Have you seen an extremely alarming warning on your screen about your computer being infected with dozens of viruses? Maybe law enforcement demanding that you pay a fine? Or a random webpage demanding that you type in your username and password?
Cybercriminals use these and similar webpages to scam people. They use the powerful interactivity and multimedia capabilities of the modern web to create convincing scams and persistent attacks.
Sometimes, this results in your screen being stuck on a webpage that seemingly can’t be closed. A locked browser.
How To Fix Locked Browser Issues quicklinks
- How to fix locked browser issues and close a malicious webpage
- Close the webpage
- Close the tab
- Close the browser
- Reboot
- Prevent the webpage from opening again
- More about browser lockers
- Types of browser-locking attacks
- Example
- How malicious sites take over the browser
- Example
- The goals and dangers of malicious sites
- Example
(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
How to fix locked browser issues and close a malicious webpage
The web browser is just a program that displays webpages. To get out of a malicious site and get back control over your computer, you need to close the browser tab or the whole browser.
Normally, you can close a browser tab by pressing the X button at the top. But if that’s not possible, there are other ways, such as using keyboard shortcuts or the Task Manager/Activity Monitor program.
Close the webpage
Close the tab
When your browser is locked by a malicious webpage, you can close its tab.
If the button for that isn’t there, try pressing Esc to exit full-screen mode. Now, close the tab.
You can also use a keyboard shortcut to close the current tab. Press the keys together and let go.
- Windows: Press the Ctrl and W keys.
 Alternatively, press the Alt and F4 keys.
Alternatively, press the Alt and F4 keys. - MacOS: press the Cmd and W keys.

Close the browser
If this didn’t work, you can close your browser by bringing up the Force Quit window in macOS or the Task Manager in Windows.
- Windows: open the Task Manager window by pressing the Ctrl, Shift, and Esc keys.

- MacOS: open the Force Quit window by pressing the Cmd, Alt, and Esc keys.

Now, find your browser (Chrome, Firefox, Edge, Safari, Opera, etc.) in the list of running applications. Select it and then end it by clicking the “End task”/”Force quit” button in the lower right.
Reboot
As a last resort, you can always turn off or reboot your computer. It will be okay. The only problem is, if you were working on something and did not save, that data could disappear. Luckily, many programs have autosaving.
You can turn off your computer by pressing the power button. But it’s better to use a keyboard combination.
- Windows: press the Ctrl, Alt, and Delete buttons. Press Sign out.

- MacOS: Ctrl, Cmd, and Eject/Power. This quits all the apps and reboots the computer.

Prevent the webpage from opening again
Do not allow the same page to open. If you quit your browser, don’t let it recreate the last session.
Scan your computer with an antivirus tool – Spyhunter for Windows, Combo Cleaner for macOS, or other reliable programs. Review your Downloads folder for suspicious recent files, especially HTML files (webpages) and bat and js files (scripts).
Use anti-malware tools that offer web filters to block malicious websites. You can also use ad blockers to help you avoid malicious pop-up ads that so often lead to browser-hijacking sites.
More about browser lockers
Types of browser-locking attacks
Malicious actors, cybercriminals, and scammers deliberately create webpages that freeze your browser and lock your screen.
Here are some examples of malicious sites and what they may look like (keep in mind that these are all fake):
- Law enforcement messages about your computer being “locked”. FBI warnings about you having to pay a fine.
- Security warnings, blue screen errors, virus detections. Often, they threaten that if you turn off your computer, something bad will happen to it.
- Pages imitating Facebook, Amazon, Google, and other companies. Fake login sites.
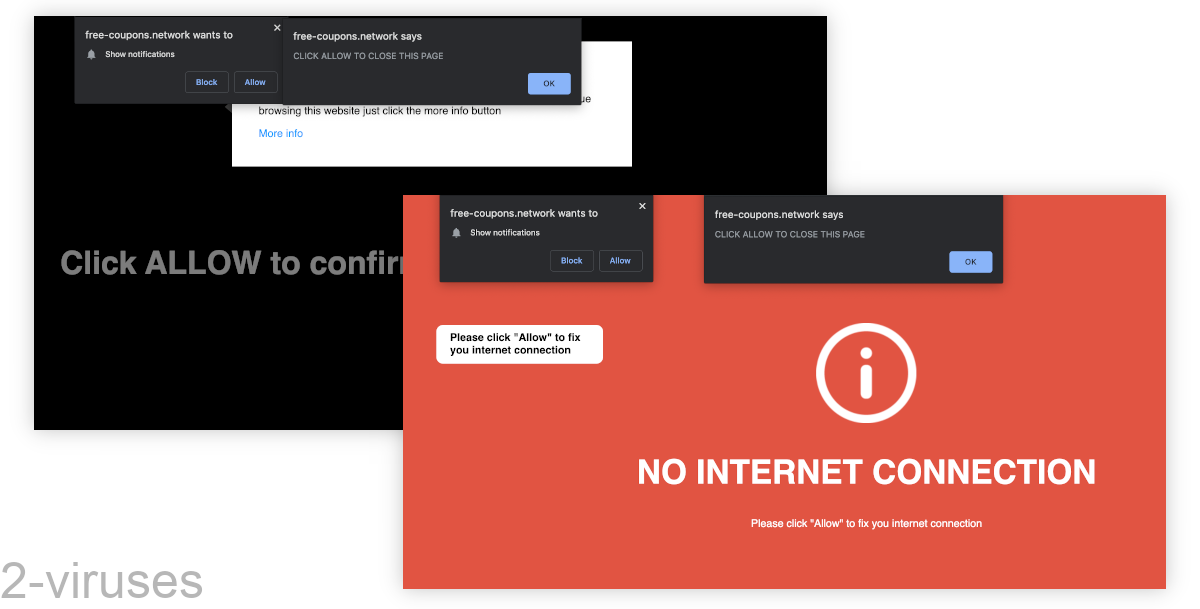
- Notification spammers that ask you to allow their notifications (“press Allow to…”).
Scammers try to impersonate someone trusted. So, malicious webpages often are made to look like a trusted environment, such as your operating system (Windows, macOS) or a famous website (Facebook).
Sometimes, there’s some scary text, like “Your Windows/iPhone/Computer is banned” or “your files will be deleted”. Baseless threats, but very stress-inducing.
Example
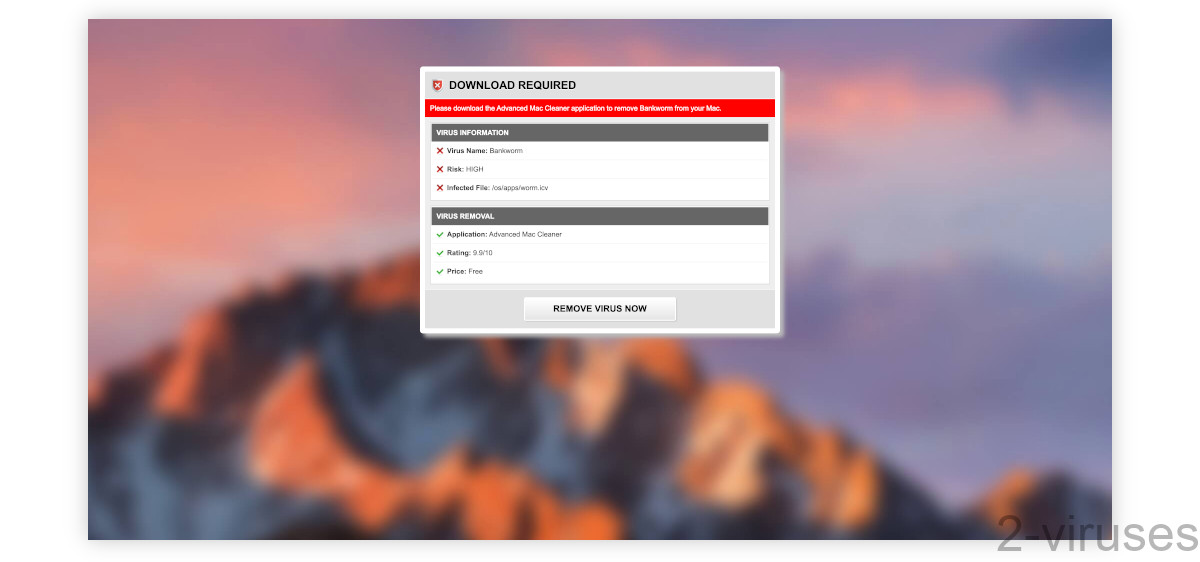
Here’s an example of a screen-locking site that is trying to look like a virus detection warning from macOS. Pressing the “Remove virus now” button causes an adware bundle to be downloaded.
How malicious sites take over the browser
Despite making it look like your computer is locked, scam webpages are contained within the web browser, within a single browser tab. And yet, they’re so difficult to close.
They use various tricks to stop people from closing them:
- Expanding to full-screen. This makes it harder to get out of the page.
- Hiding your cursor, for example, displaying it with an offset, showing a fake cursor that moves on its own, and making your mouse cursor invisible. This makes it difficult to close the webpage because you can’t be sure where you’re aiming at.
- Showing security warnings and threatening that something bad will happen if you close the page.
- Spamming pop-ups that require interaction. When you dismiss the pop-up, a new one is opened immediately. Meanwhile, no browser buttons can be pressed.
- Constantly reloading.
- Automatically download files. Scam pages sometimes download themselves onto your computer and open on their own.
Example
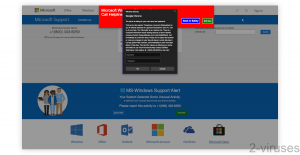
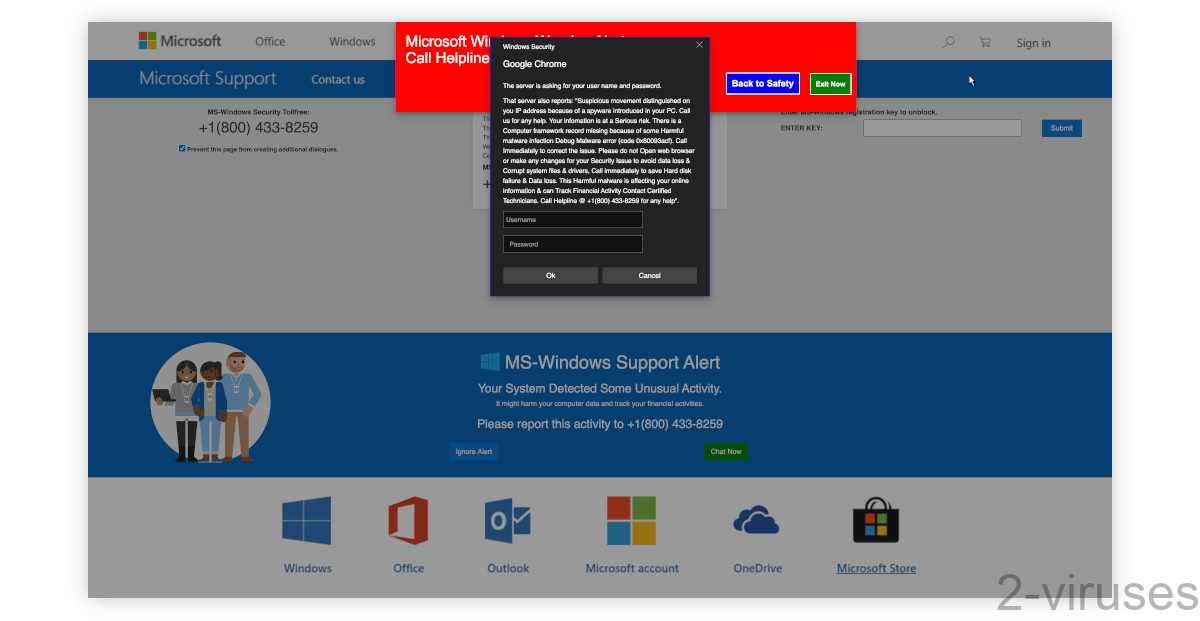
For instance, here’s a malicious site that is misusing Microsoft’s image to scare people into contacting tech support scammers. It hides my mouse cursor while showing a fake one. It also expands to full screen and repeatedly shows a request for my username and password. It reloads itself periodically. All of that is done to make sure that the page remains open and covers the whole screen.
The goals and dangers of malicious sites
Malicious websites are made to get people to download malicious files, to reveal personal information, and to give sites access to their browser settings. Ultimately, scammers are using them to make money.
Here’s how they do it:
- Fleeceware and scareware programs. Fake antivirus software that shows security warnings even when nothing is wrong with your computer. They cost a lot, usually are subscription-based, and they’re often hard to cancel.
- Tech support scams. They seek to get you to buy the above-mentioned useless security programs, as well as pay for tech support. Tech support scammers convince people to install remote access software and then steal files that they suspect contain sensitive information.
- Phishing and subscription scams. People’s stolen personal details are used to sign them up for subscriptions and charge them subscription fees. Hard or impossible to cancel.
- Notification spammers make money by displaying ads. Easy to cancel by changing notification settings.
These pages try to cause fear and excitement. They often include timers that are counting down, implying that something bad will happen if the timer runs out. There might be audio of generated speech reading out your warning, or an alarm sound which can cause a lot of urgency and discomfort.
Example
For example, these notification hijackers work as advertising networks. They use notifications to spam people with pop-up ads.
 Alternatively, press the Alt and F4 keys.
Alternatively, press the Alt and F4 keys.






