operating systems might not recognize Bam! Crypto-virus immediately as it will be labeled with a tricky combination of terms. These are a couple of names that the detected ransomware could be indicated: Trojan.GenericKD.12048470, Troj.Generickd!c, Trojan/Win32.Ransom.C2054325, Trojan.Generic.DB7D856, Trojan.Ransom.Bam.
Upon its arrival in a Windows operating system, the ransomware will strategically make alterations in Registry and that will end up with the auto-execution of the payload. It will secretively intend to make changes that will presumably be irreversible, like deletion of Shadow Volume Copies. The payload is a file that was intentionally or accidentally downloaded from the Internet. It could be that it hid its true nature by posing as a respectable application. However, after it was downloaded, a person could have been requested to enable macros or to complete other allegedly-necessary action.
Discussion about avoiding ransomware and protecting your digital data
The first thing that you should consider doing is moving your files to a safe location, presumably a backup storage or another alternative that would help you reach your data anytime you might need it. For some people, his or her USB flash drive could be a very suitable place. However, it is important not to keep it plugged into your OS at all times. If a crypto-virus hits your device, the files in the USB could also be scrambled.
The impact of a ransomware is difficult to reverse. In this case, it would be best if security researchers would manage to create a free file-recovery tool, designed specifically for BAM! malware. At the time of writing this article, we did not find any information, suggesting that such a software would have been developed.
There are other methods; you could try recovering data with the recommendations we have provided below. Examine them and try them out. However, before this could be effectively done, you should eliminate a ransomware infection from your device. Manual removal of a crypto-virus could damage an operating system if done wrongly. Therefore, our alternative suggestion is to run a scan with anti-malware tools like Spyhunter.
Wish to never hear or see words “ransomware attack”? We have a couple of tips that will help you. First of all, do not open emails that immediately strike you as suspicious. It could be that your email account is being targeted by hackers that hope you will swallow the bait and download a malicious attachment. In addition, poorly protected RDP could also be a reason for a ransomware attack.
Bam Ransomware Virus quicklinks
- Investigation of this crypto-virus
- Discussion about avoiding ransomware and protecting your digital data
- Automatic Malware removal tools
- How to recover Bam! ransomware virus encrypted files and remove the virus
- Step 1. Restore system into last known good state using system restore
- 1. Reboot your computer to Safe Mode with Command Prompt:
- 2.Restore System files and settings.
- Step 4. Use Data Recovery programs to recover Bam! ransomware virus encrypted files
Automatic Malware removal tools
(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
How to recover Bam! ransomware virus encrypted files and remove the virus
Step 1. Restore system into last known good state using system restore
1. Reboot your computer to Safe Mode with Command Prompt:
for Windows 7 / Vista/ XP
- Start → Shutdown → Restart → OK.
- Press F8 key repeatedly until Advanced Boot Options window appears.
- Choose Safe Mode with Command Prompt.

for Windows 8 / 10
- Press Power at Windows login screen. Then press and hold Shift key and click Restart.

- Choose Troubleshoot → Advanced Options → Startup Settings and click Restart.
- When it loads, select Enable Safe Mode with Command Prompt from the list of Startup Settings.

2.Restore System files and settings.
- When Command Prompt mode loads, enter cd restore and press Enter.
- Then enter rstrui.exe and press Enter again.

- Click “Next” in the windows that appeared.

- Select one of the Restore Points that are available before Bam! ransomware virus has infiltrated to your system and then click “Next”.

- To start System restore click “Yes”.

Step 2. Complete removal of Bam! ransomware virus
After restoring your system, it is recommended to scan your computer with an anti-malware program, like Spyhunter and remove all malicious files related to Bam! ransomware virus. You can check other tools here.Step 3. Restore Bam! ransomware virus affected files using Shadow Volume Copies
If you do not use System Restore option on your operating system, there is a chance to use shadow copy snapshots. They store copies of your files that point of time when the system restore snapshot was created. Usually Bam! ransomware virus tries to delete all possible Shadow Volume Copies, so this methods may not work on all computers. However, it may fail to do so. Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8. There are two ways to retrieve your files via Shadow Volume Copy. You can do it using native Windows Previous Versions or via Shadow Explorer. a) Native Windows Previous Versions Right-click on an encrypted file and select Properties → Previous versions tab. Now you will see all available copies of that particular file and the time when it was stored in a Shadow Volume Copy. Choose the version of the file you want to retrieve and click Copy if you want to save it to some directory of your own, or Restore if you want to replace existing, encrypted file. If you want to see the content of file first, just click Open.
b) Shadow Explorer It is a program that can be found online for free. You can download either a full or a portable version of Shadow Explorer. Open the program. On the left top corner select the drive where the file you are looking for is a stored. You will see all folders on that drive. To retrieve a whole folder, right-click on it and select “Export”. Then choose where you want it to be stored.

Step 4. Use Data Recovery programs to recover Bam! ransomware virus encrypted files
There are several data recovery programs that might recover encrypted files as well. This does not work in all cases but you can try this:- We suggest using another PC and connect the infected hard drive as slave. It is still possible to do this on infected PC though.
- Download a data recovery program.
- Install and scan for recently deleted files.








